- SolutionsUSE CASES
Protect users’ accounts
Slash fraud losses
Prevent spam and bots
International Revenue Share Fraud
Stop fake account registrations
Stop malicious scraping
Secure API traffic
Banking & fintech accounts

reCAPTCHA Alternative: Why 10 companies switched from reCAPTCHA to Arkose Labs to win against bots.

Bad Bots and Beyond: 2023 State of the Threat
With Arkose Labs’ 2023 State of the Threat Report, you will find extensive information and best practices around
USE CASESProtect users’ accounts
Slash fraud losses
Stop fake account registrations
International Revenue Share Fraud
Stop malicious scraping
Banking & fintech accounts
Secure API traffic
INDUSTRIESProtect users’ accounts
Banking & fintech accounts
Stop malicious scraping
Stop fake account registrations
International Revenue Share Fraud
Secure API traffic
Prevent spam and bots
Banking & fintech accounts
Slash fraud losses
- ProductsPRODUCTS
Stop bot attacks by driving up adversarial effort and cost
Assess email risk at bot scale
Detect and block reverse-proxy phishing attacks
Unique, customizable & performance improvement challenges
WHY ARKOSE LABSSabotage attacker’s ROI
Industry-first SLA guarantee
Industry-first SLA guarantee
Industry-first SLA guarantee
SERVICES & SUPPORTProfessional services expertise
Fast, reliable support
Flexible open platform
- Industries
- ResourcesINSIGHTS
Read our thought leadership blogs
Customer success stories
Videos from the Arkose Labs team
EVENTSEDUCATIONExpert Guide to Account & Identity Fraud
THOUGHT LEADERSHIPData-driven research reports
Fraud prevention guides
Fraud thought leadership
Learn how Arkose Labs prevents fraud
View all Arkose Labs content
INSIGHTSEVENTSEDUCATIONTHOUGHT LEADERSHIP - Company
- Customers
Arkose Labs Undermines the Economic Incentive Behind Attacks
Cybercrime will continue to thrive as long as there is a potential for profit. Arkose Labs tackles this issue by disrupting an attackers' return on investment (ROI), rendering it financially unviable for them to target companies within our network. This approach marks a significant shift from merely preventing attacks to actively deterring them.
Global finance companies trust Arkose Labs to detect and deter attacks at user authentication touchpoints, allowing them to save money on costly fraud losses and improve overall ROI. Rooting out crime early means companies are able to strengthen relationships with customers with an increasingly secure financial platform—all without sacrificing a positive user experience or reducing operational costs.
Protection for the Most Targeted User Touchpoints

Account Takeovers
Protect user accounts against credential stuffing and account takeovers, which put financial accounts at risk.
Application Fraud
Stop attackers from leveraging stolen and synthetic credentials to set up fake accounts.

Advanced Persistent Bots
Most robust protection against advanced bots that bypass traditional defenses to blend in with user traffic.

Bonus Abuse
Secure user promotions from abuse by fake users, such as a cash bonus for signing up to a new card or a fintech platform.

Micro-Deposits & Payment Fraud
Protect any user action within web and mobile applications, for example adding linked accounts that are abused for micro-deposit fraud.

API Abuse
Stop attacks on APIs from advanced bots emulating clients and impersonating legitimate users.

