We've recently introduced new features to streamline user experiences and strengthen your platform’s resilience against attacks, with more sophisticated detection signals and improved mitigation strategies. Here’s a quick rundown of what’s new and how these updates can help protect your business.
Arkose Device ID
Arkose Device ID is a device identification system designed to strengthen fraud detection and prevention while supporting a smoother user experience across key actions like registration, login, and payments. It offers a low-friction approach to enhance the security across your platform while looking after legitimate users. By combining Stateless (real-time telemetry and fingerprint aggregation) and Stateful (a persistent, unique identifier placed on the device via cookie) methods, Arkose Device ID provides a reliable and durable solution for device identification.
Arkose Labs’ device identification integrates session-based risk data, unique identifiers, and anti-spoofing capabilities to track devices accurately, so you can distinguish genuine users from bots and malicious actors. This layered approach between detection, identification and mitigation redefines and sets a new standard in the market.

To learn more about Arkose Device ID and how it strengthens your device identification and risk strategy, visit our dedicated announcement blog.
Multi-Dimensional Velocity Detection
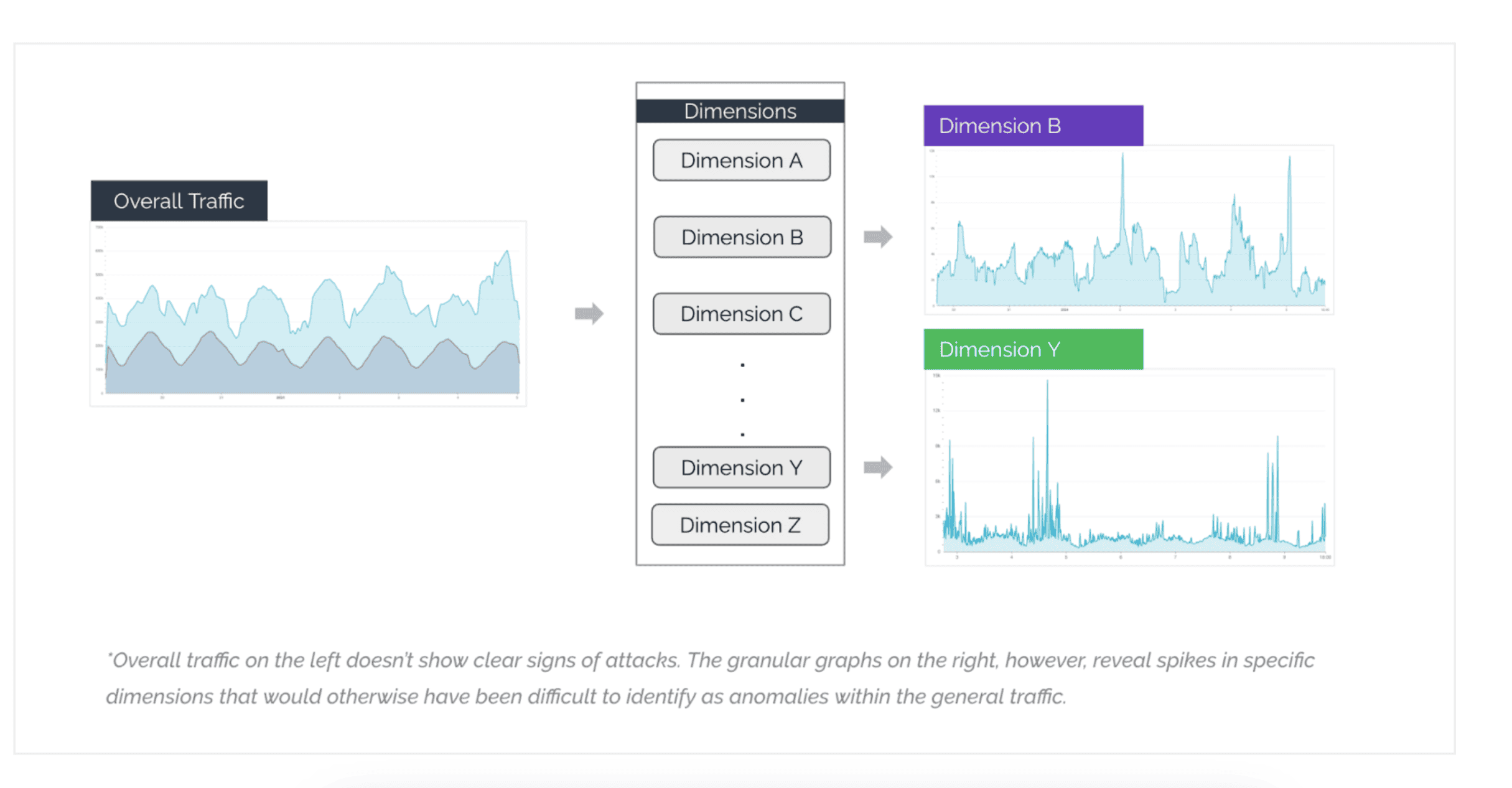
Detecting and distinguishing attack traffic from regular customer traffic often hinges on identifying subtle traffic spikes. Attack traffic typically reveals unique signals—such as originating from a particular country or using a specific ISP—that stand out when segmented across these dimensions.
