What is Account Takeover?
Account takeover is an attack where bad actors use devious tactics, such as stolen customer information or credential stuffing, to gain unauthorized access to a user's online account. Once compromised, they are used as launchpads for criminal activities like identity theft, unauthorized transactions, money laundering, and more.
Account takeover attacks are a serious threat to personal and financial information, and expose businesses and users to high risk.
How Account Takeover Happens
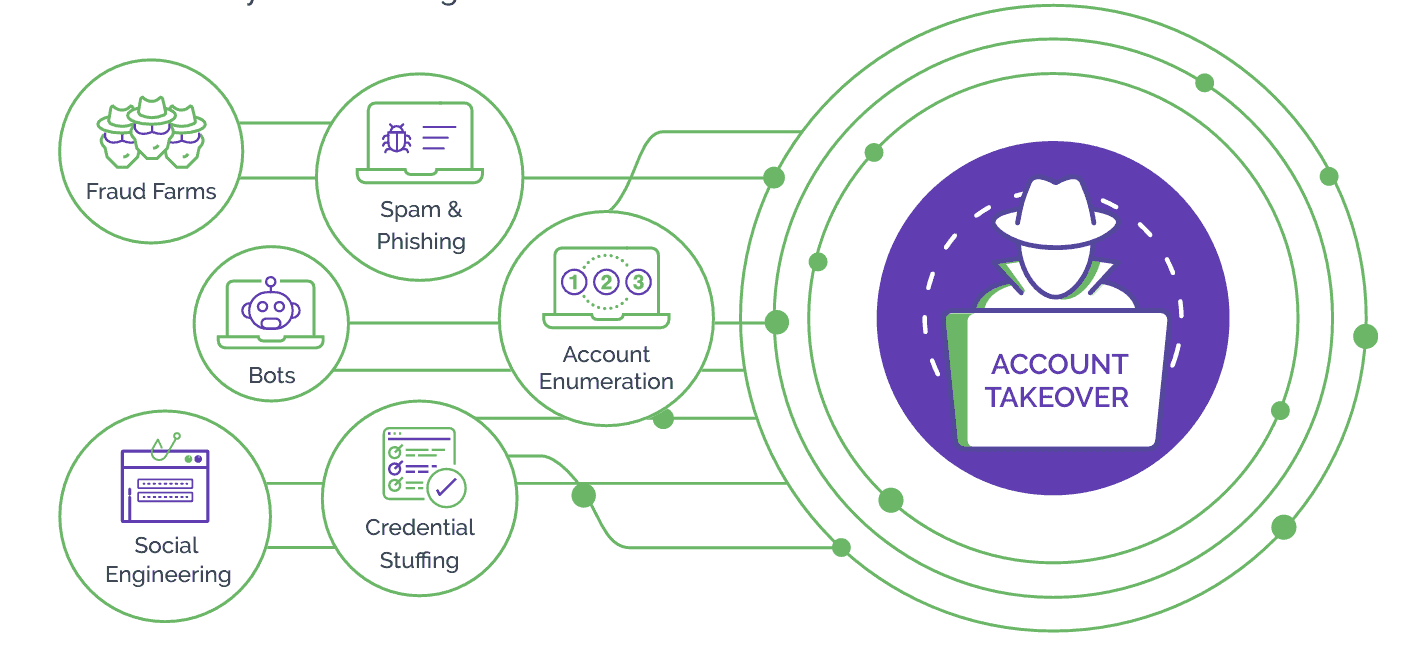
ATO has grown to become a major headache for businesses across all industries, including fintech, social media, and technology. Banking and other finserv sectors, for example, are particularly lucrative for bot-driven attacks because they involve the handling of large volumes of sensitive financial data, making them attractive targets. Here are some common key steps:
- Credential Harvesting: Bad actors use advanced techniques such as scraping, phishing attacks, purchasing user credentials exposed in data breaches and sold on the dark web, exploiting weak passwords, targeting system security vulnerabilities, using keyloggers, and other means to access login information like email addresses, usernames, and passwords. Attackers also use social engineering to trick individuals into sharing personal and financial information over the phone or through fake websites.
- Account validation: The malicious actors then check the stolen credentials via a business’s website to arrive at verified username-password combinations. They typically use automation to speed up the process and achieve attacks at scale.
