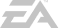- SolutionsUSE CASES
Protect users’ accounts
Slash fraud losses
Prevent spam and bots
International Revenue Share Fraud
Stop fake account registrations
Stop malicious scraping
Secure API traffic
Banking & fintech accounts

reCAPTCHA Alternative: Why 10 companies switched from reCAPTCHA to Arkose Labs to win against bots.

Bad Bots and Beyond: 2023 State of the Threat
With Arkose Labs’ 2023 State of the Threat Report, you will find extensive information and best practices around
USE CASESProtect users’ accounts
Slash fraud losses
Stop fake account registrations
International Revenue Share Fraud
Stop malicious scraping
Banking & fintech accounts
Secure API traffic
INDUSTRIESProtect users’ accounts
Banking & fintech accounts
Stop malicious scraping
Stop fake account registrations
International Revenue Share Fraud
Secure API traffic
Prevent spam and bots
Banking & fintech accounts
Slash fraud losses
- ProductsPRODUCTS
Stop bot attacks by driving up adversarial effort and cost
Assess email risk at bot scale
Detect and block reverse-proxy phishing attacks
Unique, customizable & performance improvement challenges
WHY ARKOSE LABSSabotage attacker’s ROI
Industry-first SLA guarantee
Industry-first SLA guarantee
Industry-first SLA guarantee
SERVICES & SUPPORTProfessional services expertise
Fast, reliable support
Flexible open platform
- Industries
- ResourcesINSIGHTS
Read our thought leadership blogs
Customer success stories
Videos from the Arkose Labs team
EVENTSEDUCATIONExpert Guide to Account & Identity Fraud
THOUGHT LEADERSHIPData-driven research reports
Fraud prevention guides
Fraud thought leadership
Learn how Arkose Labs prevents fraud
View all Arkose Labs content
INSIGHTSEVENTSEDUCATIONTHOUGHT LEADERSHIP - Company
- Customers
Stop Potent, Next-Generation Phishing Attacks

Phishing attacks continue to be bad actors’ go-to technique to steal user credentials and personal information. Unfortunately, phishing attacks have become more potent in recent years with the introduction of sophisticated platforms that evade traditional defenses. This new breed of phishing methods, including cybercrime-as-a-service platforms like EvilProxy and Caffeine Proxy, make it extremely difficult to detect and mitigate attacks. Arkose Phishing Protection detects, alerts, and blocks dangerous man-in-the-middle (MITM) and reverse-proxy phishing attack campaigns and prevents leak of login and MFA credentials.
- Detect reverse-proxy phishing attacks in real time
- Protect users and block credential theft
- Prevent interception of MFA/2FA codes
- Warn users with customized alerts
What Is Reverse-Proxy Phishing?
When phishing web sites disguised as legitimate login pages are combined with reverse proxy servers, an attacker acts as an “Man in the Middle” (MITM), also known as adversary in the middle (AITM), between the phishing site and the actual website. This sophisticated attack lets the attacker intercept and redirect traffic from the legitimate website to the fake one, steal credentials and other data, and work around barriers to account takeovers such as multi-factor authentication (MFA/2FA).
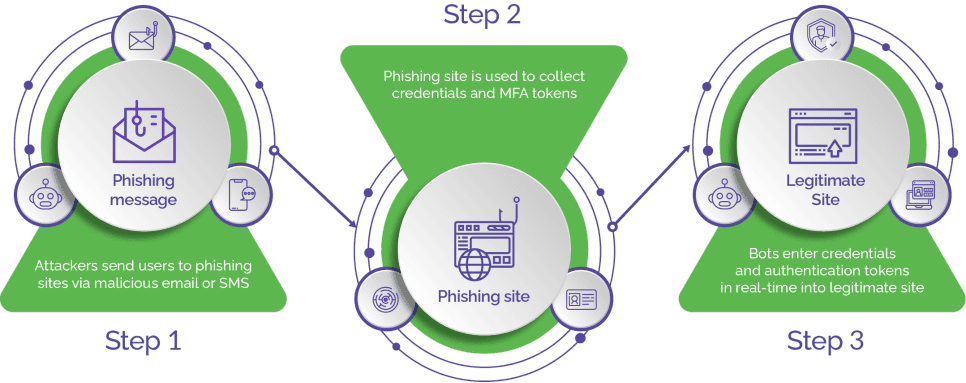
Block AITM Attacks That Hijack Logins and Bypass MFA
Arkose Phishing Protection stops reverse-proxy phishing attacks and prevents theft of login and MFA credentials, while providing the configurability and intelligence product security teams require to protect their applications and users. Key capabilities include:
- Real-time detection of reverse-proxy phishing attacks using client- and server-side signatures
- Managed phishing detection rulesets
- Hostname allow and deny lists
- Immediate end-user warning message
- Support for both active interception and monitor-only modes
- No additional integration points required
- Visibility and reporting in Session Explorer of the Arkose Command Center
Powered by the Most Effective Anti-Bot Platform
Arkose Phishing Protection builds on the unmatched bot detection and mitigation technology of Arkose Bot Manager to identify and block reverse-proxy phishing attempts in real time. Our unique visibility into server and client allows multi-layered detection aggregates device, network, and behavioral signals on critical user flows to spot hidden signs of bot and human-driven attacks.
- Multi-layered device, IP, and behavioral detection
- Access to 140+ risk attributes to enrich existing models
- ML decisioning driven by global and customer-specific attack signatures
- 24/7 SOC threat analysis and tuning

Based on results of early-access customers
“One Arkose Phishing Protection customer has flagged 175,000 reverse-proxy phishing sessions during initial deployment. The solution blocked 40 previously undetected phishing domains within a week of activation.”