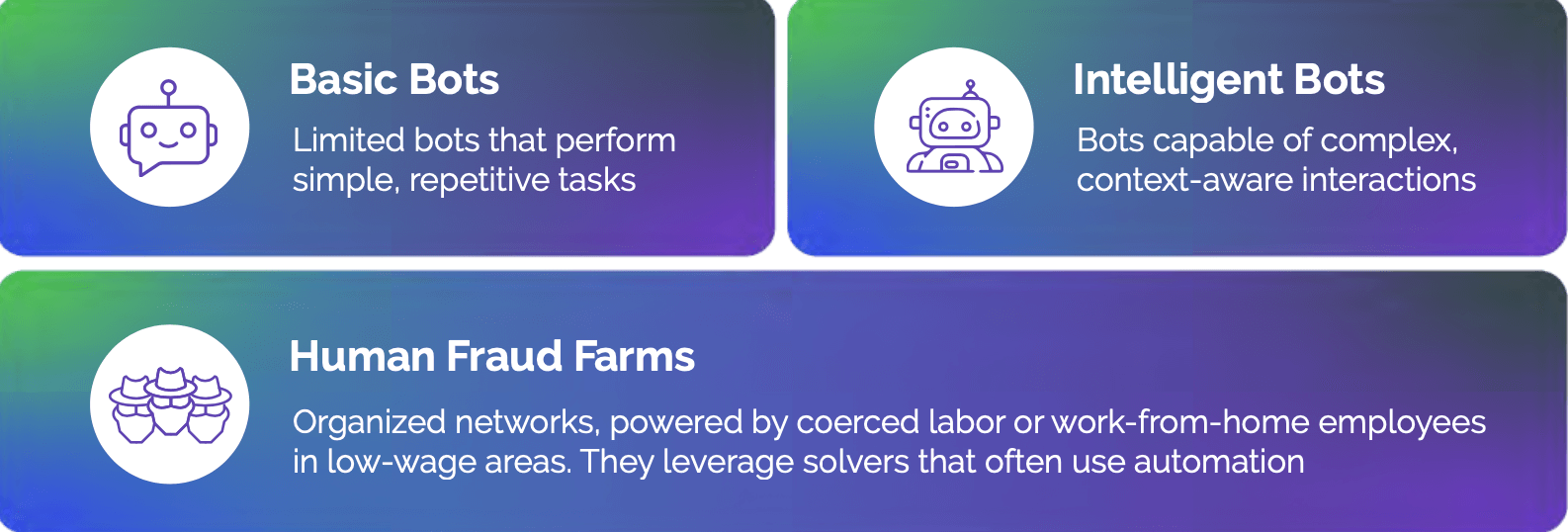
Mobile devices are facing a growing number of threats, particularly from bot attacks. The surge in mobile usage has led to an increase in cyberattacks that exploit vulnerabilities specific to mobile operating systems. These attacks use tactics like malicious apps, app-based vulnerabilities, and SMS messages.
Mobile attacks aim to compromise data, track user activities, or gain unauthorized access to sensitive information on mobile devices. As technology evolves, the distinction between mobile and traditional computing capabilities is blurring. But recognizing the impact of mobile attacks on digital businesses and their customers is crucial, especially given the vital role mobile devices play in digital transactions and interactions.
The rich data pulled from our recent industry report, Bot Abuse Analysis and Other Fraud Benchmarks, reveals the growing prevalence and sophistication of mobile cyber threats. Insights are drawn from the Arkose Labs Global Intelligence Network, which includes major corporations and category leaders. These organizations, highly susceptible to online threats, offer a distinctive vantage point for the observation and analysis of cyber activities. The information underscores the growing importance of addressing mobile security and the need for robust bot security to safeguard digital enterprises and consumers.
Global Threat Intelligence on Mobile Bot Attacks
According to our research, the threat landscape for bot attacks has witnessed a significant surge on mobile devices, marking a 106% increase in all attacks originating from these platforms. Mobile devices have become a primary target, representing 44% of all bot attacks. Fraud farm attacks on mobile devices have seen a notable increase of 63%, which highlights the vulnerability of these platforms to criminal activities.
