As consumers tend to create weak passwords and repurpose them across digital accounts, the traditional method of password-based authentication is vulnerable to cyberattacks.
Security tokens have emerged as a popular alternative to using passwords as they add an additional layer of authentication and enhance security. They prevent the use of stolen or compromised passwords for account takeover attempts by bad actors. Further, using tokens, security teams can exercise greater control over user actions and transactions.
The tokenization market is growing rapidly and is projected to reach $5.6 billion by 20251. This swift adoption is fueled by the increasing willingness of the consumers to use tokens while making purchases. According to a recent survey, 63% of the respondents consider token-based payments secure2.
Attackers compromising authentication or identification tokens to gain unauthorized access to user accounts or sensitive data is called token cracking. Bad actors usually use brute force methods to crack the tokens used for multi-factor authentication, which allows them to impersonate genuine users and take over consumers’ digital accounts.
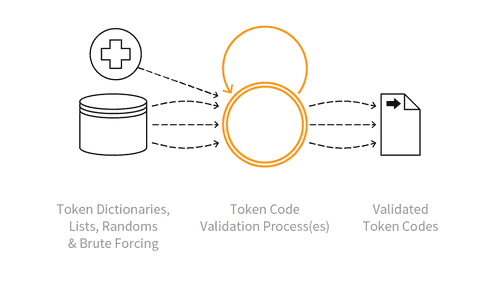
What is a token in cybersecurity?
A security token may be a physical device or a piece of information that a user must input to access a desired system. A security token facilitates the flow of data between the user and the system to verify users and allow or refuse access.
Security tokens are typically used in situations where a higher level of security is required to protect sensitive information or resources. The use of a security token helps to prevent unauthorized access to a system or network, by requiring an additional layer of authentication beyond just a username and password.
Types of tokens
Depending on their unique needs, businesses can customize their token setup with features such as password protection of data, use of biometric data along with authentication systems, and including safety features to protect data from exposure and theft. They may choose from or use a combination of the following token types:
Connected tokens:
A physical token such as a smartcard is an example of a connected token, which must be inserted into a system to be used. Once the token is inserted into the device, the system automatically reads the users’ authentication information.
Disconnected tokens:
True to their name, disconnected tokens don’t need to be inserted into a device. Instead, users must input the code that the token generates.
Contactless tokens:
These tokens allow devices to connect with each other through wireless systems – such as through Bluetooth – to authenticate user information. Contactless tokens eliminate the need to insert a physical token or use a code to access a system.
NFC tokens:
Near-field Communication (NFC) tokens can be used in both connected and disconnected states.
Single sign-on software tokens:
These tokens have users’ passwords already stored on them which eliminates the need for users to remember their passwords. These tokens often feature a cryptographic hash of the password so that the password remains protected even if the token is cracked.
Programmable tokens:
These tokens can be used as a replacement for mobile apps or as a backup.
How do security tokens work?
The bedrock of security tokens is the technology where a device generates a random code and shares it in an encrypted form with a server that stores a user’s authentication information. The server sends an encrypted response that can be decrypted only by the device. This device can be used for repeated authentication without the need to store username and password information on the server, thereby elevating security.
The process of using a security token for authentication typically involves several steps. First, the user enters their username and password to access the system or resource they are trying to reach. Then, the security token generates a random code that is unique to that particular authentication session. This code is sent to the server in an encrypted form along with the user's authentication information.
The server receives the encrypted code and authentication information and processes them to verify the user's identity. If the user is authenticated, the server generates an encrypted response that contains a message indicating that the user has been authenticated. This response is sent back to the security token, which is able to decrypt the message using its own private key.
Once the security token has decrypted the message and verified that the user has been authenticated, it can then be used for repeated authentication without the need to store username and password information on the server. This helps to elevate security, as it reduces the risk of a data breach or other security incident that could compromise sensitive user information.
Benefits of using security tokens
Use of weak and repurposed passwords make them a grave security challenge, as attackers can crack them easily. Further, forgotten passwords can lock users out of their accounts causing big problems. Security tokens are a better alternative to passwords, as they can be used as an additional layer of security (as part of multifactor authentication) and even replace passwords.
Security tokens replace sensitive financial and personal data such as identity documents and legal documents to provide better protection against data theft. They extend beyond the realm of cybersecurity and are even used across industries such as real estate, asset management, contract management etc by converting assets into their digital equivalents.
Can tokens be cracked?
It is possible to crack a token. Each one is assigned a private key, which is held by the owner or custodian appointed by the owner. The token and number itself could be hacked, but it would take years of attempts to be successful because of the encryption methods.
While security tokens are generally considered to be a secure method of authentication, they are not completely immune to attacks. One common attack that can be used against security tokens is known as a Man-in-the-Middle (MITM) attack. In a MITM attack, an attacker intercepts the communication between the security token and the server, and then attempts to manipulate or modify the data being transmitted.