- Account takeover: Once verified lists are obtained, fraudsters may choose to monetize them by selling them to third parties or launch successful account takeover attacks by filling in login forms on websites, outsourcing ATO attacks to low-cost human attackers, or completing high-value attacks themselves.
The Role of Bots in Account Takeover Attacks
Bots have become a popular choice among attackers for automating attacks. In the context of account takeover, cyber criminals use bots for credential harvesting, validating username passwords, gaining illegitimate access to customer accounts, and evading detection. Automated scripts and bots reduce manual effort spent in an attack, thereby enabling attackers to launch wide-scale attacks quickly. Malicious bots can be programmed to perform specific tasks such as brute-forcing, credential stuffing, and password spraying to quickly create databases of valid username-password combinations.
Since bots are easily and cheaply available, they allow cybercriminals to launch massive attacks with the lowest possible investment. Further, bots can operate around the clock without any breaks. As a result, attackers can execute automated bot attacks non-stop and at a speed and volume that is impossible for a human to achieve manually.
Attackers also employ bots in phishing campaigns to trick users into revealing their login credentials or installing malware. Intelligent bots that can mimic human behavior are often deployed to fool security measures.
A Typical Account Takeover Scenario in Banking
The scenario described below explains how an attack usually takes place in the banking sector. An attacker initiates the ATO process by harvesting a user’s account credentials. This could be through phishing emails that mimic official communication from the bank, or using keyloggers to capture the login details.
With the acquired login credentials, attackers access the victim's online bank account. To evade detection, attackers may choose to log in during the off-peak hours or use proxy servers that hide their true location.
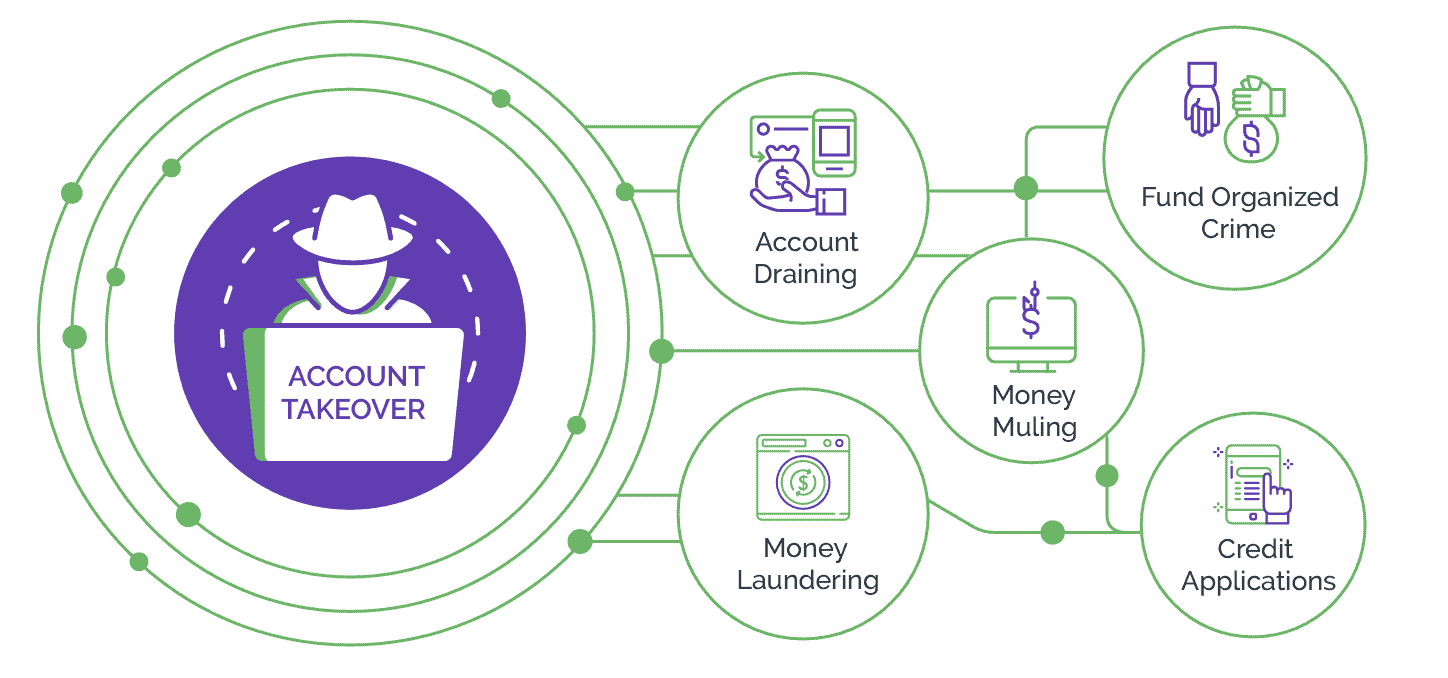
Upon gaining unauthorized access, attackers can transfer funds, make purchases, apply for credit cards or loans, or change profile settings, among other malicious activities. To obstruct communication with the genuine account holder, attackers may modify the contact information. The delay in detecting the attack allows enough time for the attacker to move ahead undetected.