For instance, let’s say a customer has 1,000 sessions in their overall traffic coming from a specific ISP. This may not seem significant compared to the total volume, but what if those sessions come from an ISP the customer rarely sees? In this case, the 1,000 sessions might have gone undetected if no other triggers were activated. However, identifying 1,000 sessions from a rarely seen ISP could reveal a granular anomaly, which we would then be able to stop.
With multi-dimensional velocity detections, our system can classify unusual traffic as legitimate or automated, reducing the risk of harmful traffic going undetected. This way, we shield our customers from even low-level threats that might otherwise slip through unnoticed, reinforcing a stronger, more responsive defense. This feature is especially effective against low and slow attack vectors.
To support proactive responses, various detection rules and thresholds for these dimensions are defined and monitored. When an anomaly or rule is activated, the system triggers immediate, relevant alerts, ensuring timely action.
Our advanced algorithms analyze historical data to set optimal auto-threshold levels for each dimension, adjusting continuously for accuracy. This feature allows for smarter threshold management with minimal manual intervention.
Page-level Biometrics
Page level Biometrics strengthen our existing Biometric Anomaly Detection capability by integrating data collection from the moment the page loads on the end user’s device—adding an additional layer of behavioral data to the interaction patterns gathered during mitigation challenges. With page-level biometrics, we can assess user behavior earlier in the session, improving detection accuracy and reducing false positives.
