What is Account Takeover (ATO) Fraud?
Account takeover (ATO) fraud is an identity-based attack where fraudsters use stolen credentials to take control of genuine user accounts and use them as a launchpad for a variety of crimes, including taking over bank accounts, redirecting shipments, money laundering, stealing rewards points, reselling subscription information and more.
Many fraudsters begin their careers with ATO attacks due to a low barrier to entry - multiple tools are available to execute the attacks at scale with little to no cost to the fraudster. Years of massive data breaches have made it easy to acquire combo lists of usernames and passwords. The tools to launch ATO attacks at scale are readily available and there are even YouTube tutorials on how to run them. If they need more compute power to launch massive attacks at scale, they can easily buy it. They can also acquire software to load combo lists and launch attacks at scale with ease. Many of these come in premium tiers that also feature dedicated customer support.
Additionally, account takeover fraud is popular because the process to execute it is the same amongst various industries - identify valid, stolen credentials, and use those credentials to access an account.
ATO fraud has grown significantly, and it does not appear to be slowing. It is increasing across all industries. A majority of the attacks detected on the Arkose Global Network are at the login point.
In this page, we dive deep into the latest fraud and abuse data to look at how account takeover fraud has grown, how the modern fraudster is executing ATO attacks and solutions you can implement to detect and prevent these attacks.
The Incredible Growth of Account Takeover Fraud
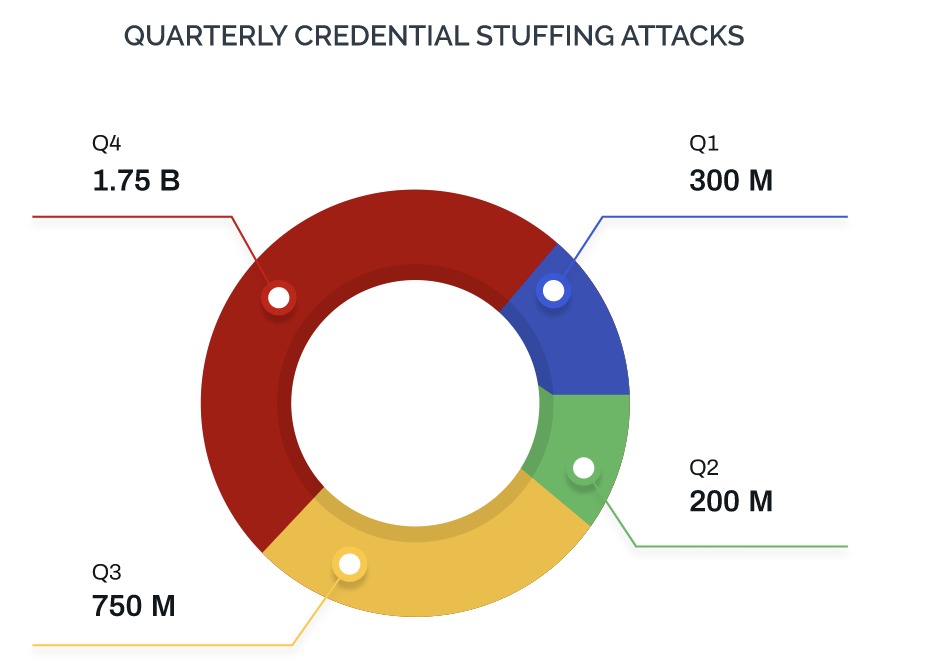
Account Takeover attacks are on the rise. Credential stuffing attacks more than doubled in Q4 2020 compared to Q3 of the same year and were around 90% increased from Q1 2020.
This is likely due to an increase in the availability of quality, inexpensive username-password combinations and a host of other personally identifiable information (PII). For example, the popular site Have I Been Pwned reports over 10 billion breached accounts from 460 different websites. Additionally, one estimate finds that an average American has 23 online accounts--the actual number could be higher. That means there will never be a shortage of targets for ATO attacks. This enables many fraudsters, even those with little technical knowledge, to easily launch bot attacks at scale.
How Fraudsters Profit from Successful Account Takeovers Fraud
ATO attacks are also popular among fraudsters because of the wide range of downstream attacks made possible by the compromised accounts. The most common use for ATO attacks are to steal payment credentials or other valuable information from the account itself.
