Credential Stuffing vs. Password Spraying: What’s the Difference?
Credential stuffing and password spraying are two forms of brute-force password attacks frequently used by bad actors. These attacks are similar, but they also differ in some important ways. Credential stuffing and password spraying are among the most common types of cyber attacks used by malicious actors to gain unauthorized access to user accounts. These attacks are becoming increasingly popular because they are easy to execute and can yield a high success rate.
In fact, according to recent studies, up to 81% of data breaches can be attributed to weak or stolen passwords1. As such, it’s critical for businesses to understand how these attacks stack up and how each one can affect overall security.
What is Credential Stuffing?
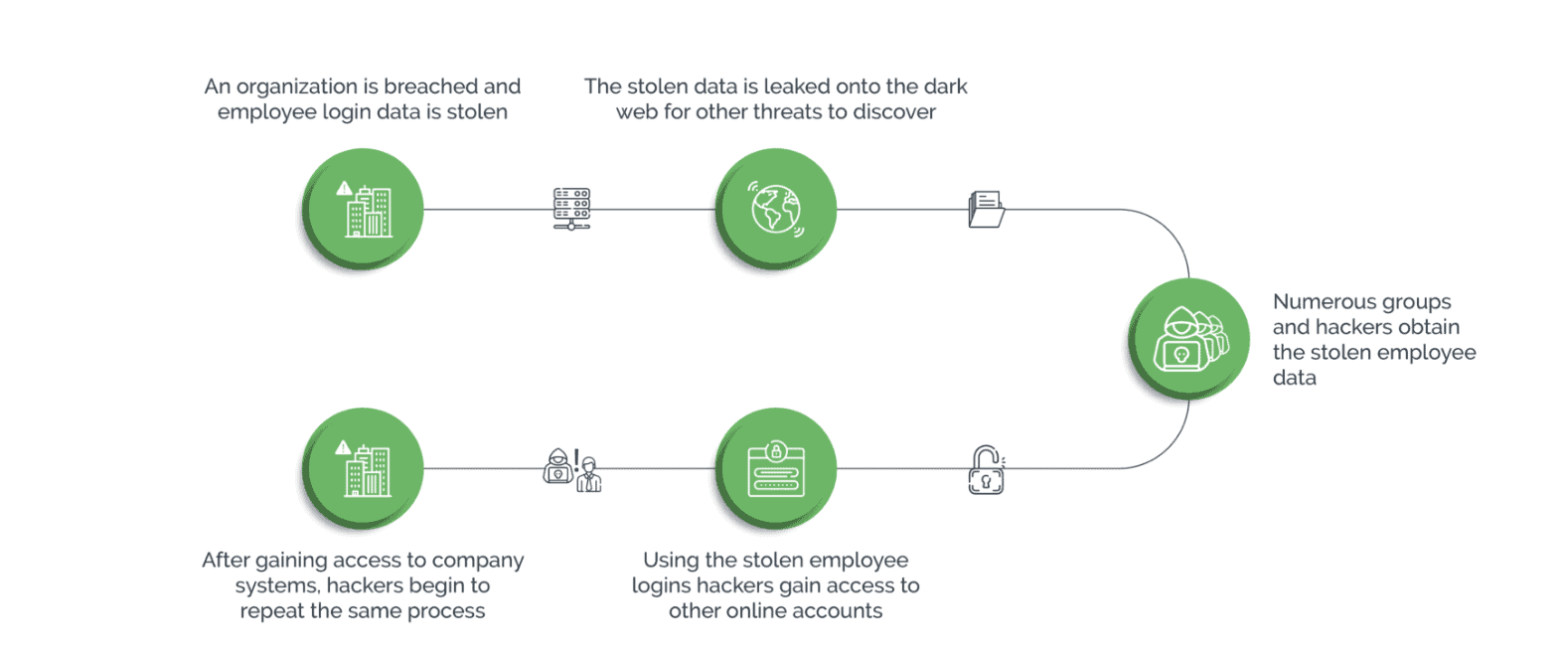
Credential stuffing is a cyberattack in which criminals use automated tools (or botnets) and stolen username and password pairs to break into systems and gain access to online accounts.
The popularity of credential stuffing can be attributed to:
- The prevalence of high-profile data breaches
- The ease with which criminals can purchase that stolen data on the dark web
- The fact that many people reuse login credentials across several websites. When credentials are compromised as a result of a data breach or a phishing attempt, cybercriminals use them to gain access to other accounts.