Bots and API Abuse
Advanced bots are consistently bypassing traditional bot defenses, attempting to blend in with traffic at logins, account sign-ups or targeting APIs directly.
Arkose Labs Attack Deterrence Platform
Arkose Labs delivers proactive bot prevention and account security by undermining the economic drivers behind attacks. Our AI-powered platform defeats persistent bots and coordinated human attacks on the most targeted user touchpoints—websites and apps. Invisible risk assessments allow good users to pass through seamlessly and without friction. High-risk traffic is triaged for active attack response using the strongest CAPTCHA in the business, Arkose MatchKey, which deters attackers while also delivering a more secure experience for good users.
This cost-effective solution eliminates the need for hardware, software, and personnel, allowing businesses to save both time and money. Moreover, the automated solutions offered by Arkose Labs reduce costs associated with chargebacks and help protect businesses from financial losses due to cybercrime. With 20% of customers being Fortune 500 companies, our solutions deliver a strong ROI by improving operational efficiency and reducing the manual effort required to manage security operations.
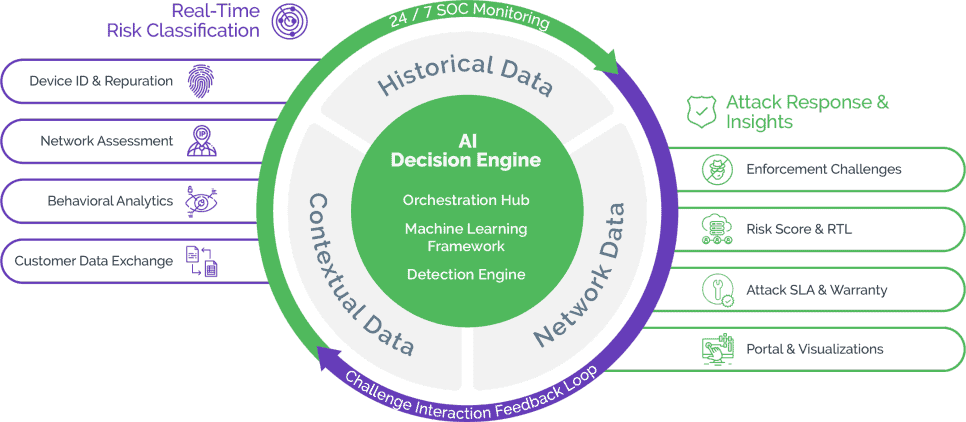
Arkose Decision Engine: Big Data & Advanced Analytics
The Arkose Labs platform is centered around an AI-driven decision engine that processes real-time signals with our deep historical intelligence to orchestrate a targeted attack response. From real-time and challenge interaction data, ensuring that genuine users are able to pass seamlessly whilst detecting evolving attack techniques.
Machine Learning Framework
Embedded machine learning assesses anomalies from real-time signals, historical attack patterns, and attacks across the Arkose Labs Global Network of customers. Our AI-driven platform evolves models in real-time to rapidly adapt to evolving attacks.
Attack Pattern Correlation
Arkose Labs takes a storytelling approach to cyberattacks. Rules and patterning correlates fraud tell-tale signals, velocity and distance, and historical customer behavior to validate whether or not a user’s story checks out.
Response Orchestration
Combining real-time insights with the risk profile of the user, our dynamic defense determines the appropriate step-up challenges for the risk profile. The orchestration hub is supported by a behind-the-scenes team monitoring traffic flow and attack patterns to adjust telltales and enforcement challenges accordingly.
Arkose Global Network
Arkose Labs takes a consortium approach to cybercrime, leveraging anonymized threat intelligence from over 4.1B IP addresses across a vast global network of customers each year. From day 1, Arkose Labs customers benefit from a database of over 4,000 tell-tale attack patterns.
Arkose Bot Manager: Attack Response & Deterrence
Arkose Bot Manager offers an adaptive approach to attack prevention and account security. Our technology combines highly-transparent detection with targeted attack response to catch fraud early in the customer journey, without impacting good users.
Our AI-powered platform combines defense-in-depth detection with dynamic attack response to navigate unclear trust signals. When traffic is flagged as suspicious, the Arkose Labs’ platform provides secondary screening and targeted attack response that break the economics of bot and human-driven attacks. Arkose MatchKey collects user interaction data to further validate the user’s intention and deliver truth data back to the decision engine. As a result, fraud and security teams gain the advanced detection power, risk insights, and option for user-friendly enforcement they need to go from bot mitigation to attack deterrence.
Device ID & Reputation
Deep device forensics is used to fingerprint devices based on its characteristics and integrity over time. Works for desktop, mobile, smart TVs, and gaming consoles.
Network & IP Assessment
Arkose Labs combines a proprietary IP scoring system with 3rd party reputation lists to monitor for abnormalities, such as spoofing location or using cheap IP addresses.
User Behavioral Analysis
Behavioral biometrics such as keystroke, gyroscope, and page familiarity are used to distinguish good user behavior from automation and bad human behavior.
Customer Data Exchange
Our flexible APIs can ingest data from proprietary or third-party risk engines to improve risk assessment accuracy and inform the usage of Arkose Labs’ enforcement challenge.
Real-Time Bot Detection
Catch Evolving Attacks with Greater Transparency
Today, bad actors have endless tools and resources to expertly mimic good users and circumvent defenses. Our multi-layered detection aggregates real-time device, network, and behavioral signals on a customer workflow to spot hidden signs of bot and human-driven attacks, such as device and location spoofing.
- Multi-layered device, IP, and behavioral detection
- Access to 70+ risk attributes to enrich existing models
- ML decisioning driven by 150+ global attack signatures
- 24/7 SOC threat analysis and tuning
Bots Defense
Suspected bot are presented with a deep bench of challenges that machines have no idea how to solve. No off-the-shelf technology can be used to solve our challenges, forcing fraudsters to continuously build AI and waste time and resources.
Human Attacker Challenges
Arkose Enforce presents time-absorbing challenges when attackers use human labor to circumvent anti-bot technology. These challenges deliberately waste the time and resources of the fraud farm, making it unprofitable.
Risk Score & Real Time Logging
An open API platform enables customers to ingest honest and transparent data directly from Arkose Labs. With our real time logging API, customers can access insights from all sessions to enhance existing risk models.
Attack SLA & Warranty
Arkose Enforce deploys a foolproof acid test to stop bots in their tracks. Arkose Labs is so effective against even the most persistent bots, we stand by our customers with a contractually guaranteed attack SLA and an industry-first credential stuffing warranty.
Solving the False Positive vs False Negative Conundrum
The combination of risk decisioning and targeted enforcement allows platforms to be more aggressive against persistent attacks without fear of impacting good users. In the event of a false positive, Arkose Labs user-centric secondary screening diminishes the risk of good users being blocked or impacting conversion rates.
High-risk traffic is challenged, never blocked
Flagged good users easily solve challenges on the first try
Improve user experience by reducing reliance on MFA
Invisible screening means customers rarely see challenges
Challenge interaction data trains the decision engine
The Arkose Advantage
Guaranteed Efficacy
Powerful protection backed by commercial assurance and industry-first limited warranty
Managed Services
Solution supported by a 24x7 SOC and service team delivering Industry-specific and actionable attack insights
Privacy Friendly
Unparalleled accuracy without compromising data protection or compliance
Early Detection
AI-driven platform with real-time risk assessment detects and mitigates fraud attempts in early stages
Fast Results
New customers will see results within days, not weeks or months
Arkose in Action

