What Is Card Testing Fraud?
Card testing fraud involves cybercriminals validating stolen credit card details through small online purchases. They use these trials to confirm card validity before making larger fraudulent transactions or selling these validated payment credentials on the dark web, aiming to exploit active cards without raising suspicion.
The Mechanics Behind the Attack
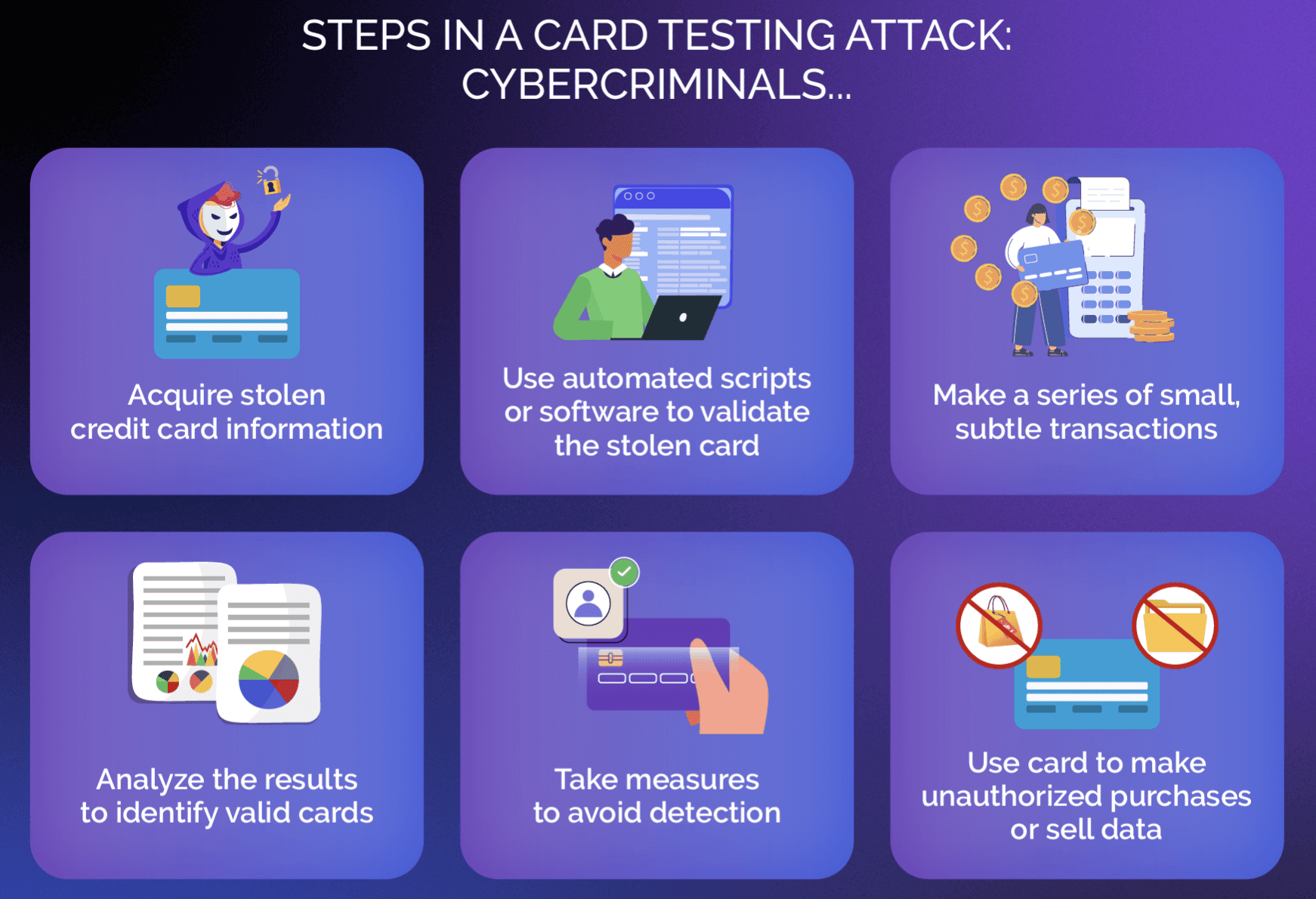
Carders may employ a variety of techniques to test the stolen credit card details. The steps involved in a card testing attack usually include:
- Data Acquisition: To steal credit card information, card testers may use data breaches, phishing attacks, or even purchasing information from the dark web.
