Google’s web security service, reCAPTCHA, is seemingly ubiquitous on the internet. Virtually anyone who has logged into one digital account or another has encountered this authentication service and clicked on more pictures of buses and traffic lights than they’d care to think about.
One reason for reCAPTCHA’s initial widespread use was that it was free. Any company doing business online that wants a modicum of bot protection could integrate it on login or registration pages without investing a dime.
But that’s not entirely true anymore. In 2021, Google released reCAPTCHA Enterprise, which charges its users based on monthly usage. The enterprise version is free for up to 1 million assessments per month, but larger companies could easily surpass those limits. That has businesses asking themselves:
“Is it worth it for our organization to invest in reCAPTCHA Enterprise?”
The answer depends on many factors, including a company’s security requirements and the tool’s overall cost. Here’s a look at what reCAPTCHA Enterprise offers, its pros and cons, and how it fits into the CAPTCHA marketplace.
How reCAPTCHA Enterprise works for bot detection
According to its own description, Google uses “an advanced risk analysis engine” to determine the suspicion level of traffic to a website. Any traffic that is deemed suspicious is served a reCAPTCHA enforcement challenge. This can entail either only clicking the “I’m not a robot” box, or also picking out mundane everyday items from a grid.
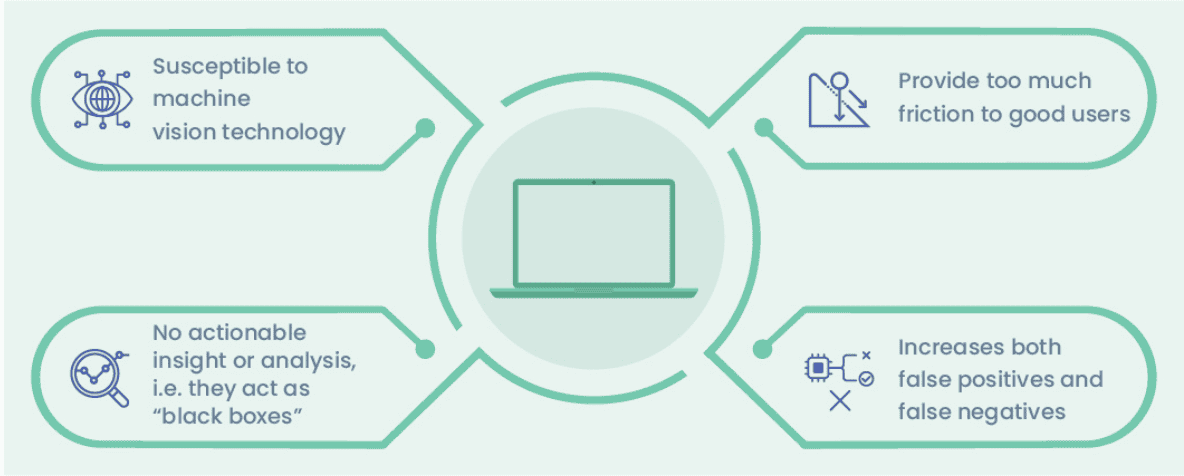
A few common issues arise with this approach.
Good users are often classified as suspicious
Google’s “advanced risk analysis” noted above is heavily dependent on the use of Google cookies1. That means if you are a Chrome user, or are logged into a Google account such as Gmail, Google knows much more about you and how “suspicious” your web activity is. So users of Google products and services will likely bypass any reCAPTCHA challenge.
Bots have become adept at solving puzzles
Image recognition software has gotten so advanced that it can easily solve most reCAPTCHAs with little difficulty2. And it's easy to get a hold of software to do just that. A simple web search for bots that solve reCAPTCHA turns up dozens of results, some of which offer access to automated scripts for as little as $20/year. An American computer science professor used off-the-shelf image recognition tools to solve Google’s image CAPTCHAs with 70 percent accuracy.3
Even AI tools have gotten in on the game, as earlier this year a ChatGPT tricked a human into helping it bypass a CAPTCHA test.4
reCAPTCHA Limitations
What is the difference between reCAPTCHA and reCAPTCHA Enterprise?
In response to many of these concerns, Google rolled out v3 of its security solution, followed by the Enterprise version, which was built on everything v3. So how exactly is this latest version different from earlier iterations?
The biggest change is that it aims to show far fewer challenges to the user. Instead, reCAPTCHA Enterprise works “invisibly” in the background, constantly monitoring user behavior to determine whether each visit to a site is a human or a bot.
Google then returns a risk score to website administrators between 0 and 1. 0 means you’re definitely a bot, 1 means you’re definitely a human, and in between is a very large gray area. Website admins then must decide what to do based on the score they receive for each user.
reCAPTCHA Enterprise still favors users of Google products
Much like its predecessors, newer versions of reCAPTCHA still largely look at whether you have Google cookies on your browser to determine if you are suspicious. According to a Fast Company article, “With reCAPTCHA v3, technology consultant Marcos Perona and Mohamed Akrout’s tests both found that their reCaptcha scores were always low risk when they visited a test website on a browser where they were already logged into a Google account.” 5
Therefore, those using browsers other than Chrome or tools to maintain online privacy will likely face friction.
