Why Businesses Can’t Solely Rely on Multi-Factor Authentication
Authenticating customers at the login and registration point is critically important to digital businesses today. Businesses want to enable a smooth and seamless digital sign up or log in process, but also keep fraud out and make them safe for good users. Multi-factor authentication (MFA) can be an effective way to safeguard these touchpoints, especially in a world where passwords are reused and years of data breaches have exposed personal information for anyone who wishes to buy it.
In today’s environment, a simple username and password combinations are not enough to protect digital accounts. Attackers utilize automation to launch credential stuffing attacks at scale to validate username/password combinations and compromise user accounts. MFA is an authentication technique that is used as an additional layer of security for enhanced user account protection. It goes beyond the first-degree of authentication that most consumer-driven businesses have.
If you’re in the fraud and security space, you’ve likely been in many meetings on how to encourage customers to enable multi-factor authentication on accounts. While it is better than nothing, and a valuable tool to have in the security arsenal, there’s a good reason many security teams are looking beyond MFA to protect user accounts, such as incorporating passwordless MFA and utilizing contextual and behavioral contexts when analyzing digital traffic. Businesses need robust digital account security that complements (or even entirely replaces) MFA throughout the customer journey.
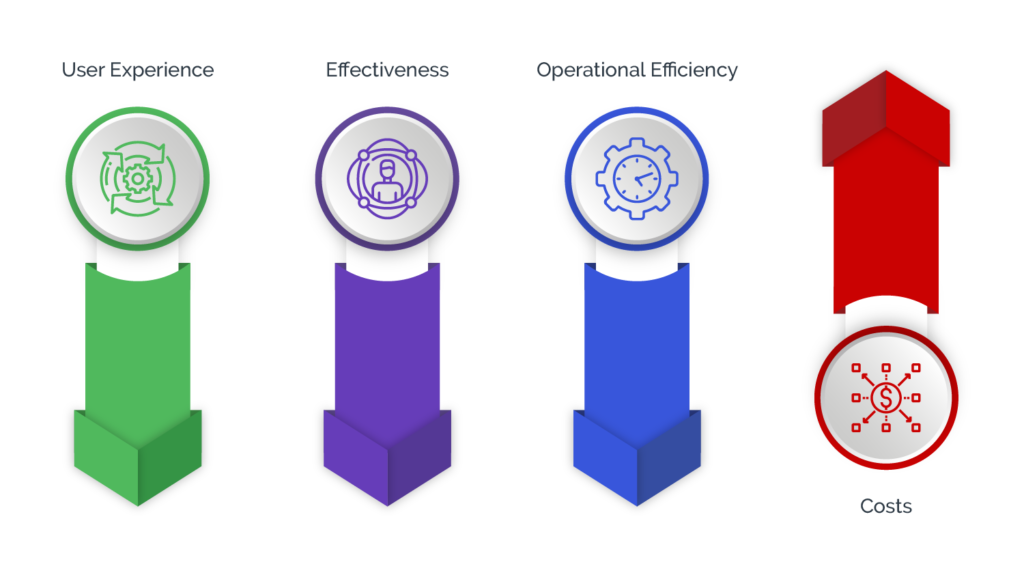
There are 4 primary reasons digital businesses struggle with MFA:
User Experience: MFA forces customers out of band and adds an additional layer of friction to the authentication experience. Furthermore, MFA typically has low opt-in rates by consumers, which limits its effectiveness. Businesses then are forced into the unenviable position of creating an opt-in strategy, which requires massive effort to educate customers on the value of turning on MFA or simply forcing it upon all customers. Overall, adoption rates for MFA are very low. They vary by business and industry but often are in the low single-digit percentage for adoption.
Effectiveness: Between opt-in challenges and new ways to bypass MFA, many security teams are unhappy with its overall effectiveness. Attackers use tactics such as SIM swaps to bypass MFA. This is where they contact a wireless carrier, convince the call center rep that they are the real owner of a phone number, and convince the call center rep to switch the SIM card linked to the real user’s phone number to one in their possession. They also have become very adept at using phishing and vishing tactics to get users to give them MFA codes.
Operational Efficiency: Relying too much on MFA can create significant operational inefficiencies. For one, it requires a complex integration process in order to enable MFA at scale. This includes both upfront investment, such as licenses and hardware requirements, as well as ongoing maintenance costs.
