Phishing attacks have long been a major concern in the cybersecurity landscape. These malicious attempts to steal sensitive information often involve creating fake websites that mimic legitimate ones, tricking unsuspecting users into revealing their personal data. Traditional phishing attacks typically rely on cloned websites to deceive victims. However, cybercriminals are constantly evolving their tactics, and one such innovation is the reverse proxy phishing attack—and this type of phishing threat is on a significant rise.
Let's delve into what reverse-proxy phishing is, how it works, and how advanced security solutions like Arkose Bot Manager can help protect you from falling victim to these cunning schemes.
Traditional Phishing Attacks
Before we dive into reverse-proxy phishing, let's briefly review traditional phishing attacks. In a traditional phishing attack, cybercriminals clone a target website's content and present it to unsuspecting users. This often involves creating a fake login page that closely resembles the real one. When users enter their credentials, the attackers collect this information. However, after the user "logs in," they are typically redirected to the actual website. Thus, the transaction is dropped by the attacker, and the compromised user credentials are used to abuse the user's account at another point in time.
Reverse-Proxy Phishing Attacks
Reverse-proxy phishing takes a different approach to go beyond this relatively simple approach to harvesting credentials. Instead of creating a static clone of the target website, cybercriminals act as intermediaries between the user and the web servers they're attempting to access. This means that when this type of attack is successful, the attacker enters the user’s account in real-time to begin the abuse.
Here's how it works:
- User Requests: When an unsuspecting user attempts to access a phishing site, their request is routed through the adversary's reverse-proxy server.
- Proxy Server Interaction: The reverse-proxy server then forwards the user's request to the target site, essentially making it seem like the user is making the request directly.
- Target Site Response: When the target site responds to the reverse-proxy server, the server sends this content back to the user as a response to their original request. Importantly, the user is completely unaware that their interaction is being mediated by a malicious actor.
- Real-Time Relay Bypassing MFA/2FA When the user enters their MFA/2FA code, the proxy server intercepts this information in real time, forwarding it to the legitimate site. Since the adversary has access to the MFA/2FA at the moment of entry, they can immediately use it to gain unauthorized access into the user's account.
- Persistent Attack: What sets reverse-proxy phishing apart is its persistence. Once the user logs in, the session isn't terminated. This means the reverse proxy can continue to collect information throughout the user's session, posing a significant threat.
The Arkose Labs Solution
Thankfully, there are advanced solutions like Arkose Phishing Protection that can help detect and thwart reverse-proxy phishing attacks. Here's how Arkose offers protection to its customers:
- Detect reverse-proxy phishing attacks in real-time using the Arkose detection engine
- Protect users and block credential theft by taking action in real time
- Prevent interception of MFA/2FA codes
- Warns targeted users with a warning message, alerting the user about the threat in real time, and protecting them from potential harm.