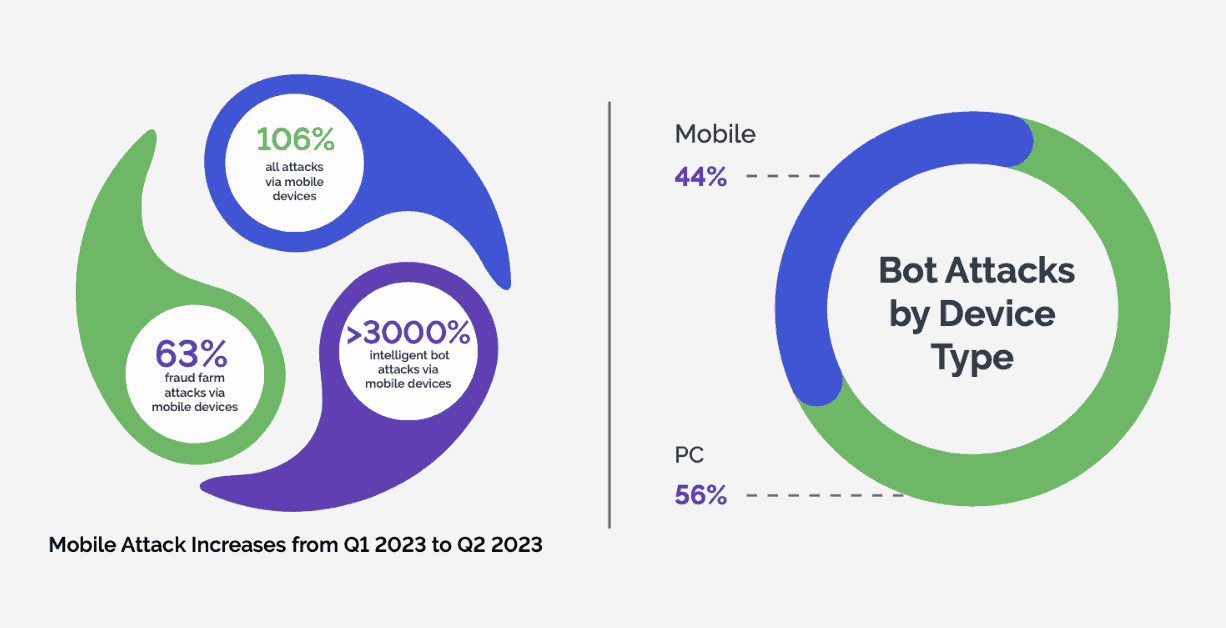
Simultaneously, the prevalence of intelligent bot attacks has skyrocketed by over 3000%, demonstrating an alarming trend of cybercriminals exploiting vulnerabilities inherent in mobile operating systems. While 56% of bot attacks still occur on PCs or laptops, the substantial rise in mobile-centric attacks calls for heightened vigilance and tailored defense strategies.
The Geographics of Mobile Bot Attacks
Mobile threats often originate from regions where mobile devices are more widespread than laptops, creating large segments of the population with smartphones but no personal computers. As a result, the widespread use of mobile devices makes it easier for attackers to blend in with regular users, creating a disguise that helps them go unnoticed.
The impact of mobile threats extends beyond just the prevalence of these devices; it also raises concerns about the potential for large-scale cyber incidents and their socio-economic consequences. With the majority of the population relying heavily on smartphones for various daily activities, from communication to financial transactions, the vulnerability of these devices amplifies the potential fallout from successful cyber attacks. Just last year, it was reported that 43% of all compromised mobile devices were fully exploited, not just jailbroken or rooted, an increase of 187% YOY.1
How does a mobile attack work?
In a mobile banking scenario, an employee unwittingly downloads a seemingly harmless app that contains malicious code. Once installed, the app breaches the smartphone's security, granting unauthorized access to sensitive financial data. The attacker then exploits this information in a phishing campaign, tricking customers into revealing login credentials. As a result, unauthorized access to customer accounts leads to fraudulent transactions, causing financial losses, reputational damage, and regulatory scrutiny.