- Account Creation: Using stolen details, attackers create fake accounts that are then used to test the validity of the compromised card numbers.
- Testing: Whether manually or using automated scripts, attackers perform pre-authorization checks or make small, low-value transactions to avoid the attention that high-value transactions may attract.
- Observation: If the transactions or pre-authorization checks are successful, it indicates that the details are valid and the cards are still active.
- Collection: Attackers collect validated card details and build databases by repeating the process with several combinations.
- Evasion: Carders employ several evasion techniques to avoid detection. These may include rotating IP addresses, using proxy servers, or mimicking legitimate card owner behavior.
- Monetization: Upon obtaining lists of valid credit card numbers, attackers may use them to make high-value purchases, power other criminal activities, or sell the databases to third parties or on the dark web.
The Role of Botnets
Attackers exploit advanced automation, particularly botnets, to amplify credit card testing endeavors. Botnets, networks of hijacked computers under their control, enable large-scale, anonymous testing of stolen credit card data. This tactic accelerates validation processes and evades detection by leveraging dynamic IP addresses. Consequently, security teams confront significant hurdles in detecting and thwarting such cyber threats, as botnets serve multiple criminal purposes beyond card testing, including DDoS attacks, credential stuffing, and malware propagation. With the advancement of botnet technology in recent years, the threat of card testing fraud has grown exponentially, causing not only financial losses but also serious brand damage for businesses. This makes it crucial for businesses to take preventative measures.
The are several ways in which botnets enable card testing fraud, including:
- Automation and Scale: Botnets can automatically execute card testing transactions on a large scale, providing attackers with validated lists of card details quickly.
- Distributed Testing: Because botnets are distributed in nature, attackers can execute card testing activities through multiple devices and IP addresses, aiming to avoid detection in the process.
- Evasion: Botnets feature evasion techniques such as randomizing transaction times, using different geolocations, and rotating IP addresses. Botnets can mimic genuine users, making it difficult for security teams to detect malicious activity.
- Dynamic IP Addresses: Botnets use a large pool of dynamic IP addresses, making it difficult for security teams to block or blacklist the IP addresses associated with card testing activities.
- Anonymity: By creating a layer of anonymity, botnets allow attackers to use compromised devices across the globe to execute attacks, making it virtually impossible to track the origin of the attacks.
Identifying a Card Testing Fraud Attack
Recognizing the signs of an attack is critical for prompt response and risk mitigation. It is, therefore, crucial that businesses, merchants, and financial institutions deploy robust detection systems, including security systems, that leverage advanced analytics, machine learning, and behavioral analysis to accurately identify and respond in real time. Collaboration with industry peers and sharing threat intelligence can help detect and prevent card testing attempts through the implementation of best practices.
In addition, businesses must ensure their security measures are always up-to-date so they are able to identify the telltales of a card testing attempt. Some of the common patterns are:
- Unusual Transactions: Small, rapid transactions within a short time-frame might indicate attackers trying to validate stolen card details.
- Testing Amounts: Common testing amounts, such as round numbers or specific values can indicate card testing activities.
- Frequency: An unusually rapid transaction rate from a single card or set of cards within a short period may indicate testing for valid cards.
- Cardholder Information: Similar cardholder information and testing values (expiration date or security codes) being used in multiple transactions.
