In this blog post, we will review the various steps of account takeover fraud, the economics around it, and the nuance of the attack in various industries.
Here’s what we’ll cover:
- Part 1: Overview
- Part 2: ATO attacks in eCommerce, travel, and media
- Part 3 – ATO attacks in fintech and banking
- Part 4 – Targeted ATO attacks
Part 1: Overview
The steps of the account takeover attack
The techniques fraudsters employ to take over an account largely depends on the targeted site and goals. If the attacker’s goal is to take over accounts of an eCommerce or travel website, the most cost-effective solution will be to acquire a list of stolen credentials. This can be done on the darknet, the list consists of email addresses and password. The attacker will replay the credential against various targeted website. If the target is a financial or banking website, a different technique involving social engineering (phishing) may be necessary as these websites typically do not use email addresses as the username. Lastly, if the attacker’s goal is to take over a system administrator account or is targeting an individual, then a dictionary attack may be in order.
A successful attack always consists of 3 major steps:
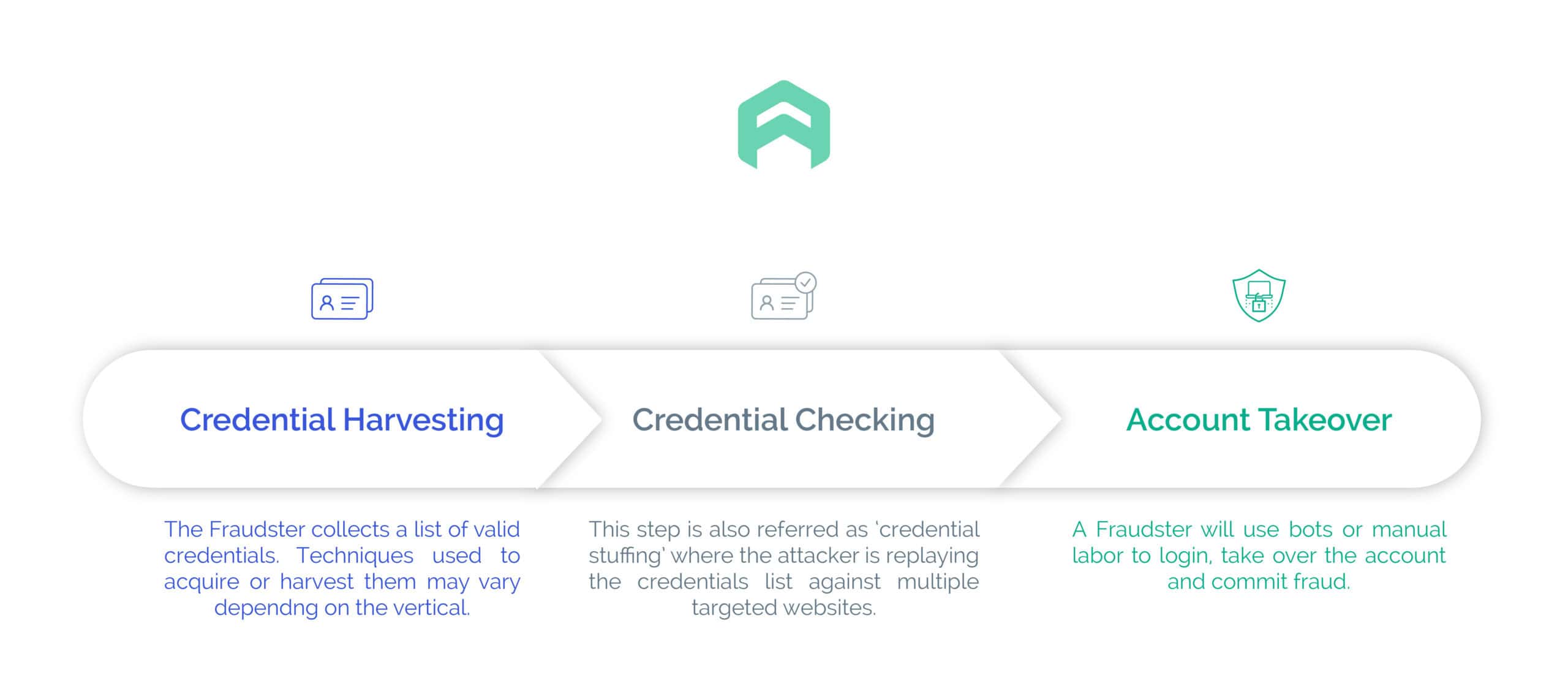
The same individual or group may carry out the different steps of the attack. But typically, an individual or group specialize in a specific step and participate in the whole economy surrounding the process.