Additionally, compromised accounts can be used for money laundering and other criminal activities. Using the PII derived from taken-over accounts, fraudsters can apply for loans or credit cards. Further, compromised accounts can be used for spam or phishing attacks, which may be more successful coming from a “real” account.
Draining funds and assets from a compromised account is only the first step of an ATO attack. Fraudsters can also exploit these accounts to make fraudulent payments. They can redeem the loyalty points in the account and even use the compromised account to launder money.
However, the motivation for account takeover is not limited to financial abuse. Fraudsters also exploit the accounts under their control for sinister crimes—such as drug- and human-trafficking—that can have far-reaching consequences for society.
Account takeover attacks can be very costly. According to a poll of 100 IT executives commissioned by Arkose Labs, a majority responded that ATO attacks can cost anywhere from $50 to more than $200 per incident. When measured in the thousands, this can be a huge monetary drain for businesses.
How Fraudsters Target Attacks Across Industry
Financial Services/Fintech: These are typically the most valuable accounts for fraudsters to target, since they not only can directly drain funds from them, but they also contain sensitive information like social security numbers, addresses, and more. Since financial accounts are so valuable they are usually highly protected and have an additional layer of security such as 2FA. Fraudsters get around this by using tactics such as SIM swaps (we’ll get more into this later). They also use phishing campaigns; typically sending emails that look like they are from a bank, asking the recipient to click on a malicious link and log into their account to confirm their identity. The login page is actually fake and instead provides the fraudster with that user’s information.
Gaming: Gaming accounts are generally much less valuable than financial ones but also much easier to hack into, as they are less protected. Fraudsters run credential stuffing attacks at scale to break into these accounts. Attackers hack into accounts to steal digital goods and items to resell to other gamers on gray market forums; this is known as real money trading. They also use these compromised accounts to use cheats or hacks to gain advantages in-game. Typically when gaming platforms notice this they ban the offending account, but the fraudster can keep doing this over and over again with newly compromised accounts.
Travel: With travel sites, fraudsters are generally going for loyalty points. They can look and see if there is a stored payment mechanism in the account and use that, but mostly they are looking to use loyalty points to buy hotels, airfare, car rentals, and cruises. They may book these for personal use but more often they do it to then resell on a third-party platform.
Social Media: This is an interesting area because there is no direct dollar value from social media accounts. They don’t contain financial information or any other sort of PII. Fraudsters instead use these accounts for other reasons, such as to send spam and phishing messages to real users on the platform, to spread disinformation, or to artificially “like” other accounts they may be associated with. In some cases, fraudsters can also resell valuable accounts, such as those with only a few characters or unique names, because they are rare.
Streaming Services: Since there is not a massive amount of money to be made on streaming accounts, here fraudsters’ goal is to launch credential stuffing attacks against streaming services at scale to gain access to as many accounts as possible and resell access to others. So if a person is paying $15/month and their account gets hacked, the fraudster might sell access to that account to any number of people for one-time fee of a few dollars each.
What Are The Steps of Account Takeover (ATO) Fraud
Depending on the target and the motivation, fraudsters choose an attack technique with the lowest cost and lowest friction. For instance, a stolen list of credentials will suffice for an attack on, say, an eCommerce or a travel website. However, for banking websites, which do not use email addresses as usernames, social engineering may be more appropriate. Further, a dictionary attack may be in order to take over a power account, such as a system administrator.
A successful ATO attack always consists of three major steps. These steps of the attack may be carried out by the same person or group; but typically, they are not. There is an entire community involved in the process.
Step 1. Credential Harvesting
Stealing and harvesting credentials are the most time-intensive parts of the process and require the most technical skill. Credentials are usually stolen using phishing, malware, or social engineering attacks, but also by exploiting various database security vulnerabilities to extract information. The stolen information is then sold on the public or dark internet. This is a lucrative business, since a single list may be sold multiple times, over several years, before the data begins to lose value.
Step 2. Account Validation
The next step involves checking accounts. The most effective and cost-efficient means to check a large list of accounts at scale is to use botnets. They are easily found on the internet, and some bot services even come with tutorials and customer support! Bots will attempt logins against the targeted website using the provided credentials until they find valid username and password combinations.