Top 5 Mobile Attack Types
Based on our threat analysis, five prominent attack types stand out, each posing distinct challenges and risks. From in-product abuse to payment fraud, these threats demand a closer look at the strategies cybercriminals are now using to target the mobile landscape.

- Fake Account Creation on mobile devices involves generating deceptive profiles or accounts on digital platforms, typically with fictitious or stolen information. Attackers use various methods, such as automated scripts or manual inputs, to create these fake accounts. The primary purpose is to engage in fraudulent activities, including spreading misinformation, conducting scams, or exploiting services that rely on user interactions. The use of fake accounts to influence product reviews, for example, is now so widespread that it has become a flourishing industry of its own.
 For businesses, fake account creation can lead to skewed user metrics, diminished user trust, and increased operational costs for managing and verifying accounts. Additionally, fake accounts can be used to manipulate reviews, ratings, or engagement metrics, influencing the perceived credibility of a platform. According to our analysis, in Q2 2023, there was a 202% increase in bots trying to take over accounts in financial institutions, and a 164% jump in bots attempting to create fake new bank accounts.
For businesses, fake account creation can lead to skewed user metrics, diminished user trust, and increased operational costs for managing and verifying accounts. Additionally, fake accounts can be used to manipulate reviews, ratings, or engagement metrics, influencing the perceived credibility of a platform. According to our analysis, in Q2 2023, there was a 202% increase in bots trying to take over accounts in financial institutions, and a 164% jump in bots attempting to create fake new bank accounts.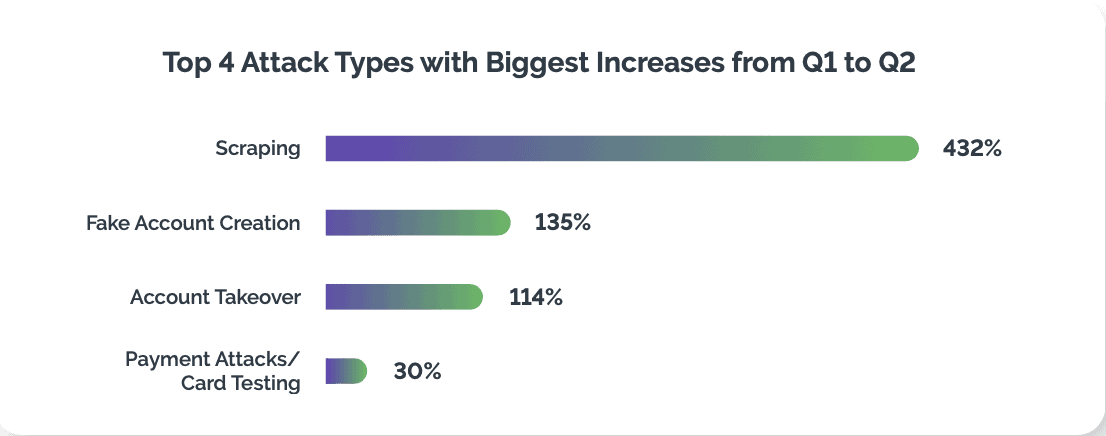 As one of the top four attack types, fake account creation affects businesses and customers in myriad ways. Scams, phishing attempts, or deceptive information spread by malicious actors using fake accounts are some examples. The presence of fake accounts can also compromise the overall user experience, as they may interact with bogus profiles, thereby impacting the integrity of online communities.
As one of the top four attack types, fake account creation affects businesses and customers in myriad ways. Scams, phishing attempts, or deceptive information spread by malicious actors using fake accounts are some examples. The presence of fake accounts can also compromise the overall user experience, as they may interact with bogus profiles, thereby impacting the integrity of online communities.
- Account Takeover (ATO) attacks on mobile devices involve attackers gaining unauthorized access to user accounts through various tactics, such as credential theft, phishing, or exploiting vulnerabilities in the mobile app or operating system. Once attackers successfully take over an account, they can impersonate legitimate users, manipulate sensitive information, conduct fraudulent transactions, or engage in other malicious activities.