Credential harvesting
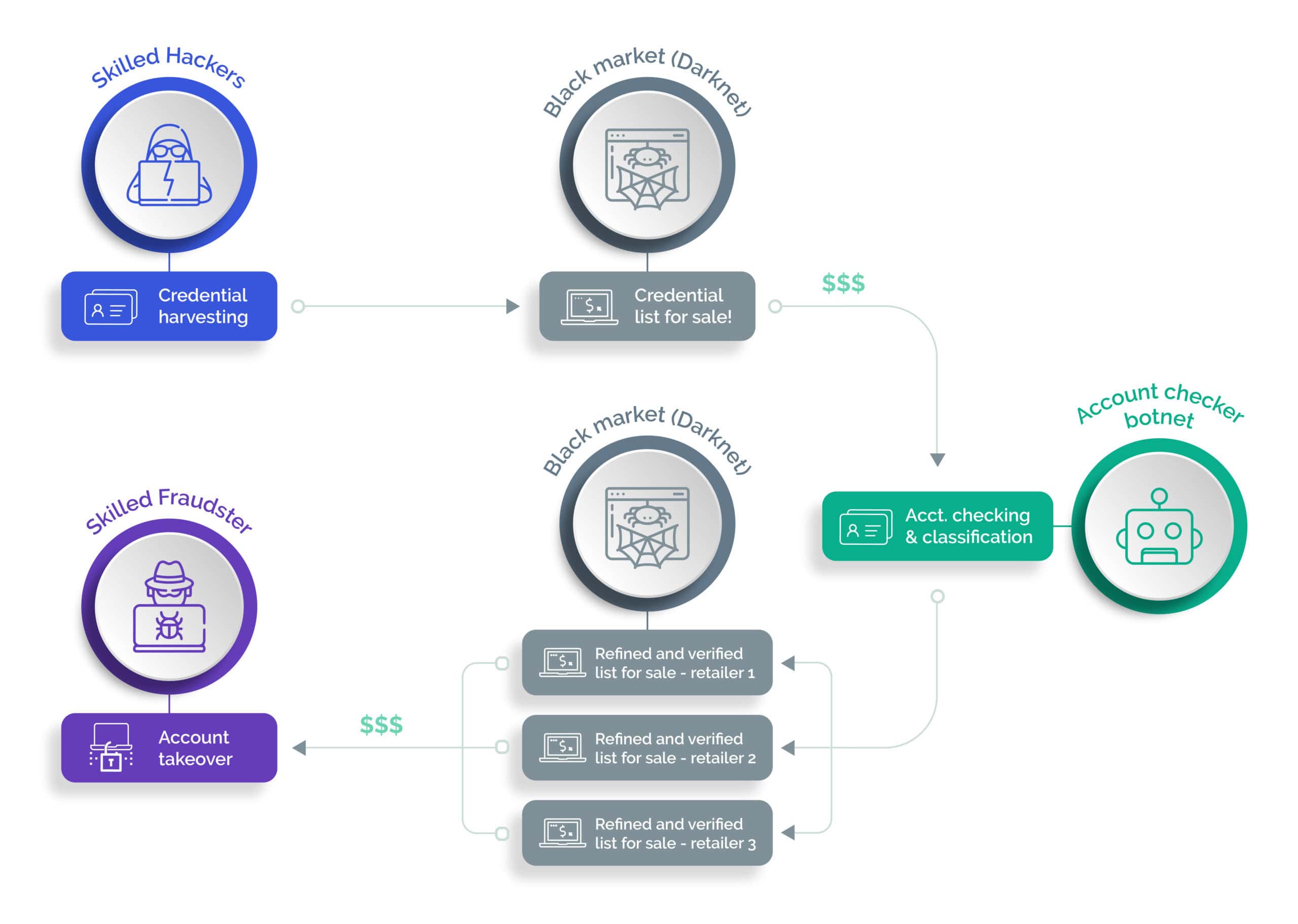
Stealing and harvesting credentials requires the most advanced hacking skills. Credentials are typically stolen using various schemes ranging from phishing attacks, malware attacks, or exploiting various security vulnerabilities a company may have. The harvested list resulting from the attack is typically put up for sale on the public or dark internet. This is a very lucrative business since a single list may be sold multiple times over several years. Of course, the actual value of a list may go down over time.