You don’t need to be an accomplished hacker to carry out this stage of the attack at scale. You can simply enter the list of stolen credentials into the tool, configure your proxies, define the target and you’re ready to go. More skilled attackers can even build their own botnet to deal with any bot or fraud-detection solutions in place more effectively.
The attack will help extract a list of credentials that have been verified against a specific website, which will then be resold on the dark web. The value of these refined lists fluctuates, depending on the possible ROI associated with them. For example, a verified list for a banking site or an eCommerce site known for its very good loyal customer reward program will have a much higher value than a list for a site that offers basic services.
Here’s an example of how a fraudster would use a piece of software to validate credentials:
Step 3. What is Account Takeover
The final step in this chain is the fraudster, who buys these lists. The lists are usually sold in bundles, as there is no guarantee that any given individual account will be valuable. For instance, a dormant account (where the account owner doesn’t actively use the site), will only yield the owner’s personal data. However, some other accounts may turn out to be a treasure trove for the attacker.
Fraudsters will use automated methods to fill in login forms en masse with validated credentials; leverage low-cost human “sweatshop” resources to launch ATO attacks in a way that evades anti-automation defenses, or for very high-value targets manually complete the ATO attack themselves.
Automating ATOs with Credential Stuffing
Credential stuffing is a subset of account takeover attacks, where bots are deployed to constantly try different username/password combos at scale until a match is found. With the ready availability of this information for purchase by fraudsters -- due to years of personal information being exposed from data breaches -- credential stuffing plays a key role in carrying out ATO attacks.
From the same video as earlier, here’s an example of how quickly and easily an attacker can execute an automated credential stuffing attack:
Credential stuffing is a vital part of carrying out successful fraud attacks. Fraudsters will often use automated scripts to power credential stuffing, such as to fill in login forms en masse with validated credentials. But they also utilize human sweatshops to launch these attacks so as to evade defenses that specifically look for signs of automation, or even conduct the attacks themselves for very high-value accounts.
Once credential stuffing is used to compromise an account, the fraudster then has a wide range of options, from simply stealing money or information from the account, using it for downstream fraud such as sending phishing or spam messages, laundering stolen money, or reselling the successfully validated credentials as a list on their own right.
Account Takeover Detection Prevention Solutions
Account takeover is challenging to detect and stop. Fraudsters have studied the defense mechanisms that businesses deploy and have devised innovative ways to circumvent them.
-
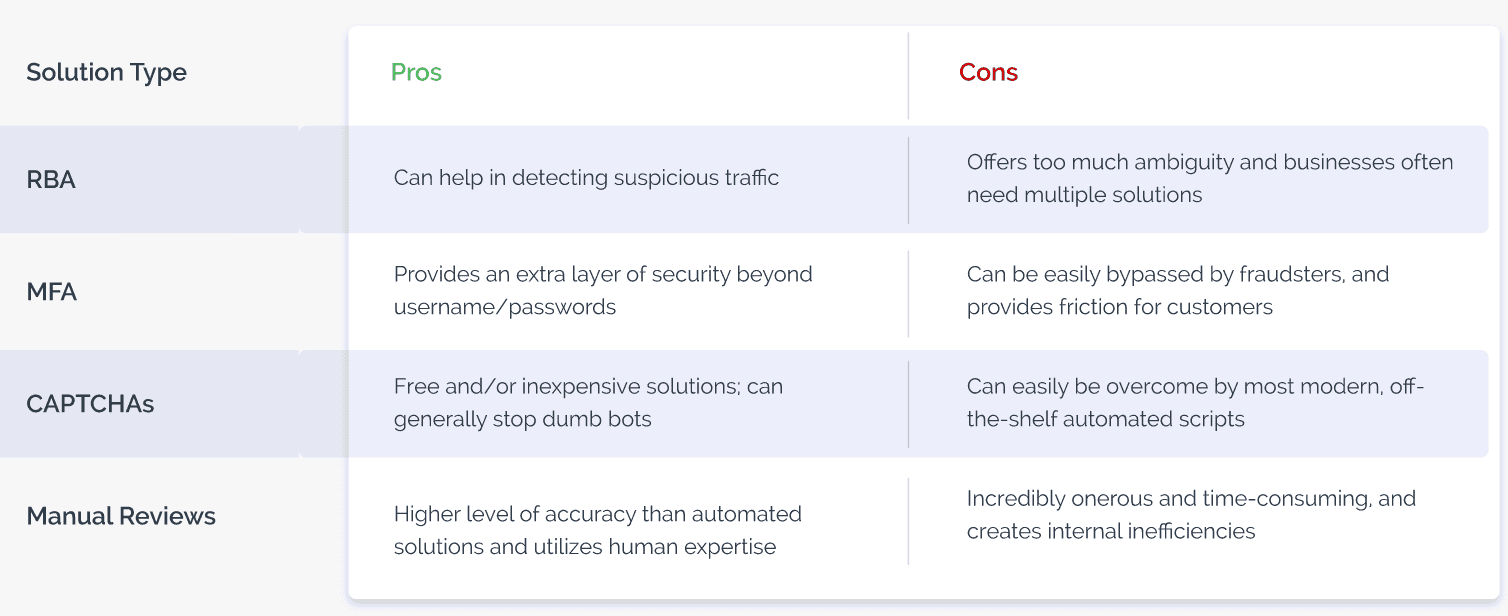
