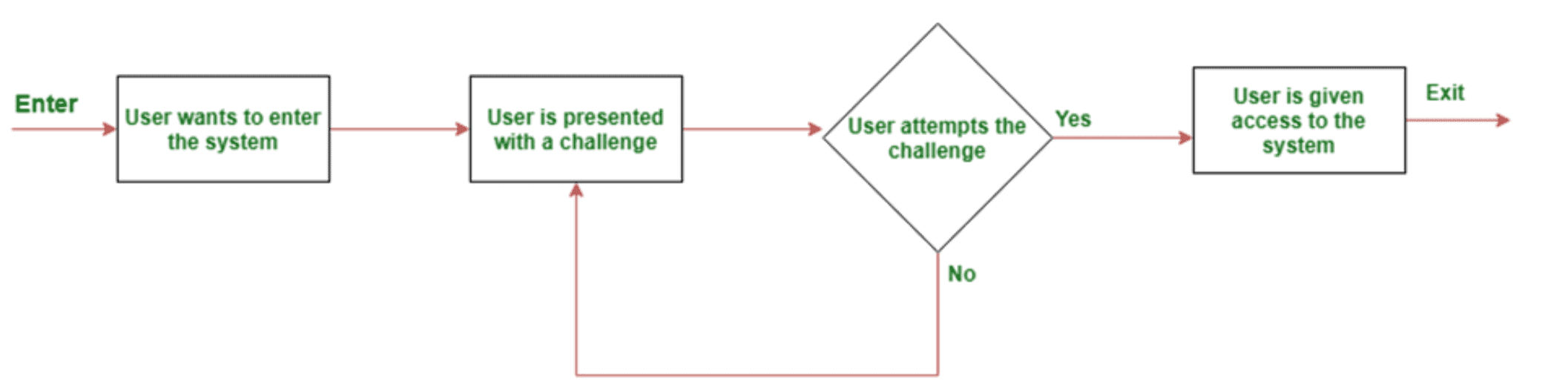
What is challenge-response authentication and why is it useful?
Challenge-response authentication refers to a set of protocols that helps validate actions to protect digital assets and services from unauthorized access. This protocol usually has two components – a question and a response – where a verifier presents a challenge to a user, who must provide a correct answer for authentication. Challenge-response protocols can be as simple as a password or a dynamically generated request.
A challenge-response authentication mechanism, or CRAM, provides businesses with an easy-to-use tool that they can use to control access to sensitive information and identify bad actors.
Types of challenge-response authentication mechanisms (CRAM)
Challenge-response authentication has been around since the early 20th century, when the US military used a paper cryptographic system called DRYAD to authenticate radio users. In this system, users at both ends would read out numbers corresponding to a combination of letters to verify their identities.
In the digital realm, there are two main types of challenges, as described below:
Static: True to their name, static challenges are protocols that do not change over time and where users can select a challenge for authentication purposes. The case of ‘forgot password’ is an example of a static challenge. When a user forgets the password, they can reset it by answering a security question.
Dynamic: In this approach, users must respond to a challenge presented dynamically. These dynamic challenges are based on the premise that if the user is real, they will have a valid answer and therefore, the answers may be different for every challenge. For instance, the answer may be a one-time password (OTP) or randomly generated token that the user must input to complete the authentication process.
Examples of challenge-response authentication systems
Challenge-response authentication is a method that businesses use to stop bad actors from accessing business assets. Commonly used mechanisms are:
- CAPTCHA: An automated method to distinguish between humans and attackers, CAPTCHA is designed to prevent bots from disseminating spam, registering fake new accounts and hacking into genuine user accounts.
- Password: A server validates the password provided by the user with the correct password.
- Biometrics: Users must provide biometric details (such as iris or fingerprint scans) that are matched with those saved in the authentication system.
- Salted Challenge Response Authentication Mechanism (SCRAM): A hashed challenge is used such that the password can be used only once. The server validates the user-provided hash by matching with the saved hash, protecting the password from exposure through replay or man-in-the-middle attacks.
- SSH (Secure SHell): This cryptographic network protocol facilitates secure operation of network services securely over an unsecured network. It authenticates communication sessions between servers using a public key infrastructure (PKI).
- Password proof system: This is a cryptographic method that helps verify passwords between two users without sharing their passwords mutually.
- Challenge-Handshake Authentication Protocol: CHAP is a three-way handshake where hash values are generated and verified between the authenticating system, challenge message, and the local system. If these hash values match, further action is allowed else the session is terminated.
- OATH Challenge-Response Algorithm: Developed by the Initiative for Open Authentication, OCRA is a cryptographically strong challenge-response authentication protocol.
- YubiKey: This method uses HMAC-SHA1 and Yubico OTP for authentication. In HMAC-SHA1, a string acts as a challenge and hashes the string with a stored secret, whereas Yubico OTP creates a Yubico OTP code encrypted using a stored AES key.
- MD5: In this mechanism, the RADIUS server directs a challenge to the client, which creates an MD5 hash of the challenge and the password that the user enters. These are then sent back to the server which uses the correct plaintext password from the database to validate the MD5 hash.
Uses of challenge-response authentication
Challenge-response authentication is mainly used in the following three areas.
- To verify passwords: When a user enters a login and password to sign into a digital account, the password is matched with that saved on the server. In case the two passwords match, the user is successfully authenticated and allowed to continue with the onward digital journey. In case of a mismatch, appropriate countermeasures are used.
- To distinguish between bots and humans: Bot attacks can disrupt business operations and degrade user experience. For instance, scalper bots can shop items in bulk during an online sale event, denying genuine consumers a fair chance to score a deal. Many businesses use challenge-response authentication to give consumers an opportunity to prove they are not bots. One of the common examples of human verification challenge-response authentication is CAPTCHA.
- To train machine learning programs: Challenge-response authentication trains machine learning and artificial intelligence programs to solve complex programs. For instance, they are made to solve human verification puzzles and the outcome is matched with that of a human user. The programs learn from the feedback, which improves decision-making over time.
Limitations of challenge-response authentication
Although commonly used challenge-response authentication methods are useful in authenticating consumers, they have their own limitations. One of the most pressing problems is with password authentication. Often, consumers reuse and recycle their passwords across multiple digital accounts. One successful account takeover attack can result in compromising multiple accounts. The server cannot ascertain whether the person providing the password is a genuine user or an impostor using stolen consumer details. If the impostor provides the correct password, the system will allow access to the system.
The latest CRAMs such as SCRAM use cryptography to match the hashes such that passwords are not exposed.