- Successful or Declined Transactions: A high volume of transactions, especially those with small purchases or specific merchants, being repeatedly declined. A high success rate, on the other hand, may indicate an attacker preparing for high-value transactions using validated information.
- Behavioral Anomalies: Deviations from a cardholder's normal behavior, such as transactions carried out on days or time of the day that occur outside of the legitimate cardholder transaction pattern, may suggest attackers exploiting non-peak times to avoid.
- Surge in Account Creation: A sudden increase in new accounts may indicate attempts to test stolen card details for validity.
- IP Address: Suspicious IP addresses or a large number of transactions emanating from a single IP address may indicate use of botnets and proxies to obfuscate identity and location.
- Automated Tools: Distinct fingerprints that automated tools or scripts leave behind.
- Unexpected Geographies: Transactions originating from unexpected geographical locations suggest use of proxies or compromised devices from several locations with the aim to obscure true location.
The Impact on Your Business
Card testing can leave a lasting impact on businesses through financial, reputational and regulatory damages. Undetected attacks burden businesses with chargeback requests and reimbursements. Repeated attacks may attract additional scrutiny from financial institutions and payment processors with the risk of restrictions or increased transaction fees.
Compromise of customer data can cause distrust among consumers that can impact future business prospects. Further, security lapses may lead to legal consequences in the form of fines and penalties, adding to financial losses.
Implementing Multi-layered Protection Against Card Testing Fraud
In view of the long-lasting damages that businesses stand to suffer, it is essential that companies adopt multilayered protection. A multilayered protection approach creates a strong defense by implementing a combination of advanced technologies and strategies.
The Importance of Risk Reviews and Risk Monitoring
To assess and manage the risks that can impact operational efficiency, businesses must conduct risk reviews regularly. With this proactive approach, businesses can address the potential issues before they escalate and prevent financial, reputational, and legal damages.
Risk reviews refer to a systematic evaluation of financial transactions, cybersecurity measures, compliance with regulations, and other factors that can add to potential risks. Periodic risk reviews enable businesses to identify vulnerabilities, measure the effectiveness of existing risk mitigation strategies, and make data-driven decisions for an upgraded risk management framework. Risk reviews also help businesses stay compliant with evolving industry regulations and mitigating compliance-related risks.
Setting Minimum Payment Thresholds
By setting minimum payment thresholds, businesses can discourage fraud associated with small transactions and reduce their chargeback rates. Establishing a minimum transaction amount not only streamlines operational workflows but also encourages customers to make larger purchases, which improves overall revenue and profit margins. This enables businesses to minimize the impact of processing fees, authorization fees and administrative overhead associated with small card payments.
Recognizing and Responding to Anomalies
To protect their digital assets, businesses must accurately recognize and respond to anomalies indicative of card testing attempts. These anomalies may include unusual transaction patterns, rapid testing velocities, or unexpected geolocations.
Businesses must consider using automated systems to help recognize these anomalies in real-time, which will trigger alerts to enable security teams to make prompt interventions.
The Role of Technology in Preventing Card Testing Fraud
Technology plays a key role in empowering businesses by providing proactive, intelligent, and adaptive measures to stay ahead of evolving fraud tactics.
Some of the ways technology is powering the fight are:
- Fraud Detection Systems: State-of-the-art fraud detection systems that leverage machine learning algorithms and artificial intelligence help analyze transaction patterns, user behavior, and other data points in real-time and identify attack telltales.
- Behavioral Analytics: To establish baselines for normal user behavior and detect anomalies that suggest potential fraud.
- Device Fingerprinting: To recognize unique characteristics of devices used in transactions which helps identify anomalies associated with automated tools or scripts.
- IP Geolocation and Anomaly Detection: To verify the legitimacy of transactions based on users’ IP geolocation data and flag anomalous transactions that diverge from normal user behavior.
- Artificial Intelligence: To identify subtle and evolving patterns associated with fraud, enabling improvements in the effectiveness of fraud prevention measures.