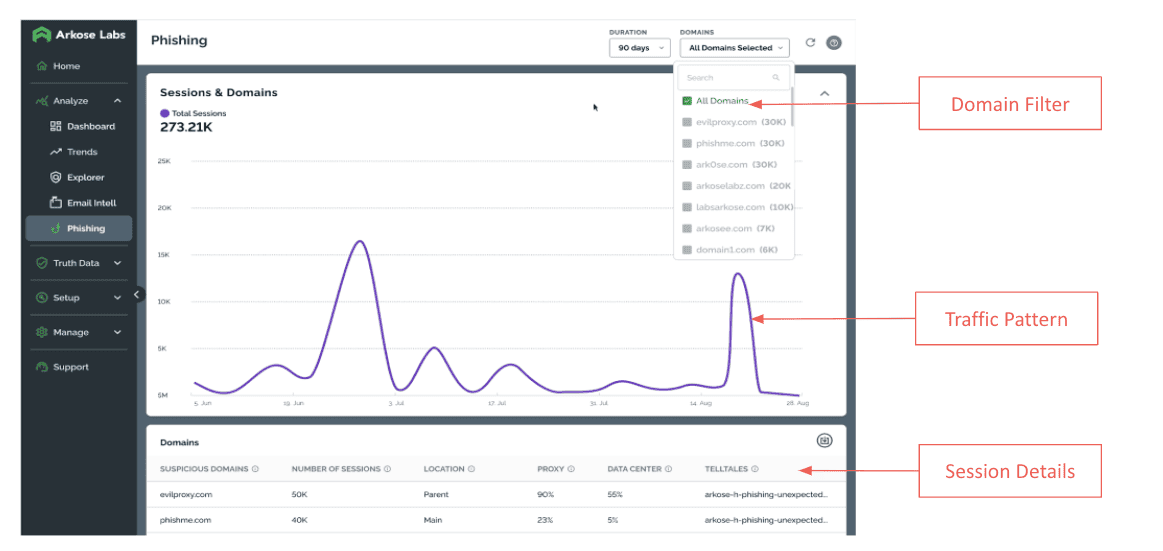
The Arkose Labs dashboard gives insight to the suspicious domains being used to target end user:
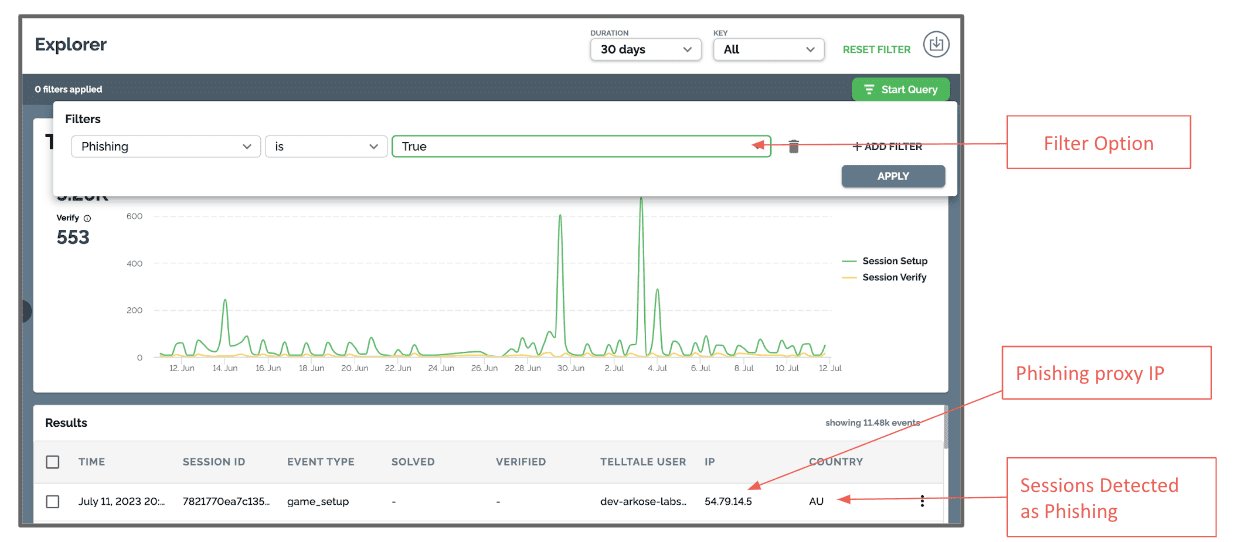
Use Session Analyzer to analyze all sessions impacted by reverse-proxy phishing attacks in real time:
Conclusion
Reverse-proxy phishing is a crafty and insidious form of cyberattack that can go unnoticed by unsuspecting users. However, with advanced security solutions like Arkose Phishing Protection, organizations and individuals can fortify their defenses and detect these attacks in real time. By implementing intelligent mechanisms that scrutinize web interactions, Arkose Labs helps unmask the true identity of malicious actors, safeguarding your online presence and sensitive information.