The ML-powered biometric analysis is especially effective at detecting headless browsers and automated tooling. This feature also enhances our ability to detect human fraud operations that leverage automation. Page-level signals in this release include comparisons to past behavioral interactions, detection of scripted and modified web interactions, tracking anomalies in mouse dynamics, identifying granular velocity-based anomalies, and detecting unexpected behavioral patterns that deviate from legitimate user activity.
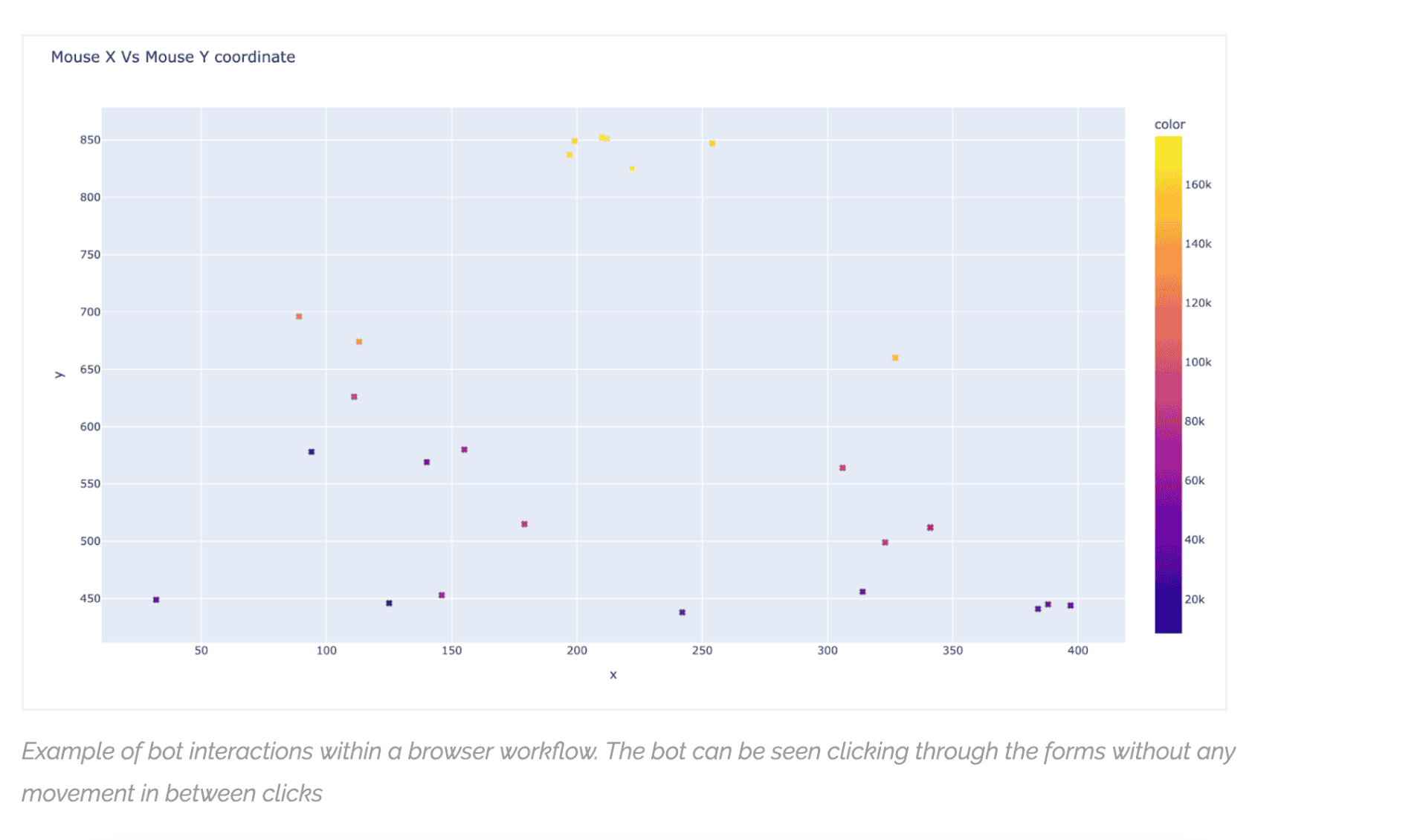
Example of bot interactions within a browser workflow. The bot can be seen clicking through the forms without any movement in between clicks
Network Anomaly Detection
Network Signals are vital indicators used to assess the legitimacy of incoming traffic in a security context. These signals enable Arkose Bot Manager to correlate network behavior with other session indicators, such as IP addresses, user agents, and device fingerprints. Monitoring these associations allows for the identification and mitigation of bot traffic, automation attempts, and potentially malicious activities, offering an additional line of defense against malicious bots, and allowing us to understand how browsers or sessions interact with our APIs and services. Known automation libraries can also be fingerprinted at the network layer using these signals.