- Risk scores: Many digital businesses rely almost entirely on data-driven solutions to assign risk scores and create rules to verify digital identities. However, with massive amounts of personal data being bought and sold, digital identities have been compromised at scale, leaving fraud intelligence data feeds with a significant level of ambiguity. To overcome limitations, businesses should deploy multiple solutions and threat scores. However, this results in complex tech stacks and alert overload, which is difficult to action.
- Multi-factor authentication: The aim of multi-factor authentication (MFA) is to create barriers for fraudsters. However, despite its noble aim, out-of-band authentication ends up introducing unnecessary friction for good users. Further, fraudsters have devised ways to intercept SMS messages, and solutions that are paid for on a per-token model become very expensive.
- CAPTCHA: Available for free for many basic offerings, CAPTCHAs are designed to distinguish between humans and machines. However, with automatic solvers mushrooming, traditional CAPTCHAs are near-redundant as they allow bots to easily bypass them at scale. They also provide a sub-par user experience and fail to address human-driven and hybrid fraud attacks.
- Manual review: Reviewing every user manually is an onerous task, which not only needs spending exorbitant amounts of effort but also slows down the process and increases the risk of human biases creeping in.
How Arkose Labs Detects and Prevents Account Takeover Fraud
Businesses must rethink their fraud prevention approach and adopt a strategy that provides them with long-term protection against evolving fraud while accelerating the consumer journey.
That’s why the Arkose Labs Fraud and Abuse Prevention Platform uses data-driven, real-time fraud intelligence, which is paired with secondary screening of risky traffic so businesses can reliably address ambiguity. Real-time risk assessments further classify traffic based on probable intent and inform the system whether additional authentication is required.
Rather than outright blocking traffic and negatively impacting the user experience, the Arkose Labs approach is to use targeted friction, which is reserved purely for high-risk traffic. While the vast majority of good users can pass unchallenged, those who do experience a challenge can see that steps are being taken to protect their accounts without degrading their experience.
Arkose Labs' custom enforcement challenges are context-based, adaptive visual challenges that stop both automated and human-driven account takeover attempts. These custom visual challenges are designed to specifically thwart machine vision software, causing bots and automated solvers to fail. Additionally, the use of incrementally more complex challenges wear human fraudsters down, sap their resources and compel them to abandon attacks.
Learn more about Arkose Labs Account Takeover and Credential Stuffing Prevention solutions.
The Ultimate Guide to Account Takeover Fraud
- What is Account Takeover (ATO) Fraud?
- The Incredible Growth of Account Takeover Fraud
- How Fraudsters Profit from Successful Account Takeovers Fraud
- How Fraudsters Target Attacks Across Industry
- What Are The Steps of Account Takeover (ATO) Fraud
- Step 1. Credential Harvesting
- Step 2. Account Validation
- Step 3. What is Account Takeover
- Automating ATOs with Credential Stuffing
- Account Takeover Detection Prevention Solutions
- How Arkose Labs Detects and Prevents Account Takeover Fraud