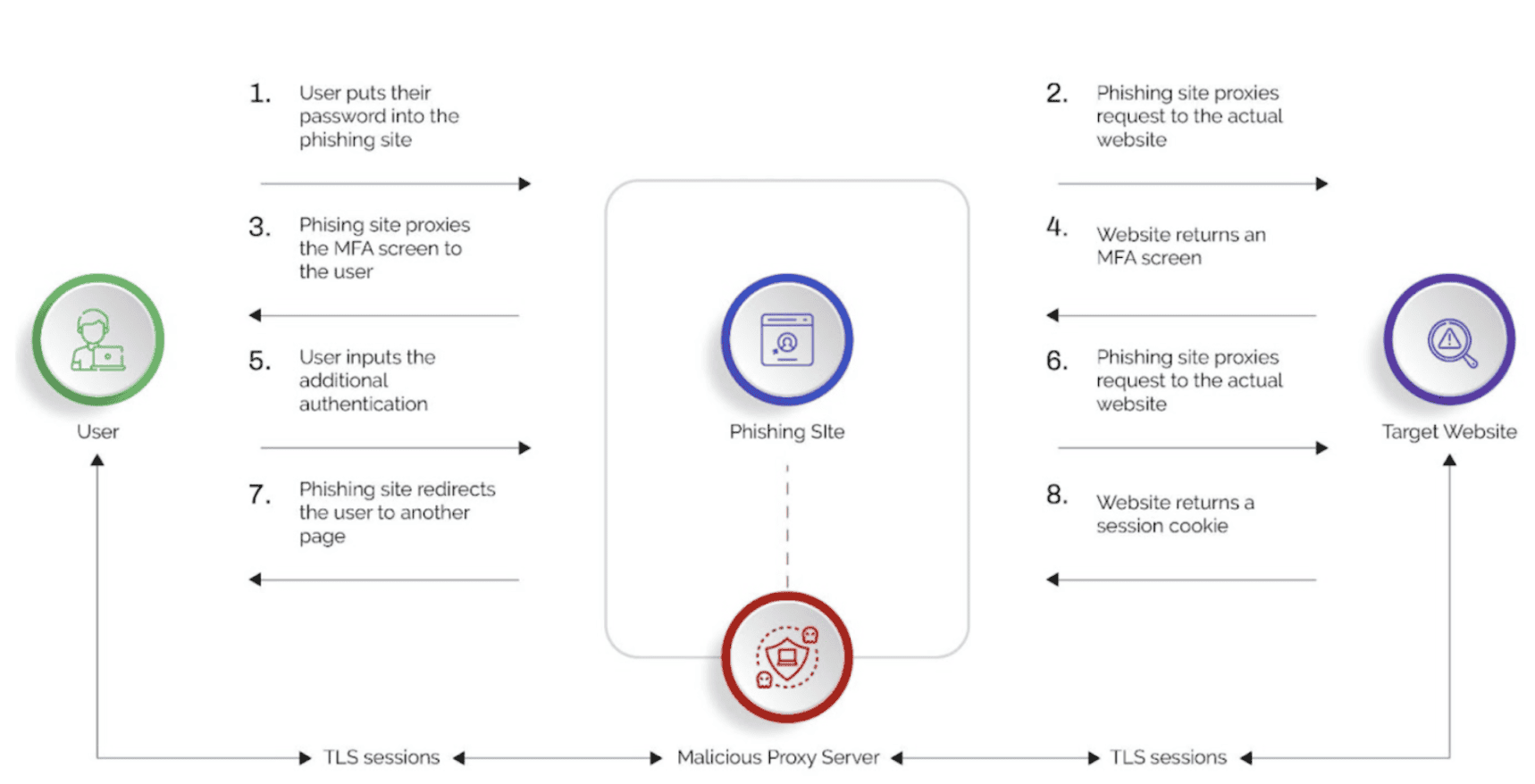
To prevent these types of attacks, it is important to use security tokens that generate dynamic codes that change over time. Additionally, it is important to use strong encryption methods to protect the transmission of data between the security token and the server. It is also recommended to use multi-factor authentication (MFA) to provide an additional layer of security to authentication processes.
Overall, while security tokens are generally considered to be a secure method of authentication, it is important to be aware of the potential risks and to take steps to mitigate these risks. By following best practices for security and using the latest technologies, organizations can ensure that their authentication processes remain secure and protected against attacks.
Why token cracking is dangerous
As more and more applications use token-based authentication, it has caught the eye of the actors who crack these tokens to compromise user accounts and use them for malicious activities. Although security tokens are designed to secure data, token cracking is possible and can be done in under 15 minutes3!
Token cracking can pose serious challenges to businesses, as they can lead to compromised accounts that can be used for a plethora of criminal activities.
Token cracking is dangerous because compromised tokens can pose a much greater security risk as compared to compromised passwords. For instance, when a user tries to log into a service after completing multifactor authentication, they are assigned an authentication token. If an attacker is able to crack this token successfully, they can easily pose as the compromised user and won’t need to make additional effort to bypass the MFA.