By leveraging these new network based signals, and combining them with existing device information, we can better determine lower-level information about connecting browsers, substantially increasing detection efficacy.
Signals based on the network stack are difficult to tamper with and complement the other class of signals ( Device, Browser, Behavior etc ) to effectively detect malicious traffic.
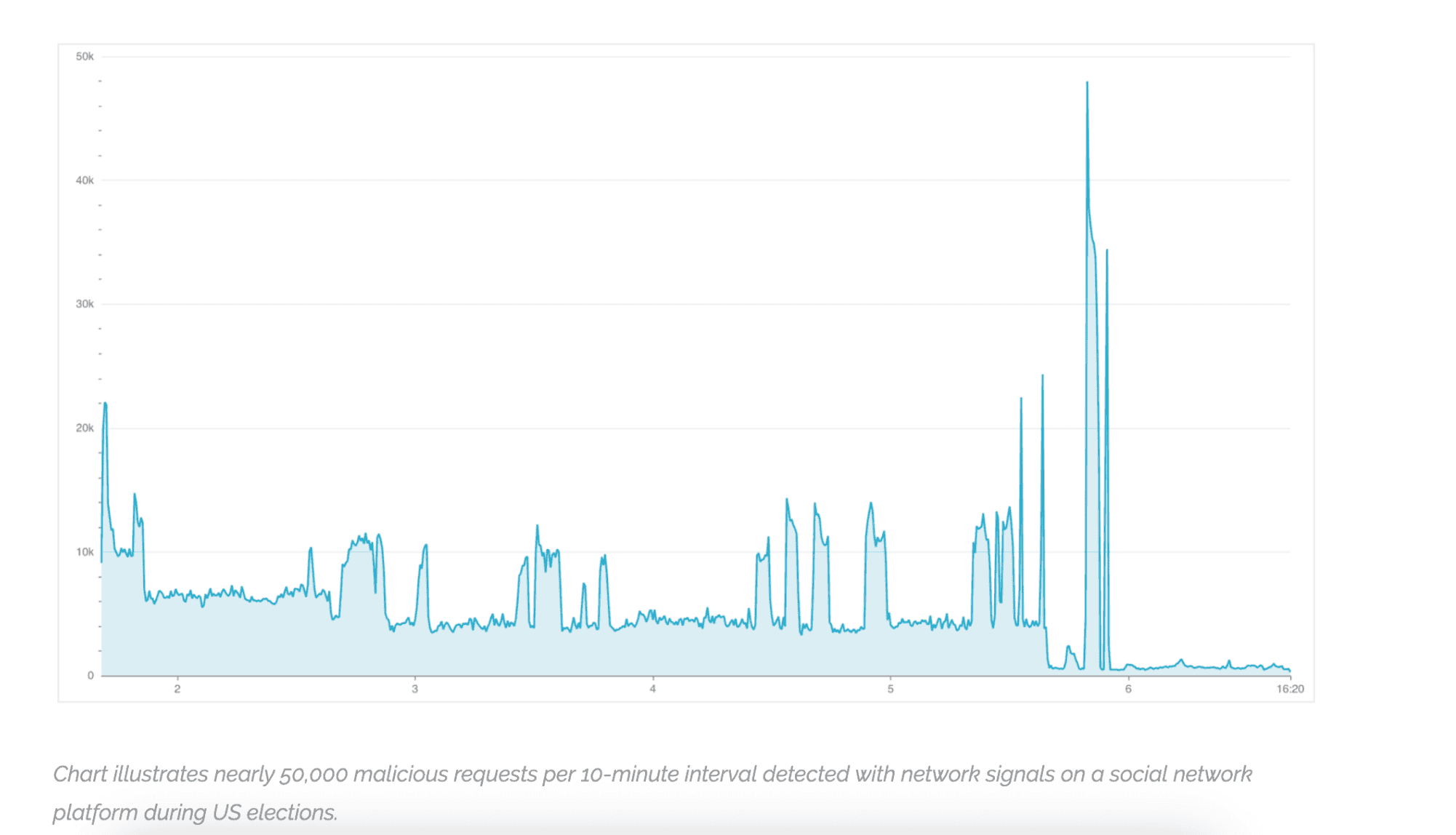
Chart illustrates nearly 50,000 malicious requests per 10-minute interval detected with network signals on a social network platform during US elections.
Proof of Work (PoW) (Preview)
To enhance our mitigation against cybercriminals, and complement the visual CAPTCHA mitigation challenges, Arkose Labs is introducing Proof of Work as a layer of security that requires a user’s device to complete a cryptographic computation tailored to its capabilities.
PoW is designed to reduce user friction and provides a scalable, effective, non-interactive alternative to mitigation challenges by significantly increasing attackers’ operational costs, making large-scale attacks unsustainable.
Currently, this preview version will present a highly-difficult PoW challenge, making it especially effective in high-risk scenarios.
In the near future, PoW will have the flexibility to adjust the challenge difficulty—low, medium, or high—based on the assessed threat level and device computational capabilities, covering a much wider range in risk scenarios. This feature promises a smoother user experience while effectively deterring large-scale attacks through high computational demands on malicious actors. More exciting features to come in the following quarters.