Costs: Finally there are significant costs associated with MFA tokens. The sending of one-time passwords or tokens can reach hundreds of thousands of dollars per month depending on the size of a businesses’ customer base. MFA is a significant line item on a businesses’ security budget that many are concerned won’t scale as their customer base grows.
A Smarter Way to Use MFA
MFA, while effective in some capacities, is still not the ideal solution for stopping fraud and attacks on user accounts. It should be reserved for very specific instances of extremely high risk traffic. This means no good users or potential new customers will be served undue friction. Businesses will also realize significant cost savings by only sending a limited amount of MFA tokens.
It is urgent for organizations to review their authentication workflows to see what can be achieved in-session, at a lower cost, to get rid of the majority of threats - before resorting to sending traffic out of band as a last resort.
To do this effectively, businesses will need to follow the five golden rules of user authentication.
THE 5 GOLDEN RULES OF AUTHENTICATION
Instead of relying solely on MFA --or any other single type of security measure -- businesses should instead follow these “golden rules” when it comes to digital authentication.
- User Experience: When choosing how to authenticate, avoid pushing users out of band at touchpoints that are important for user engagement and growth, for example, a new account registration form. This causes added friction and may even lead consumers to abandon the authentication process out of frustration. You should put as minimal hurdles as possible between your customers and your platform. MFA can be then used judiciously in the user authentication experience, but should not be relied upon as a catch-all.
- Minimize User Opt-In: Implementing MFA often requires forcing your customers to perform an action, such as opting in or downloading TOTP applications. Again, businesses should focus on methods that require as little from their customers to authenticate as possible, with most of the work being done invisibly on the back end. This also eliminates the need to spend time and effort educating customers on turning on MFA.
- Cost Efficiency: MFA can become a costly endeavor for businesses when used for nearly every login or registration on their platform. The cost to send one SMS token may be minimal, but when multiplied over thousands of interactions a day it becomes a hefty price in the end. When choosing a solution to validate new or existing accounts, look for options that can filter out bots and bad actors at scale without the hefty price tag. By deploying MFA judiciously and not as a catch-all, it becomes much more cost-effective.
- Resilience to Attacks: Authentication measures need to keep up with evolving attacks. Forward-thinking account security platforms should deal effectively with both advanced bot attacks as well as coordinated human attacks. Sophisticated risk profiling with actionable insights enables fraud and security teams to take smarter actions when risk signals show suspicious activity while minimizing friction with clearly trusted users.
- Easy Implementation: Any solution that a business is considering should feature a quick and easy implementation process, ideally using Javascript and a mobile SDK. This enables businesses to start seeing results in days and not weeks or months, and start earning a return on their investment almost immediately.
A New Approach to Securing Logins & Registrations
Digital businesses today need to have a defense-in-depth strategy that minimizes the impact to good users while still effectively monitoring for and preventing bad actors from successfully attacking. This will lead to a much better user experience and benefits customer retention as well as acquisition. Businesses will also benefit from lower operational costs, not only due to the costs associated with deploying MFA less but also in having fewer manual reviews and stresses on internal teams. This means MFA can be deployed in a much more judicious manner, perhaps only for very high-risk traffic, saving businesses money because the majority of traffic coming to their login and registration pages has already been analyzed.
The Arkose Labs platform is centered around an AI-driven decision engine that allows trusted users to pass through without friction while orchestrating a targeted attack response for suspected fraud. The detection engine determines user intent and risk classification by comparing real-time signals of traffic to our global network of data. Traffic-classed as high-risk in our detection platform and be administered a curated enforcement challenge. These challenges will cause bot traffic to fail, and incrementally increase the time for human fraudsters to solve, making micro-deposit attacks against our customers unworthwhile.
Arkose Labs steps up vigilance at the entry gates to help digital businesses monitor every incoming user and deny entry to bad actors. Although the Arkose Platform doesn’t block any user, it does use targeted friction to filter out suspicious users. It presents incoming users with unique challenges to prove their authenticity. These challenges completely eliminate automated scripts and bots, while genuine customers can clear them rather easily.
The fight against fraud and attacks against digital accounts never ends. Attackers are always evolving their tactics and techniques, and businesses must be prepared for this evolving threat landscape. To learn more about Arkose Labs’ cost-efficient and user-centric approach to fighting fraud, book a demo now.