Furthermore, it should be noted that any environment that doesn’t enable cookies will automatically lead to much higher instances of good users seeing reCAPTCHA challenges. This includes when authenticating on iOS and Android apps, as well as desktop applications such as launching apps for PC video games.
This is also an issue for users in places where Google does not have a presence. Take mainland China, where Google is banned. It’s one of the largest economies and consumer markets in the globe. No Google means no Google cookies, so users almost always have to solve challenges. It’s plainly apparent that a cookies-based approach to authentication is not viable in the long term.
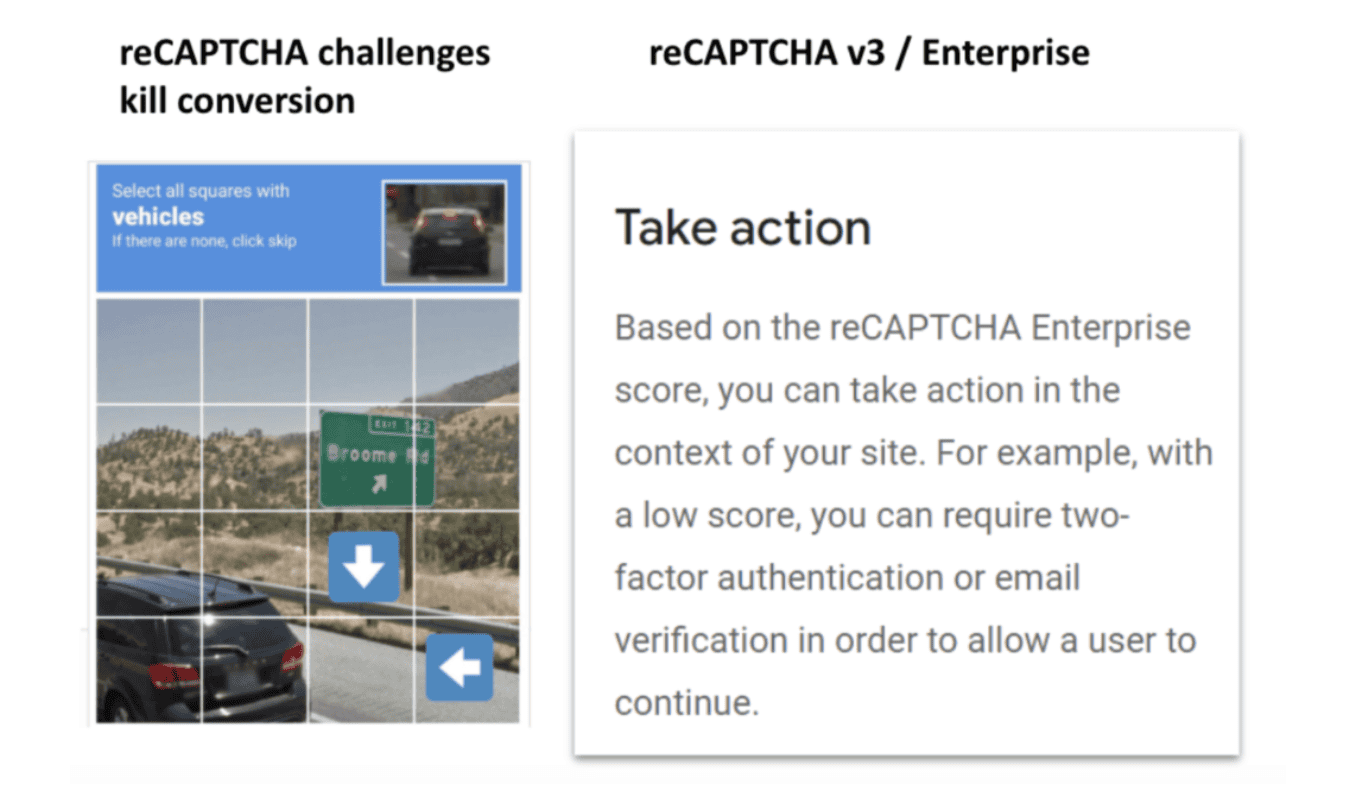
reCAPTCHA is still the same challenge
So, what do you do for your users who get assigned high-risk scores? Well, you have a few options. One is to serve them a challenge...which is exactly the same reCAPTCHA it has always been. Any business deploying reCAPTCHA Enterprise is still going to have only the same old reCAPTCHA grid with picking crosswalks available to them if they want to serve a challenge to suspected suspicious traffic. Website operators can also choose to trigger two-factor authentication (2FA) for those with low scores, but this provides even more friction to potential good users than solving a CAPTCHA.
A “Black Box” with No Data
The main issue with a risk scoring system is one that has long been an issue for users of reCAPTCHA or many other services: There is no insight or data analytics.