 For businesses, ATO can lead to financial losses, reputational damage, and legal consequences. Cybercriminals may exploit the compromised accounts to perform fraudulent transactions, access proprietary information, or disrupt business operations. The trust and credibility of the business may be compromised, resulting in a loss of customer confidence.Customers, on the other hand, face risks such as unauthorized access to personal information, financial losses, and potential identity theft. ATO attacks can undermine the trust users place in digital platforms and lead to a negative user experience.
For businesses, ATO can lead to financial losses, reputational damage, and legal consequences. Cybercriminals may exploit the compromised accounts to perform fraudulent transactions, access proprietary information, or disrupt business operations. The trust and credibility of the business may be compromised, resulting in a loss of customer confidence.Customers, on the other hand, face risks such as unauthorized access to personal information, financial losses, and potential identity theft. ATO attacks can undermine the trust users place in digital platforms and lead to a negative user experience.
- Account Management attacks on mobile devices involve exploiting vulnerabilities in customer support systems, particularly during processes like password resets and account recovery. Attackers may employ various tactics, such as social engineering, phishing, or manipulating customer support representatives, to gain unauthorized access to user accounts.For businesses, these attacks can lead to unauthorized access to sensitive user data, compromise of accounts, and potential breaches of confidential information for businesses. Attackers may exploit account recovery processes, impersonating legitimate users and gaining unauthorized access to proprietary information or conducting bogus transactions.For consumers, this means privacy breaches, unauthorized access to personal information, financial losses, and potential identity theft as a result of account management attacks. Trust in the digital platform may be eroded, and users might become hesitant to engage with customer support services, fearing potential security risks.

- In-Product Abuse on mobile devices refers to malicious activities conducted within the features and functionalities of digital products or services. This can include actions such as inventory hoarding, loyalty point abuse, chat manipulation, bogus gaming sessions, cheating services, and win-loss trading. Attackers exploit vulnerabilities in these features to engage in deceptive practices—such as phishing through SMS or exploiting WiFi networks to intercept transactions—often for financial gain or disruption.For businesses, these threats can lead to financial losses, compromised user experience, and reputational damage. The manipulation of features like inventory hoarding or loyalty point abuse can disrupt the intended functionality of digital products, affecting the fair use by genuine customers.In-product abuse can lead to unfair competition in online gaming or trading platforms, negatively impacting the overall integrity of these services. Additionally, the credibility of the digital business may suffer, as customers may lose trust in the platform's ability to provide a secure and fair environment.

- Payment Attacks involve the illicit use of stolen payment information for unauthorized digital transactions. This includes fraudulent activities such as card testing fraud, Man-in-the-Middle attacks, and SIM card swapping.According to industry reports, online payment fraud will exceed $362 billion globally between 2023 and 2028, with losses of $91 billion alone in 2028. , highlighting the substantial economic impact on businesses.2 Consumers, on the other hand, face the direct consequences of compromised financial information, leading to unauthorized transactions, identity theft, and potential financial loss.The pervasiveness of mobile payment attacks is evidenced by a substantial increase in reported incidents, with a 56% rise in mobile banking Trojans alone in the past year. As reliance on mobile transactions continues to grow, the need for robust security measures becomes paramount to protect both businesses and consumers from the escalating threat landscape.
Arkose Labs, a trusted leader in bot management and account security, safeguards the world’s largest B2C enterprises, Fortune 500 companies, and trailblazing businesses. Its AI-powered Arkose Bot Manager platform provides detection and protection, precisely distinguishing legitimate consumers from malicious bots and diminishing adversaries’ financial gains by increasing attack effort and cost. G2 consistently ranks Arkose Labs high for customer satisfaction and extensive market presence, based on verified customer reviews. Innovating the first cybersecurity industry guarantee program, the company offers $1 million warranties for credential stuffing, card testing, and SMS toll fraud. Arkose Labs is headquartered in San Mateo, CA, with global offices in Asia, Australia, Central America, and South America.