- Machine Learning: To prevent card testing attempts with predictive analysis, identifying potential risks and trends before they escalate.
- Biometric Authentication: To authenticate users by adding an extra layer of security in the form of biometric authentication methods, such as fingerprint or facial recognition.
- Encryption and Security Protocols: To secure communication protocols, safeguard sensitive data during transactions and prevent unauthorized access.
- Address Verification System (AVS): To match the billing address with the address on file with the issuer.
- 3D Secure Authentication: To request the cardholder to authenticate the transaction with a one-time password (OTP) or other additional verification steps.
- Tokenization: To replace cardholder data with random tokens, denying attackers a chance to engage in fraudulent activity even if they access the tokenized data.
- Real-Time Monitoring and Red Flags: To trigger automated alerts for suspicious orders, enabling prompt intervention.
- Audits and Updates: To identify potential areas of improvement and keep software, security protocols, and fraud prevention measures up-to-date.
- Collaboration: To collaborate with industry peers and facilitate information sharing on evolving threats to effectively respond to emerging card fraud tactics.
Using CAPTCHA for Security
CAPTCHA, an acronym for Completely Automated Public Turing test to tell Computers and Humans Apart, is a key component in the fight against automated, bot-driven cybercrime.
By requiring users to prove they are humans, especially at the time of account creation and online transactions, CAPTCHAs add an additional layer of authentication. They stop automated bots and scripts from executing large-scale activities, thereby protecting user accounts against fraudulent transactions, and unauthorized access.
The Benefit of Requiring CVV Numbers
CVV (Card Verification Value) or CVC (Card Verification Code), a three- or four-digit number of a credit card, can be used as an additional authentication layer for digital transactions. CVV numbers are neither stored in magnetic stripes nor embossed on the card. This makes it difficult for attackers to complete fraudulent transactions without providing a correct CVV number. As a result, the risk of unauthorized purchases is reduced, which helps protect consumers and businesses against financial losses.
Address and ZIP Code Verification
Address and ZIP Code Verification also add an extra layer of security to online transactions. When the billing address and ZIP code provided by a user do not match with the information on file with the card issuer, businesses can effectively prevent imminent fraud. This strengthens the overall security of transactions and reduces the risk of unauthorized purchases.
How Effective is Your Current Card Testing Fraud Prevention Strategy?
Fighting card testing fraud requires a comprehensive strategy. It involves the use of latest digital technologies, such as machine learning and behavioral analytics, to identify anomalous transaction patterns and improper user behaviors. It also includes additional layers of authentication such as CVV numbers, address verification, and real-time monitoring.
By conducting a thorough assessment of their current prevention strategy, businesses can gain insights into the existing strengths and weaknesses, and make informed adjustments to enhance its efficiency. Consider assessing your strategy on the following parameters:
- Incident Monitoring and Reporting: The number of detected incidents, their nature, and the effectiveness of the response mechanisms in place.
- Transaction Analytics: Whether the system is able to effectively distinguish between legitimate transactions and those indicative of bad actors.
- False Positives/Negatives: Balance between rate of false positives (legitimate transactions flagged as fraudulent) and false negatives (fraudulent transactions not detected).
- User Experience: If the strategy results in a high number of false positives or introduces friction into the customer journey, it may need refinement.
- Adaptability to Emerging Threats: Ability to dynamically adjust to evolving fraud tactics and techniques.
- Technology and Tools: Are the technology and tools used in the prevention strategy up-to-date? Are they capable of leveraging advanced technologies, such as machine learning and behavioral analytics, to stay ahead of evolving fraud tactics?
- Collaboration and Information Sharing: To what extent does the strategy allow collaboration with industry peers and participation in information-sharing networks.
- Compliance with Industry Standards: How well the strategy aligns with industry standards and compliance requirements.
- Continuous Improvement Practices: Does the strategy support continuous improvement through regular reviews and updates?
Find out more about proactive card testing prevention from Arkose Labs.