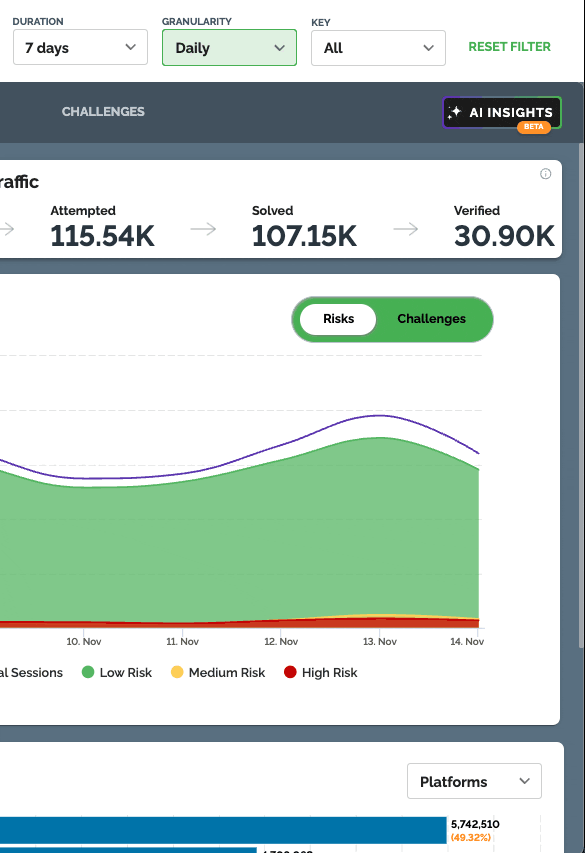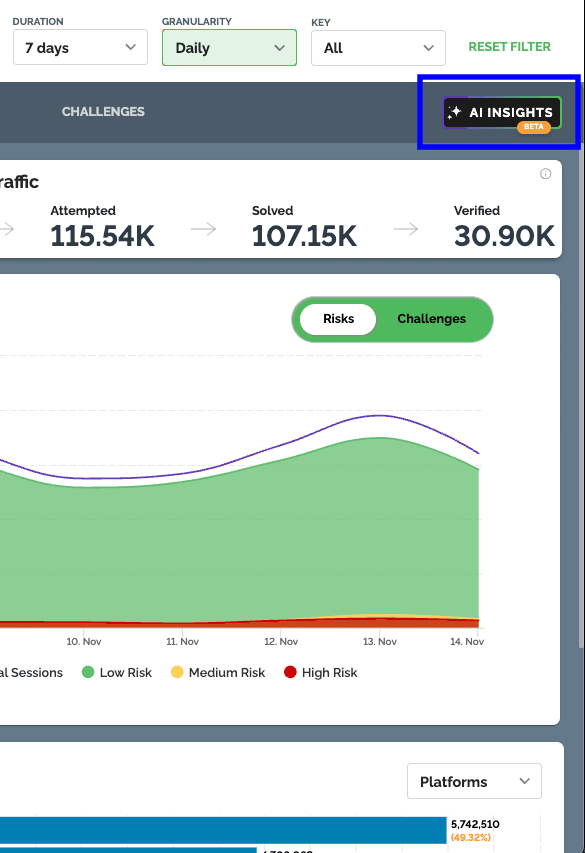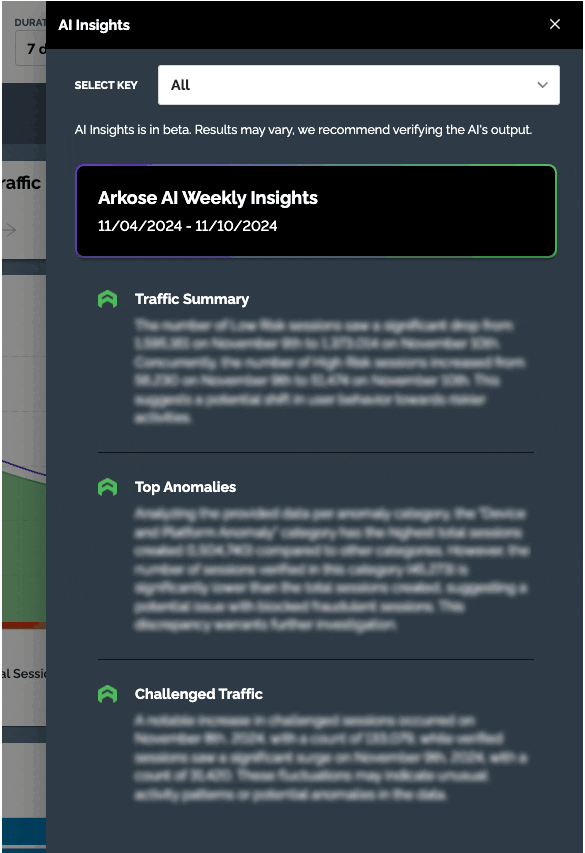
AI Reports in Arkose Command Center
This new AI-powered feature is designed to provide quick, easily digestible reports, bringing clarity to data trends and patterns right within your Command Center. These reports cover the following key categories:
- Traffic: Highlights trends and spikes based on risk levels, enabling quick identification of significant changes in activity.
- Anomalies: Offers insights into anomaly categories within your traffic, uncovering trends that provide a clearer view of irregular activity
- Challenges: Provides insights on interactive sessions and their verified rates, providing deeper understanding of challenged traffic interactions
The AI Insights report in Beta version is soon to be available via a new action button on your Dashboard, allowing you to quickly interpret complex data and identify critical patterns, ultimately streamlining and enhancing your security team’s decision-making process.
To learn more about our advanced technology or how these features can improve your risk and user experience strategy, please contact one of our experts.