Google can tell you if it thinks someone is suspicious, but not what to do about it. If you are a website admin, at what score do you draw the line for challenging a user? Is it .15? .25? Ultimately, any web pages using reCAPTCHA will end up either blocking too many good users or being too lax and letting too many attackers through.
Businesses need insight into attack patterns to be able to stop future threats. Without a constant feedback loop refining the accuracy of its risk scores, reCAPTCHA or another CAPTCHA solution cannot learn or evolve to defend against the ever-changing threat landscape.
Which reCAPTCHA should I use?
To effectively manage fraud and abuse in this rapidly evolving ecosystem, businesses need a long-term approach that evolves with attack patterns, instead of playing a constant game of whack-a-mole with cyber attacks.
That’s why Arkose Labs takes a different approach. Rather than traditional “fraud mitigation” we aim to bankrupt the business model of cybercrime entirely. By removing the ROI for cyber attacks, bad actors are compelled to abandon attacking your site and attack someone else.
Arkose MatchKey is the strongest CAPTCHA ever made. It presents users with adaptive challenges, such as puzzles or tests, that are designed to be easy for genuine human users to solve but difficult for automated bots. By successfully completing these challenges, users authenticate themselves as humans, helping to differentiate them from malicious bots. Arkose MatchKey enhances the overall security and user experience by effectively thwarting automated attacks while minimizing disruptions for legitimate users.
This is how Arkose Labs ensures bots are foiled and good customers aren’t frustrated:
Accurate classification
Risk scores based on identity fail to stop modern attacks. Arkose Labs analyzes hundreds of data points around behavior to create “telltales” to determine whether a user is suspicious. This is partially informed by data from our extensive global network, where we create telltales of known previous attacks.
Arkose Labs also can implement industry-specific telltales customized for individual merchants based upon their business model and industry. Traffic is then segmented based on whether it is likely to be legitimate, a bot, or a human sweatshop–which informs the platform of any required secondary screening and the type of enforcement challenge it should show.
Challenge and interact
To understand traffic intent in a deterministic way, secondary screening must be paired with the risk assessment stage. Our platform tests and challenges high-risk traffic using interactive technology that causes all automated attacks to fail.
Meanwhile, increasingly complex challenges are served to human sweatshop workers, which increases the amount of time it takes them to complete a task, thus reducing their ROI and ultimately leading them to abandon their attacks. Challenges can either be timed (to stop queued solve pipelines) or take a long period of human attention to solve (to sap efficiency). The platform tailors the type of challenge based on the nature of the sweatshop attack.
The small number of good users who may see a challenge will be able to solve it on average in less than 3 seconds. Our challenges are also designed with gamification principles–meaning they are fun to solve, unlike CAPTCHAs. They can also appear as brand-specific challenges, which enhances the customer experience.

RECOMMENDED RESOURCE
The Ideal CAPTCHA: Arkose MatchKey Has Defensibility, Usability & Accessibility
Evolving technology with machine learning
The Arkose Bot Manager is an adaptive approach to bot prevention and account security. It combines risk assessments with Arkose MatchKey challenges, which creates a continuous feedback loop to improve fraud detection rates while decreasing challenge rates for good users. Embedded machine learning provides advanced anomaly detection and evolving protection, taking the burden away from in-house teams.
The feedback loop also ensures that any good user who sees a challenge will not continue to do so after they have solved it the first time. The solution can also be used to send data to validate if a user ultimately was a cybercriminal, which can be used to further train appropriate defenses for future or ongoing attacks.
Arkose Labs customers also benefit from real-time logging (RTL), which is the detailed logs of user activity provided by Arkose Labs' servers. These logs are sent to a client-specified endpoint, which may be a server you run directly, or a third-party service designed to digest and package logging data for analysis. The RTL data is made up of events. Each event is tagged with a unique session token that ties it to a user. Events are sent in real-time and cover the entire user experience, from Arkose Labs session creation to the session verification attempt.
Included in the RTL data is telemetry data about the user, including what has been learned from the user's presence elsewhere on the Arkose Labs network. If the user was given an elevated security level, the reasons for that are also included. And since we don’t block any traffic, instead of challenging suspicious traffic, false positives are drastically reduced and our customers don’t have to worry about being blocked. Arkose Labs offers strong protection for use cases including account takeover, credential stuffing, SMS toll fraud, new account fraud, website scraping, and more.
In short, Arkose Labs doesn’t just mitigate the effects of bot attacks. It provides powerful remediation that eradicates 100% of automated traffic and enables businesses to deflect attacks from skilled cybercriminals and sweatshop outfits.
Learn more about how we can help or book a demo.
Bot Management Software: Guaranteed Results Stopping Bots With Arkose Labs
- How reCAPTCHA Enterprise works for bot detection
- What is the difference between reCAPTCHA and reCAPTCHA Enterprise?
- reCAPTCHA Enterprise still favors users of Google products
- reCAPTCHA is still the same challenge
- Which reCAPTCHA should I use?
- Accurate classification
- Challenge and interact
- Evolving technology with machine learning