There are many downstream consequences of credential stuffing, including account takeover, identity theft, fraud, and more.
What is Password Spraying?
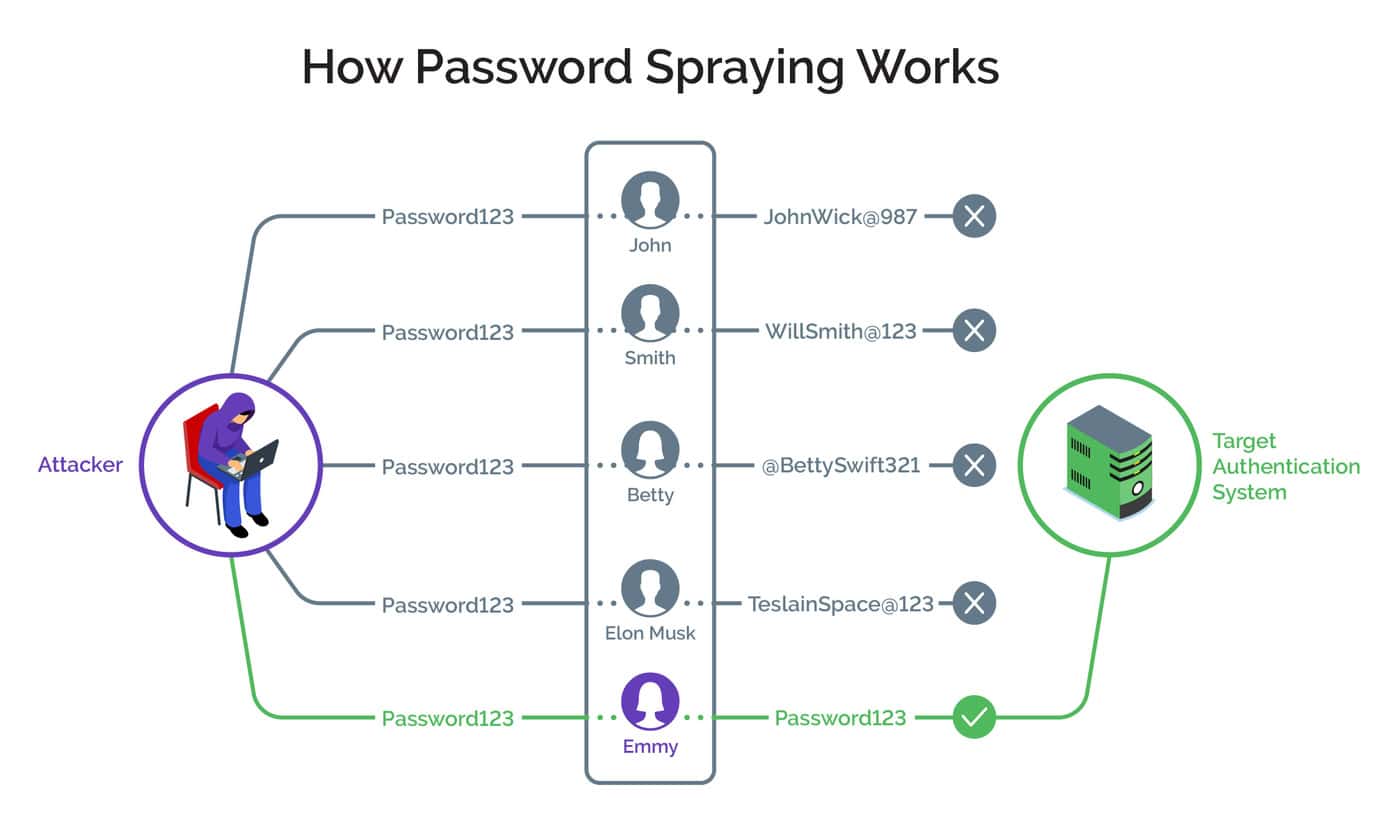
In password spraying, an attacker may test or ‘spray’ a common password—such as “123456” or “password1”—across several user accounts, hoping to find one that works. In this way, they avoid an account lockout, in which an account is locked after a predetermined number of incorrect login attempts.
Many people never change their devices' default passwords. Others set up simple, easy-to-remember passwords and use them for multiple accounts to avoid having to remember many passwords. This lack of rigor makes it pretty simple for criminals to hack into multiple accounts.
What’s the Difference Between Credential Stuffing and Password Spraying?
