What is password spraying?
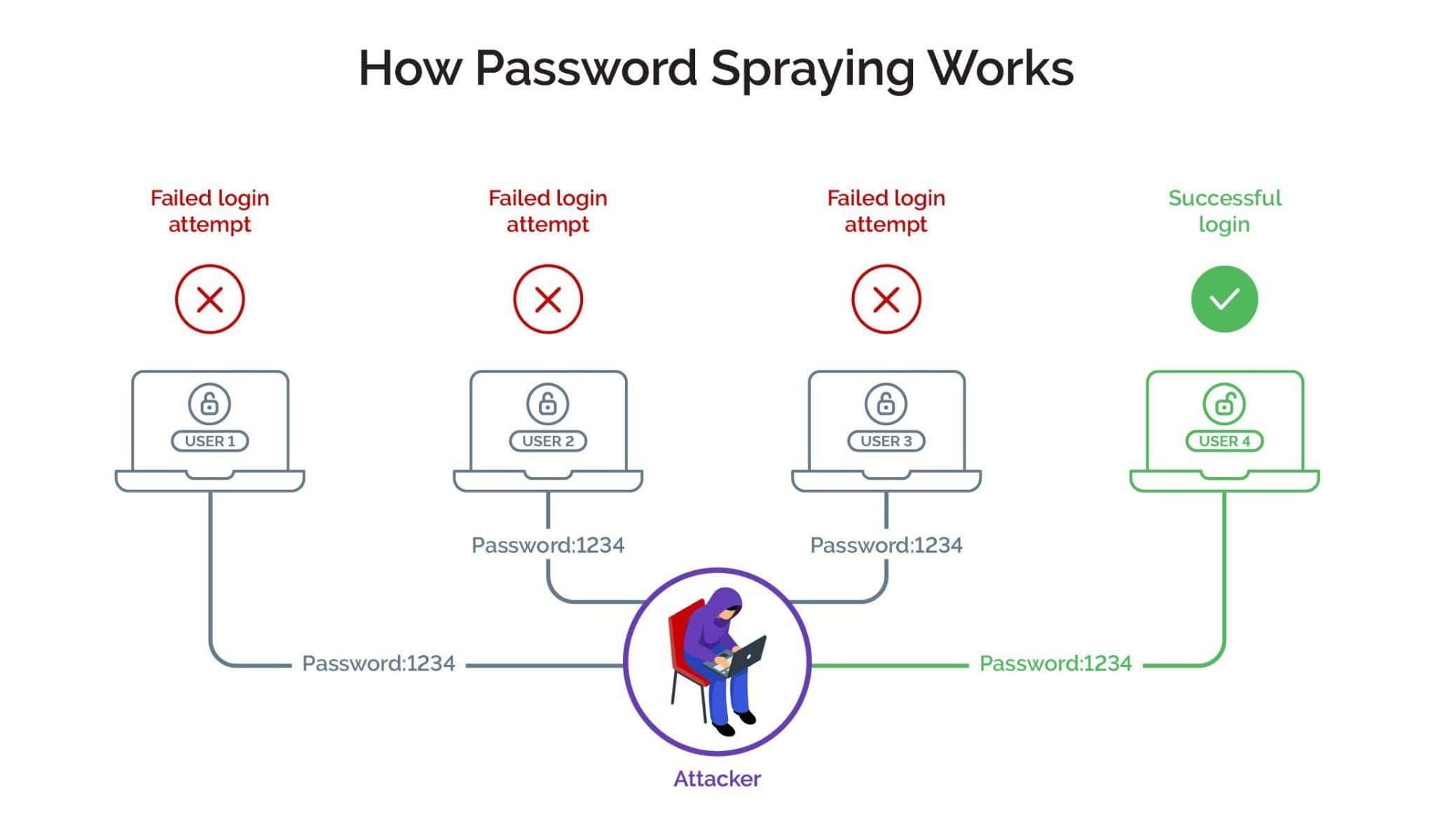
Password spraying is a type of cyberattack where attackers attempt to gain unauthorized access to accounts by trying commonly used passwords against many usernames. Unlike a brute-force attack that targets a single account with various password combinations or a credential stuffing attack that tries specific username/password combinations, password spraying involves trying a few passwords against a large number of accounts.
Multiple usernames, one password
Password spraying is often successful because it takes advantage of the likelihood that different users might have the same weak, commonly used passwords across different accounts on various websites and apps.
Many users, and businesses, do not change the default passwords of their devices. Default passwords are often widely known or easily discoverable, making devices vulnerable to unauthorized access. Additionally, to work around the problem of remembering too many passwords for their accounts across multiple digital channels, consumers often just simply create easy-to-remember passwords to repurpose and reuse them across accounts.