Fintech Neobank Beats ATOs
One of the world’s most prominent fintech firms was targeted by bots executing credential stuffing attacks at scale. Successful attacks lead to the draining of customer funds and poor user experience.
Attack Impact
- High repayment costs as a result of ATOs
Arkose Labs Result
- 75% reduction in ATO attempts
- Slashed compromised account costs, previously hitting $100,000 per week
- Resources saved from reduction in resetting credentials on compromised accounts
- Downstream cost savings and a better ROI

Global Bank Protects Logins and Stops Application Fraud
The client is one of the largest global banks, with millions of retail customers around the world and heavily targeted by loan application fraud and ATO attacks.
Attack Impact
- Threatened customer account security due to financial and identity theft
- Mass automated attacks became mass revenue loss with having to repay stolen customer funds
Arkose Labs Result
- Proven superiority in stopping automated attacks
- Improved user experience versus reCAPTCHA approach
- Downstream cost savings and a better ROI

Blackhawk Network Puts an End to Carding
Blackhawk Network is a rapidly growing payment company with innovative solutions that enable gift card use in the digital realm. It is trusted by retailers and consumers alike.
Attack Impact
- Fraudsters would test stolen gift cards and prepaid cards to drain the remaining balances leaving the company to repay the victims of stolen cards.
- Other bot and human-driven attacks on their website caused a poor user experience.
Arkose Labs Result
- 98% reduction in bot attacks
- 60% reduction in human-driven fraud
- Downstream cost savings and a better ROI
Book a Meeting
Meet with an account security expert today!