Common token cracking attacks
Because tokens are live only for a short duration, attackers typically try to access them before they expire. Some of the common ways bad actors implement attacks for token cracking include:
- Man-in-the-middle (MITM) attacks: where they intercept the data traversing between the server and the user’s connection. Since data is stolen in near real-time, bad actors can access even the most short-lived tokens much before they expire.
- Brute force: Where they test multiple stolen passwords and tokens against accounts.
- Breach of codes: Where attackers develop methods to exploit cryptographic flaws to extract secret keys.
- Loss or theft: When physical tokens are lost or stolen, the data stored on them is susceptible to misuse.
- Social engineering: Attackers may trick users into sharing their personal information to try and gain access.
- Malware: Using malware, bad actors can extract tokens from an infected device.
Tools used in token cracking
There are several techniques that attackers use to crack tokens. In addition to the attack types mentioned above, bad actors exploit the cryptographic flaws to extract sensitive keys from commonly used cryptographic devices.
They also use HTTP requests and intercepting proxy tools to read the full explicit response, which is then used for token cracking. These proxy tools allow attackers to tweak their requests and change the tokens to observe how it affects the application. The commonly used intercepting proxy tools are Burp Suite and ZAP, whereas POSTMan is popular for APIs.
How to detect token cracking?
Token cracking can be a dangerous proposition for businesses, especially financial service providers, that would be exposed to a heightened threat of impersonation and financial crimes. It is, therefore, essential for businesses to detect early signs of token cracking and take timely corrective measures to prevent token cracking attempts.
With early detection of token cracking attempts, businesses can improve their security posture and take proactive steps to protect their business and customer interests. Machine learning toolkits can be used to spot anomalous patterns – such as unusual increase in the number of requests from a user – and make timely interventions such as rejecting approval requests, revoking tokens, and asking users to change their passwords.
How can businesses fight token cracking?
Token cracking can expose the affected business to impersonation attacks. To mitigate the effects of a token cracking attack, businesses can take the following steps:
- Invalidate compromised tokens: If unusual behavioral patterns are detected - such as an unusual increase in user requests within a short duration - it is possible that a bad actor may have been able to crack a token. In such an instance, it is essential to revoke the tokens generated to prevent attackers from making further progress.
- Change client-side password: In case of a suspected token cracking attempt, web and app users must be asked to change their passwords with immediate effect. Using some form of multi-factor authentication to effect this password change will help improve security.
- Discover how the attacker accessed the token, from client-side or server side: Use digital intelligence to ascertain how the attackers accessed the token. Possible scenarios to be investigated include checking if the user’s phone was stolen, the user tried to access the service through an infected device, or was the token stolen from the business network.
- Work with a seasoned vendor with strong credentials in preventing token cracking: Partner with a vendor that has the required expertise to detect token cracking attempts early.
Why work with Arkose labs to fight token cracking?
Arkose Labs provides comprehensive protection against token cracking by utilizing advanced data analysis techniques to accurately distinguish between genuine users and bad actors. This ensures our customers enjoy long-term protection while maintaining the exceptional user experience we aim to provide.
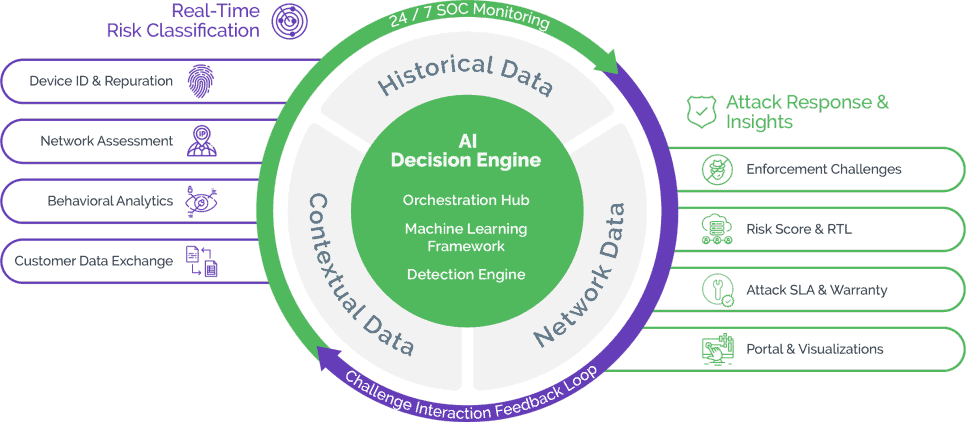
Committed to helping businesses protect their data and revenues from evolving and complex attacks, Arkose Labs offers user-centric attack remediation through active monitoring and optimization of their partners' traffic. We also provide valuable insights and raw signals that empower security teams to effectively combat evolving attack tactics and ensure future-proof protection.