Added value account checking
Next, comes the account checking process; groups specializing in checking accounts buy the lists and replay the credentials against multiple targeted websites. The most effective way to check a large list of accounts at scale is to use a botnet.
This step actually requires far less skills than the previous one. Tools like Sentry MBA or similar give easy access to a botnet. These turn-key, easy to use solutions come with tutorials and even sometimes support. One doesn’t need to be an accomplished hacker to carry out this stage of the attack at scale. Simply enter the list of stolen credentials into the tool, configure your proxies, define your target and you’re ready to go. More skilled attackers develop and build their own botnet, to more effectively deal with any bot or fraud detection solutions protecting a web site. The tool will attempt to login against the targeted web site using the credentials and provide a report of the valid and verified username and password combinations.
The resulting “refined” list is then typically put up for sale again on the darknet. The value of these refined lists fluctuates depending on the possible ROI associated with them. For example, verified lists for a banking or eCommerce site known for its very good loyal customer reward program, have a much higher value than lists for sites that offers more basic services.
Recommended eBook: Busting the ROI of Fintech Fraud
Account takeover
Lastly, a fraudster will acquire the list of verified accounts. These accounts may be sold separately but they are more commonly sold in bundles depending on what access, data or potential monetary value is attached to them. I'll go over how these accounts are exploited in the next sections. The diagram below shows the various steps of the process and the trading points.
Part 2: ATO attacks in eCommerce, travel, and media
Where credential lists come from
In the first part of this post, we talked about the entire logistics of an ATO attack process and the different steps and actors involved. In this section, we’ll focus more particularly on ATO in the eCommerce and travel industry. First of all, how do lists of credentials make it to the darknet? Remember those stories about data breaches you read in the news on a regular basis?
Here are a few notable examples or data breaches that fueled these lists over the years:
- December 2009: A company that developed applications for social media sites leaked 32 million username and plaintext passwords
- April 2011: Up to 77 millions user accounts from an entertainment company were compromised
- October 2013: A software company revealed that 130 million user records were stolen
- October 2017: A web services provider revealed that 3 billion accounts (in effect their entire user database) had been breached
- March 2018: An apparel company reported a data breach of over 150 million accounts
- December 2018: An online platform reported a data breach that affected 100 million users
- July 2019: Capital One reported a data break of over 100 million customer accounts and credit card applications
- September 2019: Zygna reported a database breach of approximately 200 million users
- April 2020: Zoom revealed that over 500 million account credentials were sold on the dark web
- July 2020: 130 Twitter accounts of major US politicians, celebrities, and high profile personalities were breached to swindle $120,000 worth of bitcoin
In all of the above cases, the attack involved several steps and took advantage of various security vulnerabilities of the targeted network and system. If you want to know if your account has been compromised as a result of a breach, check out Troy Hunt's site Have I Been Pwned. The site reports over 10 billions breached accounts from 460 different websites. I recently verified that 2 of my personal accounts have been part of multiple breaches, one of them was recently used in an extortion fraud scheme.
It’s all about added value
Account checkers constantly acquire these lists and re-play them against numerous eCommerce and travel web sites worldwide. Why do they do this? According to a poll, nearly 59% of people use the same password everywhere so that it’s easier to remember. So the chances of finding a valid account are quite high. Because of the large number of players in the account checking business, there is some competition and quality of the account verified must be guaranteed so as to:
- be able to resell a list of verified credentials at a high price,
- maintain a reputation, a seller's ability to make future sales depends on it.