How Businesses are Impacted
ATO attacks can have far-reaching consequences for businesses, especially financial services and banking institutions. In addition to direct financial losses due to fraudulent transactions carried out through compromised accounts, businesses stand to incur covert losses. These include account restoration, extra burden on customer support services, investment in additional security measures, and operational disruptions. Further, compromise of user account security can damage the reputation of the business and lead to non-compliance with regulatory requirements.
Affected customers may lose trust in the business and choose to take their business to a competitor, causing potential loss of revenue and the ability to acquire new customers.
The aftermath of an attack in the financial services and banking sector can be particularly severe, as these are highly regulated industries. While consumers face financial losses, banks and other financial institutions may invite regulatory scrutiny, potential legal action, and the costs associated with investigating and remediating security breaches. Erosion of market confidence can affect their stability and competitiveness in the market.

Signs of an Account Takeover Attack
Protecting the business and consumers from attacks is crucial for any organization. Through constant vigilance, organizations can proactively identify ATO attempts to inform timely preventive action.
Common signs include:
- Unusual Activity: Activity that deviates from the norm, such as login attempts from different locations or devices, multiple failed login attempts, or unauthorized changes to settings
- Password Changes: Notifications or confirmation emails to customers about password changes that they did not initiate
- Transactions: Unrecognized and unauthorized financial transactions, withdrawals, or transfers
- Strange Notifications: Email notifications that are not in line with the standard communication format from the service provider, request disclosure of sensitive information, or instruct recipients to click on links
- Lock-out: Legitimate users locked out of their accounts due to unauthorized password changes or multi-factor authentication that is enabled without their knowledge
- Account Access Timing: Divergence from usual access times, including unusual times or odd hours when the legitimate user is unlikely to be online
- Recovery Email Changes: Alterations to email forwarding settings or changes to the recovery email address
How Businesses Can Mitigate the Risk of ATO
Given the significant impacts on businesses and consumers, enterprises must implement robust security measures to mitigate the risk of ATO. Proactive measures may include enforcing strong password policies, using multi-factor authentication, regularly monitoring user activity for anomalies, employing advanced bot detection systems, and implementing automated alerts for suspicious behavior.
Creating awareness about phishing threats through security awareness training and staying informed about the latest cybersecurity trends and vulnerabilities can prove useful in safeguarding against cyber threats.
Strategies to Prevent Account Takeover Attacks
Businesses must create a comprehensive security strategy and adopt a multi-faceted approach to address current and emerging threats. A combination of the strategies can help businesses create a more resilient defense and enhance safety of sensitive user information.
Some strategies that businesses may consider are:
- Multi-Factor Authentication (MFA): Adds an extra layer of security through text message or other verification to make it more difficult for attackers to gain unauthorized access. Requires users to provide multiple forms of identification, such as a password and a one-time code sent through SMS to their mobile devices.
- Strong Password Policies: Requires users to create strong, unique passwords, while avoiding use of easy-to-guess information. Discourages reuse of passwords. Prompts users to update their passwords periodically.
- Continuous Monitoring: Helps analyze user behavior and activity for anomaly detection, such as sudden changes in login locations or multiple failed login attempts, to trigger alerts for further investigation.