Credential stuffing attacks exploit genuine, stolen credentials to gain unauthorized access to other accounts. But, in password spraying attacks, criminals don’t have access to known credentials, so they test a commonly used password against several usernames to see what works.
Both of these types of brute-force password attacks can cause great harm to a business and are highly profitable for criminals.
How Password Attacks Harm Businesses
Credential stuffing and password spraying can lead to data breaches, financial losses, damage to a company's reputation, and a loss of trust from customers. In addition, businesses can face legal and regulatory penalties if they fail to protect their customers' personal and financial data.
How Criminals Profit
Criminals gain access to valuable personal information through credential stuffing and password spraying attacks. Once they know they have valid user credentials, they can steal sensitive data such as credit card numbers, social security numbers, and other details. This information is then sold on the dark web to other cybercriminals, who use it for identity theft, fraud, or other malicious purposes. Criminals also use compromised accounts to launch further attacks against businesses or their customers, leading to even greater financial losses and reputational damage.
Other Kinds of Password Attacks
In addition to credential stuffing and password spraying, there are many other kinds of password attacks that organizations should look for. Some of the most common include:
- Brute-force attack: This type of attack involves trying every possible combination of characters until the correct password is found.
- Dictionary attack: In this attack, hackers use a pre-built list of commonly used passwords to try and gain access to an account.
- Man-in-the-Middle attacks: In MITM attacks, phishing toolkits act as malicious reverse proxy servers for online services, showing users the same content as the target website while stealing credentials like MFA tokens and session cookies.
- Phishing attack: This attack involves tricking users into revealing their login credentials through fake websites or emails.
- Keylogging attack: With a keylogging attack, hackers install software on a victim's computer to record their keystrokes and gain access to their login information.
All of these attacks can be conducted in various ways, and businesses must take steps to detect and prevent them.
Arkose Labs $1 Million Credential Stuffing Warranty Guarantees Success Against Volumetric Credential Stuffing Attacks
Detect and Prevent Credential Stuffing and Password Spraying
Although credential stuffing and password spraying are separate attacks, they are similar, and they can be prevented using similar techniques. The best practices listed below are just a few ways you can protect your company from attacks that involve credential stuffing and password spraying.
Multifactor authentication (MFA): MFA adds an extra layer of security to the login process, making it more difficult for automated attacks to succeed. While it is not the only answer, MFA is an essential part of blocking automated attacks.
Account Lockout: An account lockout works by locking user accounts after a predetermined number of failed login attempts. It is effective for thwarting automated attacks that use multiple IP addresses.
CAPTCHA: While traditional CAPTCHAs are mostly ineffective against automated attacks, Arkose Labs' MatchKey Challenge is the strongest CAPTCHA ever made. MatchKey's dynamic attack response adapts to attacks in real time, making it impossible to beat.
Logging: Logs can be used to find unusual things, like suspicious activity around login attempts or a lot of data transfers in a short amount of time. Logs can also be used to track down malicious activity and trace the source of the attack. Additionally, logs provide organizations with an audit trail that can be used for forensic analysis in the event of an attack.
Disallow email addresses for usernames: Require users to create a non-email address username.
Disallow common passwords: Get a list of the most common passwords and disallow those passwords. When a user tries to use one of the disallowed passwords, prompt them to use something less common. Encourage users to use a unique password for every online account or system.
Use a firewall: Web application firewalls (WAF) detect botnet-related anomalous traffic. A firewall can stop password spraying, credential stuffing, and other password attacks that use bots.
Conclusion
Both credential stuffing and password spraying are common forms of brute-force password attacks that can lead to data breaches, financial losses, reputational damage, and the loss of customer trust, among other negative consequences.
A robust bot management solution, like Arkose Labs, provides the best defense against all types of password attacks. Arkose Bot Manager sits on login and registration flows, which are highly targeted by bad actors. It provides real-time attack deterrence by delivering dynamic response orchestration tailored to the attack pattern. Legitimate users click right through, while bots and human fraudsters are stopped immediately. And Arkose Labs is the only vendor with a $1 Million Credential Stuffing Warranty.
Want to know more? Book a demo today!
Credential Stuffing
- Credential Stuffing vs. Password Spraying: What’s the Difference?
- What is Credential Stuffing?
- What is Password Spraying?
- What’s the Difference Between Credential Stuffing and Password Spraying?
- How Password Attacks Harm Businesses
- How Criminals Profit
- Other Kinds of Password Attacks
- Detect and Prevent Credential Stuffing and Password Spraying
- Conclusion