Not only does this lack of strong password policies increase the risk of a successful credential stuffing attack -- where attackers take a stolen set of credentials and inject them into other sites -- but those "easy" passwords tend to be used by other individuals as well. (Check out this list of the top 200 most common passwords.)
Types of password spraying attacks
Broadly speaking, there are two types of password spray attacks - rule-based and hybrid.
Rule-based attacks
Where attackers apply specific permutations to the passwords they are trying to guess.
Hybrid attacks
Where attackers use a combination of brute force attack and dictionary attack by adding combinations of numbers to all the words in a dictionary.
Login attacks on the rise
Password spraying is an easy method to identify user accounts for account takeover attacks. Use of automation helps scale up password spraying attacks and arrive at thousands of valid username-password combinations quickly.
Attackers aim to avoid detection by not triggering multiple failed login attempts for a single account, reducing the risk of an account lockout period due to too many incorrect password attempts. Bots with advanced capabilities and support are easily and cheaply available, which allows fraudsters to execute large-scale attacks with the least possible investment. The returns far outweigh the investment, which is one of the reasons why password spraying attacks are on a steady rise.
Motives behind the attacks
Monetizing password spraying attacks is pretty straightforward. Attackers can monetize their lists of valid username-password combinations by simply selling them off to third parties or on the dark web. They can choose to spend a little more effort to categorize the hacked accounts according to their net worth, which enables them to fetch higher prices. For this, they take over the accounts and assess their worth and then put them on sale at a much higher price.
Cybercriminals can also steal the funds from the compromised accounts and use the saved information to carry out further downstream attacks.
Malicious actors also use phishing to extract a user's personal information. Using bots and advanced scripts to scale up password spraying attacks, black hat hackers are able to create databases of valid username-password combinations in no time that are then used to fuel account takeover attacks.
A successful business account takeover enables bad actors to exploit the compromised account at whim. In addition to the financial benefits by draining the funds from the account, fraudsters can access saved details such as email addresses from the compromised account to attack more users.
Protection from password spraying attacks
It is clear that businesses cannot afford to bear the brunt of automated attacks. However, current fraud defense solutions are limited in their scope and fail to provide the level of protection that digital businesses need today.
Identity-based solutions have been rendered redundant as fraudsters can access valid login credentials and impersonate good users. They can also hide their real intent and location using tactics such as IP spoofing and device obfuscation, among others. Data-driven solutions look for clear signals of ‘trust’ or ‘mistrust’ that have now been transmuted due to manipulation of digital identities, evolving consumer behaviors, and spoofing techniques used by fraudsters. This means signals are no longer reliable for risk-decisioning with certainty. Fraudsters use this knowledge to game the fraud defense mechanisms, which means that businesses are engaged in a cat-and-mouse game with the fraudsters.
Targeted friction for smarter authentication
Businesses cannot rely on obsolete or point solutions to fight password spraying attacks, as not only do they fail to provide the needed protection but can also add to the long-term costs. Instead, they need a long-term approach that can enable them to disrupt fraud and put a stop to these large scale attacks.
Arkose Labs adopts a zero tolerance to fraud approach, which helps identify suspicious activity while preserving user experience. The Arkose Labs solution shifts the attack surface to its network and instead of blocking any user - good or bad - it affords them an opportunity to prove their authenticity. The platform combines risk-based decisioning with intelligent step-up to clarify whether or not a good customer’s digital footprint has been corrupted through the following steps:
Real-time Analysis
Sophisticated, real-time analysis of incoming traffic looks for even the most subtle indicators of fraud. However, this does not involve collecting users’ sensitive data; instead it encompasses focus on behavior, device, and network characteristics and how they are connected.
Classify and Triage
Arkose Labs classifies and segments traffic based on the risk profile. The platform triages traffic on the basis of its likelihood of being a legitimate user, bot, or human sweatshop, and provides actionable intelligence to inform the system of any secondary screening required and the type of enforcement required.
Challenge and Interact
To understand the intent of traffic in a deterministic way, secondary screening must be paired with risk assessment. Arkose Labs’ custom enforcement challenges test high-risk traffic using interactive technology that causes all automated attacks to fail. Graduated risk-based challenges can also frustrate cyberattackers by increasing the amount of friction they experience, leading them to abandon their attacks.
Continuous Learning
Arkose Labs not only shares actionable insights and threat intelligence from a diverse client network but also offers 24x7 SOC support. We assist partners in comprehending the evolving landscape of spoofing attacks, enabling informed decisions, risk mitigation, and proactive defense against emerging threats.
To discover how Arkose Labs safeguards global enterprises against cyberattacks without compromising user experience, please contact us for a demo.