- Device Recognition and Risk-Based Authentication: Helps recognize and authenticate devices frequently used by genuine account holders. Risk-based authentication assesses the risk level of a login attempt based on factors like location, device, and behavior, allowing for adaptive security measures.
- Email Authentication and Monitoring: Uses email authentication protocols to prevent email spoofing and phishing attempts.
- Security Audits: Conducts routine security audits and penetration testing to identify vulnerabilities in systems and applications. Helps address and patch the weaknesses to strengthen overall security.
- Incident Response Plan: Outlines the steps to be taken in the event of a takeover or security breach to minimize the impact of an attack and facilitate a swift, effective response.
- Lockout Policies: Temporarily restricts access after a specified number of failed login attempts. Slows down attackers’ ability to guess passwords and prevents brute-force attacks.
- Secure Coding Practices: Ensures that web applications and online services are built with secure coding practices in mind.
- Educational Programs: Educates employees and users about the risks of phishing, social engineering, and other tactics used in attacks to help recognize and avoid potential threats.
Steps After Detecting an ATO
Account takeover fraud can be devastating. Therefore, as soon as the telltales of an ATO attempt are detected, it is crucial to take prompt corrective actions that foil the attack and prevent further harm. Some key steps to follow are as described below:
- Isolate and Secure the Account: Immediately restrict access to the compromised account by locking it, changing the password, or temporarily disabling it until a thorough investigation is conducted.
- Notify the Users: Inform account holders about the attack. Provide clear instructions on the recovery process such as resetting passwords, enabling multi-factor authentication, and verifying recent activity.
- Investigate and Analyze: Determine the extent of the compromise. Analyze logs, activity, and forensic data to understand how the attack occurred, personal information accessed, and potential risk to other systems.
- Containment Measures: Implement measures such as closing potential security loopholes, updating software, and addressing any vulnerabilities exploited by the attacker, to contain the incident and prevent further unauthorized access.
- Forensic Analysis: Perform a forensic analysis to gather evidence about the attack and identify the methods used by the attacker.
- Communicate Transparently: Inform affected users, stakeholders, and relevant regulatory bodies about the incident and the measures deployed to address the problem.
- Enhance Security Measures: Use insights gained from the incident to improve overall security posture.
- Collaborate with Law Enforcement: Provide law enforcement agencies with the necessary information about the attack and cooperate in any investigation.

How Arkose Labs Helps Prevent Account Takeover Attacks
Arkose Labs helps global brands effectively prevent account takeover attacks with its innovative and adaptive approach to cybersecurity. Leveraging a combination of real-time threat intelligence, behavioral analysis, and risk-based authentication, Arkose Labs can swiftly detect suspicious activities and mitigate the risk of unauthorized account access.
Arkose Labs assesses the risk associated with each user on various factors such as device fingerprinting and geolocation. This information allows the system to identify potentially risky sessions and introduce the challenge-response authentication mechanism to differentiate between legitimate users and malicious actors. Good users, if at all they encounter the Arkose MatchKey challenges, find them fun and easy to solve, while scripts and bots of all advancement levels struggle to pass them. Arkose MatchKey challenges are highly resilient to modern optical vision technologies, which means even the most intelligent, human-like bots cannot solve the wide repository of these challenges.
Persistent malicious users continue to face a barrage of challenges that keep increasing in complexity. Even if seasoned attackers were to try to create automatic solvers for Arkose MatchKey challenges, they would end up spending weeks and months’ worth of effort – and still not be able to create any solver that can clear the innumerable variations of each challenge.
Effectively, Arkose MatchKey challenges increase the time, effort, and resources needed to execute the attack to such an extent that the attack becomes financially non-viable, with added expenses instead of any returns. The negative economics of the attack forces attackers to give up for good and abandon the attack, thereby ensuring future-proof protection for the business.
Backed by its 24x7 SOC support, actionable insights, raw attributes and the latest threat intelligence from its network, Arkose Labs helps its partners remain updated on and prepared for the latest cybersecurity threats. This ensures businesses can build a robust defense against account takeover attacks, while maintaining a superior user experience for legitimate users.
Want to learn more about how Arkose Labs can help stop cybersecurity threats? Learn about our account takeover protection solutions.