Simply providing a list of verified account for a given web site is therefore not enough. Most account checkers will provide added value services by categorizing the accounts. Categorizing an account requires the attacker to login to the site and check what value can be extracted from it (personal information, credits, reward points, gift cards, registered credit cards). This part of the process may be automated using custom scrips deployed on a botnet or done manually depending on the level of quality the fraudster is looking to attain. The more information available about the account, the more marketable it will be, and the higher the revenue.
Recommended Whitepaper: The Ultimate Guide to Bot Prevention
Account takeover attacks and fraud
Next, a fraudster will buy the refined and categorized account lists, complete the process of taking over the accounts and use them for the various schemes including:
- Spam / fake reviews with the potential goal of discrediting a particular product or brand
- Change the password, address and make a purchase using the credits/reward points/gift cards available on the account
- Collect personal information (home address, phone number, email address) and resell the information on other forums
- An account for video streaming providers will be sold for a fraction of the price of the service
Part 3 - ATO attacks in fintech and banking
Credential harvesting logistics
We talked about how an account takeover attack happens in the eCommerce and travel industry. In this section, we’ll review how ATO happens in banking and fintech. Because of the more secure nature of the space, the harvesting step is more complex. The potential gain is much higher. The extra cost still makes the overall operation profitable. That is until you start disturbing the ROI with Arkose Labs’ advanced fraud detection solution.
The great majority of credential data breaches happen on media, entertainment, or eCommerce web sites. These companies typically use email addresses as the username. Fintech and banks rarely use email addresses. Building these lists of credentials to carry out the credential stuffing attack, therefore, requires a lot more finesse and skills. Two avenues the attacker can go:
- go for a phishing attack to attract the victim into a malicious “look-alike” web site, or
- go for a variant and more complex of it to entice the user to install a malware on his computer to log keypresses.
Phishing attack
All of us have received one of those emails that seem to be coming from a bank (sometimes not even one we’re banking with) asking to click a link and login because there is an important message or issue that requires our immediate attention. According to reports in 2016, 1.09 million phishing attacks were detected. Of course, if you pay attention, you’ll see that the URL you’re going to is close enough to the real deal but your trained security expert eyes won’t be fooled. But what about less computer-savvy people? Once you log in to the fake bank website, your credentials are recorded into the attacker’s database and you are redirected to the bank’s real login page. Most users won't think much of such a glitch, assume that something went wrong and attempt to log in again.
Malware campaign
To prevent malware, the first step as a user is to make sure you have a reputable antivirus running on your machine. If you’re reading this, you’re likely a security professional and that’s a pretty obvious statement. But that’s definitely not something obvious for my parent’s generation. Also, don't visit questionable websites. Don’t click on links or download attachments you received from questionable emails. Again, obvious for us professionals but not so much for our senior citizens. I once received a phone call from a “Microsoft support center” who wanted to kindly inform me that they had detected malware on my Windows computer and offered to guide me through removing it by downloading a software. That of course raised all sorts of red flags in my head but I decided to play along for a little while. When I mentioned that my AV software was up to date and I was asking too many questions on what the malware was doing and why I needed the software, the guy quickly explained that if I didn’t listen and act quickly, I would lose all my data and there would be nothing he could do to help me. At that point, I decided to let him know that I only owned Apple products and hung up. Attackers can certainly be persuasive. Once the malware is installed on a system that is not protected adequately, it will listen for keystrokes as the user is logging into various web sites. The credential collected will be reported to a database the attacker owns.
Account takeover attacks and fraud
Once the credentials are acquired, the attacker will verify access to the accounts using a botnet (Sentry MBA or similar tool), if the list is very large. Or simply do their process manually to stay under the radar. The harvester may use these accounts to commit fraud or resell them online to the highest bidder. Fraudsters use compromised accounts in a variety of ways:
- Account Draining: Fraudsters use stolen identity credentials to take complete control of financial accounts. The accounts are drained of funds, and the money is often “laundered”, making it difficult to trace the theft.
