What is a Reverse Proxy?
Organizations with applications and services distributed across multiple servers and networks face challenges when it comes to managing and securing their web traffic, especially incoming requests from external clients. One solution to this problem is the use of a reverse proxy server.
Reverse proxy servers can provide global server load balancing, distributing traffic across multiple servers in different geographic locations to ensure that clients are connected to the closest and most available server. They can also be used to provide a single point of contact for clients to access resources on a single origin server. Here, we’ll describe what a reverse proxy is, how it works, the benefits of a reverse proxy server, and the types of attacks that can target a reverse proxy server.
How a reverse proxy server handles traffic
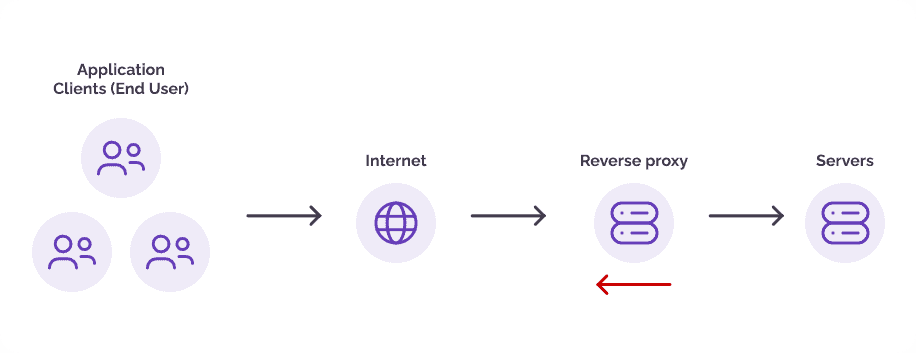
Benefits of a Reverse Proxy Server
The benefits of using a reverse proxy server are many, including:
- Improved performance and scalability
- Improved security
- Caching and compression
- SSL termination
- Monitoring and logging traffic
Improved Performance & Scalability
One of the key advantages of using a reverse proxy is that it can help improve the performance and scalability of a web application. Reverse proxies can use the Domain Name System (DNS) to route client requests to the appropriate server based on the domain name, IP address, or other criteria, providing additional flexibility and control over how traffic is distributed across a network. This can help reduce response times and improve the overall reliability of the application.
Improved Security
Reverse proxies can be used to provide a secure gateway for web applications to be accessed from the public internet, mitigating the risk of attacks and unauthorized access. By acting as a middleman between incoming traffic from the internet and backend servers, a reverse proxy server can protect against common web-based attacks such as a DDoS attack, SQL injection, and cross-site scripting. It can be set up with a firewall in a buffer zone that permits access to it, or the configuration could restrict access to certain resources or services, handle user authentication before forwarding a request, and ensure that only authorized clients are able to access sensitive information. A reverse proxy can terminate Transport Layer Security (TLS) connections, allowing it to decrypt and inspect the traffic for malware or filter out malicious traffic before the request reaches the web server. Additionally, reverse proxies can help hide the origin server's IP address, making it harder for hackers to target.
Caching & Compression
One of the most significant benefits of a reverse proxy server is powerful caching. Reverse proxy servers can be used for web acceleration by caching frequently accessed or dynamic content, or content from a CDN (content delivery network), which reduces the server load and improves response times for clients. This can be especially useful for websites that have high traffic volumes or frequently accessed content, such as images or videos.
By caching frequently accessed data, a reverse proxy can serve it quickly to clients without requiring the server to generate it each time. This can greatly improve the user experience, decrease load times, and reduce bandwidth usage for websites with high traffic volumes.
SSL Termination
SSL termination involves decrypting incoming SSL traffic at the reverse proxy and then forwarding the request to the backend servers in plain text. This setup can help reduce the computational load on the backend servers, as they no longer need to handle SSL encryption and decryption.
Monitoring and Logging Traffic
The ability to monitor and log traffic to your web servers will help you detect and prevent security threats. Additionally, reverse proxies can provide detailed analytics on website traffic and usage patterns, which can help with website optimization and performance.
Types of Reverse Proxy Servers
There are many types of reverse proxy servers available, each with its own set of features and capabilities. Some popular open source options include Nginx, Apache, and HAProxy.
Nginx is a lightweight and high-performance reverse proxy server that is particularly well-suited for serving static content. Apache, on the other hand, is a more full-featured web server that can be used as a reverse proxy as well as a traditional web server. HAProxy is a high-performance TCP/HTTP load balancer that is often used in conjunction with other reverse proxy servers to provide additional scalability and redundancy.
What are Reverse Proxy Attacks?
A reverse proxy server can act as a web application firewall (WAF) by inspecting incoming client requests and filtering out malicious traffic, helping to protect web servers and applications from cyberattacks. When attackers target the reverse proxy server to gain control over it and intercept traffic, it can result in cache poisoning or HTTP header injection, which could then allow them to perform cross-site scripting (XSS) attacks.
The latest evolution of phishing kits is the Man-in-the-Middle (MITM) toolkit which acts as a malicious reverse proxy server of online services, mirroring target website content to users while extracting credentials like MFA tokens and session cookies in transit. The MITM phishing kits also automate the harvesting of multi-factor authentication (MFA) sessions.
Some of the most widely used MITM phishing toolkits are Evilginx and Modlishka. EvilProxy is the most recent and uses the same reverse proxy approach to lure victims to phishing sites and then sniff out the traffic to extract credentials and MFA tokens.
Conclusion
Reverse proxies offer a wide range of functionality, including load balancing, caching, SSL/TLS termination, content filtering, and more, making them a versatile tool for improving the performance, security, and reliability of web applications. While reverse proxy servers can improve website performance and security, they can also become a single point of failure if they are not properly configured or fail due to hardware or software issues, which could potentially disrupt the flow of traffic between clients and servers. By understanding how a reverse proxy works, businesses can make informed decisions about their web infrastructure to improve performance, enhance security, and streamline operations.
A robust bot management solution, like Arkose Labs, is an important part of an overall enterprise security plan. And Arkose Labs combines highly-transparent detection with targeted attack response to catch fraud early in the customer journey. It is configured in a website's login and registration workflows prior to the MFA step. This phishing detection feature not only protects from MITM reverse proxy attacks by requiring our token to be present, but also may alert the end consumer about the phishing attack.
Want to learn more? Book a demo today!