- Fake accounts was the #1 attack vector, monetizing promos and free trials
- Bot traffic increased by 25% from Q4 2021
- 40% of attacks from Asia targeted tech companies

One thing is certain: The ROI for cyberattacks is greater than ever in 2022. The digitalization of our lives and work means bad actors can attack companies and threaten consumer trust long before a transaction takes place.
Meanwhile, the automated fraud ecosystem grows daily as new tools and resources are created to reduce the barrier to entry for sophisticated bot attacks and abuse schemes.
Catching evolving attacks early requires deeper insight and intel into the tactics and financial motivations of cybercriminals.
Each quarter, Arkose Labs analyzes billions of sessions to uncover the latest attack patterns seen on the most targeted user touch points, across our global network.
This report reveals the top attack trends from Q1 2022.






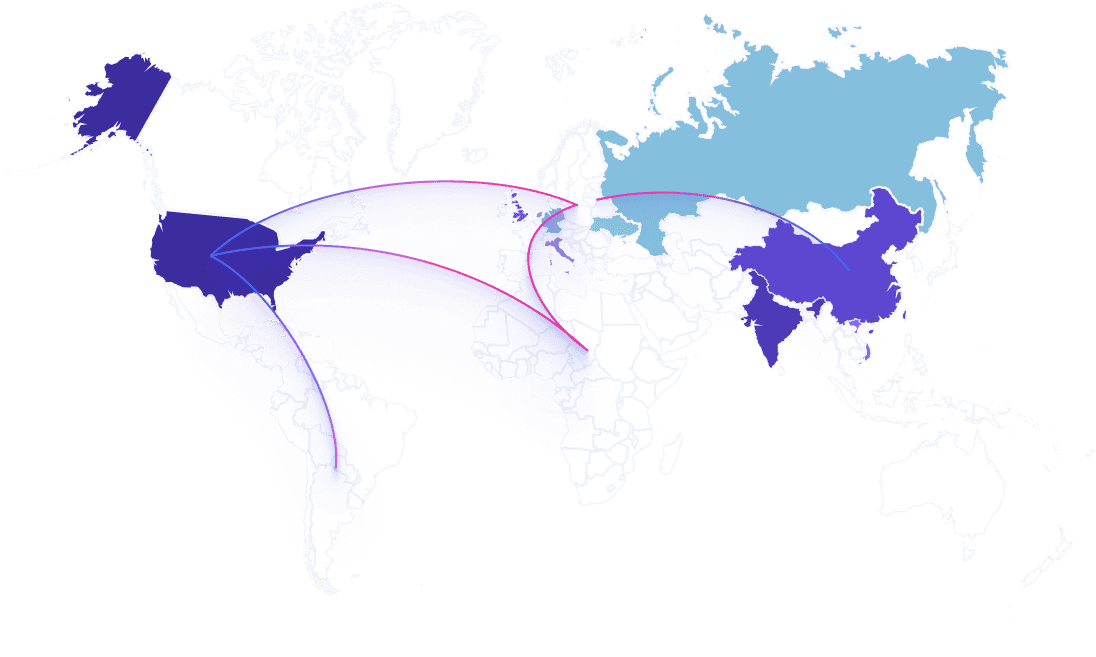
The top 5 attacking countries contributed over 60% of all attacks in Q1. Attack patterns differ in each region because of varying incentive levels due to differences in wages, cost of labor, and comparative currency values.

It no longer takes years of mastery to be an effective cybercriminal. Since the pandemic, the cybercrime workforce has exploded, thanks to the vast information sharing on the dark web and ROI opportunity for Rookie Criminals and Master Fraudsters alike.
Skilled cybercriminals use marketplaces and messaging platforms to promote their own personal fraud business, recommend attack tools and techniques, and offer free step-by-step guides for rookie cybercriminals to quickly become masters at their game.
“
We estimate there has been a 10-fold increase in people taking up fraud as a career since 2019 because of the wealth creating opportunities presented.
Brett Johnson
Chief Criminal Officer
Arkose Labs

93%of attacks are bot-driven

7%of attacks are human-driven
Bot attacks can overwhelm workflows with a single high volume attack, with peak attack periods being up to 2.5x normal traffic volume across the global network.
Human-led attacks are low-and-slow, allowing attackers to consistently target a platform while staying under the radar.
Hybrid attacks are increasingly common for persistent attackers. They start with intelligent bots, then switch to click farms when bots are deterred.


As reported by IC3, many of the most costly cybercrimes start with credentials being stolen or a fake account being created. The growing prevalence of fake account attacks reflects the lucrative nature of romance scams, while account takeovers continue to be an attacker favorite for the multitude of ways they can be used for profit. Protecting consumers and preventing fraud losses requires stronger security technology that can detect malicious activity where it originates—on login and registration workflows. Implementing such technology can lead to significant cost savings and improved ROI, allowing businesses to maintain security while also optimizing their operations.
A major US fintech company experienced 20x growth in one year. This massive popularity attracted cybercriminals, who began attacking on multiple fronts.
Attackers were executing ATOs at scale and creating fake new accounts to then send phishing messages to users. This caused poor user experience and customer financial losses, and overwhelmed fraud and security teams.
Arkose Detect was implemented on the customer’s web and mobile flows to classify traffic risk and determine the appropriate response. Arkose Labs shared detection data with the customer to enhance their internal models.
increase in login and registration attacks in 2021
Attack trends in 2021 revealed the critical need for stronger security at the account level. ATOs and fake accounts can be profitable on their own, while also creating high monetization potential for downstream spam and abuse.
more complexity in attack signatures
Bots are increasingly sophisticated, able to mimic human behavior with a high degree of accuracy. The number of data points that need to be collected, reviewed, and correlated to form a single attack signature makes it harder to detect them.
percentage of traffic consumed by a single attack
Businesses need to be adaptable to detect and mitigate high-velocity attacks in and out of peak season that can unexpectedly overwhelm servers and security teams. Having an effective and robust cybersecurity strategy in place can help reduce costs associated with downtime and lost business, while also improving ROI for the business. With the right technology and processes in place, enterprises today can stay one step ahead of malicious actors and ensure their systems remain secure.
increase in attacks targeting metaverse pioneers over Q4 2021
Attackers are going to great lengths to abuse metaverse communication channels, leveraging click farms to feign legitimacy. Insights from our global network show that scams, microtransaction abuse, and unfair play are threats to monitor as the metaverse develops.