- Money Laundering: “Dirty” money (the proceeds of crime) is passed through a complex series of bank transfers, obscuring the origins of the funds to make it appear legitimate. The “clean” money returns indirectly to the criminal.
- Money Muling: Money muling is a form of money laundering where fraudsters either recruit legitimate customers to transfer dirty money or take control of legitimate active or dormant accounts and use them to transfer funds.
- Credit Applications: Stolen identity data is used to make fraudulent credit applications. Compromised account data might be held for months before fraud is committed, making it difficult to identify the source of the breach.
Part 4 - Targeted ATO attacks
The attacks discussed in the previous sections are not targeting a specific individual or type of account. The attack is broad and the goal of the attacker is to take over any account and exploit whatever valuable information that may come with it. Some attacks however aim to target specific people (for example a celebrity) or “power user” accounts (a cloud service or network equipment admin account). When it comes to taking over these special sorts of accounts, the techniques used will most of the time be radically different from the ones seen in the eCommerce, travel, fintech, and banking industry. Replaying published lists from the darknet may be impractical and costly due to the sheer number of stolen credentials available on the black market. A phishing attack may be impractical with little chance of success. When the targeted account only relies on a password, is not set up with multi-factor authentication, or a network access server (RADIUS), the attacker may be successful using a dictionary attack.
Network administrator accounts
Most networking equipment comes with default admin usernames and passwords. Unfortunately, not everyone is careful enough to change it with a strong one or set up a RADIUS server linked to a corporate user database to manage the account. Doing a quick search on Google gives you several links to pages that list the default credentials of various vendors networking equipments. These are typically published to raise awareness and help network administrators build a script to automatically detect vulnerable access points. Unfortunately, attacker also use these wise advices. If an attacker is able to gain access to a router, they may be able to reroute the traffic of a web server to an alternate location. Or they may simply shut down access to the network and in effect, deny access to all users. This type of attack would have a significant impact on the site’s reputation.
System administrators accounts
Cloud services don’t generally have a default password. Site administrators for a small to medium-sized businesses may not always be well versed in security best practices and only rely on password-based authentication methods. Most people, even security professionals, may sometimes use easy to remember passwords. Often, the password consists a word available in the dictionary, a combination of words with some letters swapped with numbers or an easy to execute keyword sequence like “qwerty”. A quick Google search gives a list of the most common passwords, which can be used to build a word list. The list can then be used in a brute force attack to take over the targeted account. If the attacker successfully “guesses” the password, he will gain access to the cloud services. Depending on the access rights associated with the account, the attacker may be able to do all sorts of damages, including deny access, deface the web site or exfiltrate data.
Specific individual account
Celebrities' social media accounts are regular targets of attacks. Some attackers may hold a grudge on someone and decide to embarrass or discredit them by taking over their social media accounts. Again, a dictionary attack would be a logical step of the process.
The bottom line on account takeover attacks with Arkose Labs
Here you have it, a 360 degrees overview on the various techniques used by attackers to take over accounts by industry and use cases. All accounts are at risk and fraudsters will go above and beyond to reach their goals. Don’t wait for the attack to show up before deciding to protect a login endpoint. Simply apply the same level of protection to all critical endpoints, whether they have been attacked in the past or not. Because you can’t expect your users to be security savvy, protecting all your login endpoints with a strong fraud detection product that offers good user experience like Arkose Labs is a must to prevent account takeovers and preserve the reputation of your business. To see how we can help you prevent these attacks, book a demo with a specialist today.
The Ultimate Guide to Account Takeover Fraud
- Part 1: Overview
- The steps of the account takeover attack
- Credential harvesting
- Added value account checking
- Account takeover
- Part 2: ATO attacks in eCommerce, travel, and media
- Where credential lists come from
- It’s all about added value
- Account takeover attacks and fraud
- Part 3 - ATO attacks in fintech and banking
- Credential harvesting logistics
- Phishing attack
- Malware campaign
- Account takeover attacks and fraud
- Part 4 - Targeted ATO attacks
- Network administrator accounts
- System administrators accounts
- Specific individual account
- The bottom line on account takeover attacks with Arkose Labs

