What is bot detection?
Digital attackers are in the cybercrime business to make money. They are willing to put in efforts and resources commensurate with the profit they can make from an attack. A handy and cost-effective tool that allows them to launch attacks at scale and speed is automation scripts and bots.
A bot is an automated application or script that can mimic human behavior to varying degrees of sophistication, and it comes in all shapes and sizes, both legitimate and malicious. Bot scripts are widely and cheaply available – and some of them even come with customer support.
Bot detection is the process of identifying and distinguishing between automated bots and human users, using techniques such as behavior analysis, device fingerprinting, CAPTCHAs, machine learning, and threat intelligence to mitigate bot-driven threats.
Bot detection is increasingly important because some estimates indicate that bad bots now constitute nearly half of all internet traffic. Since they can be powerful tools in delivering web services at scale and low cost, they are similarly exploited by bad actors looking to maximize their profits. The ability to launch thousands of digital attacks in parallel makes bots much more scalable than humans. This also makes it possible for cybercriminals with little or no technical knowledge to trigger large-scale attacks.
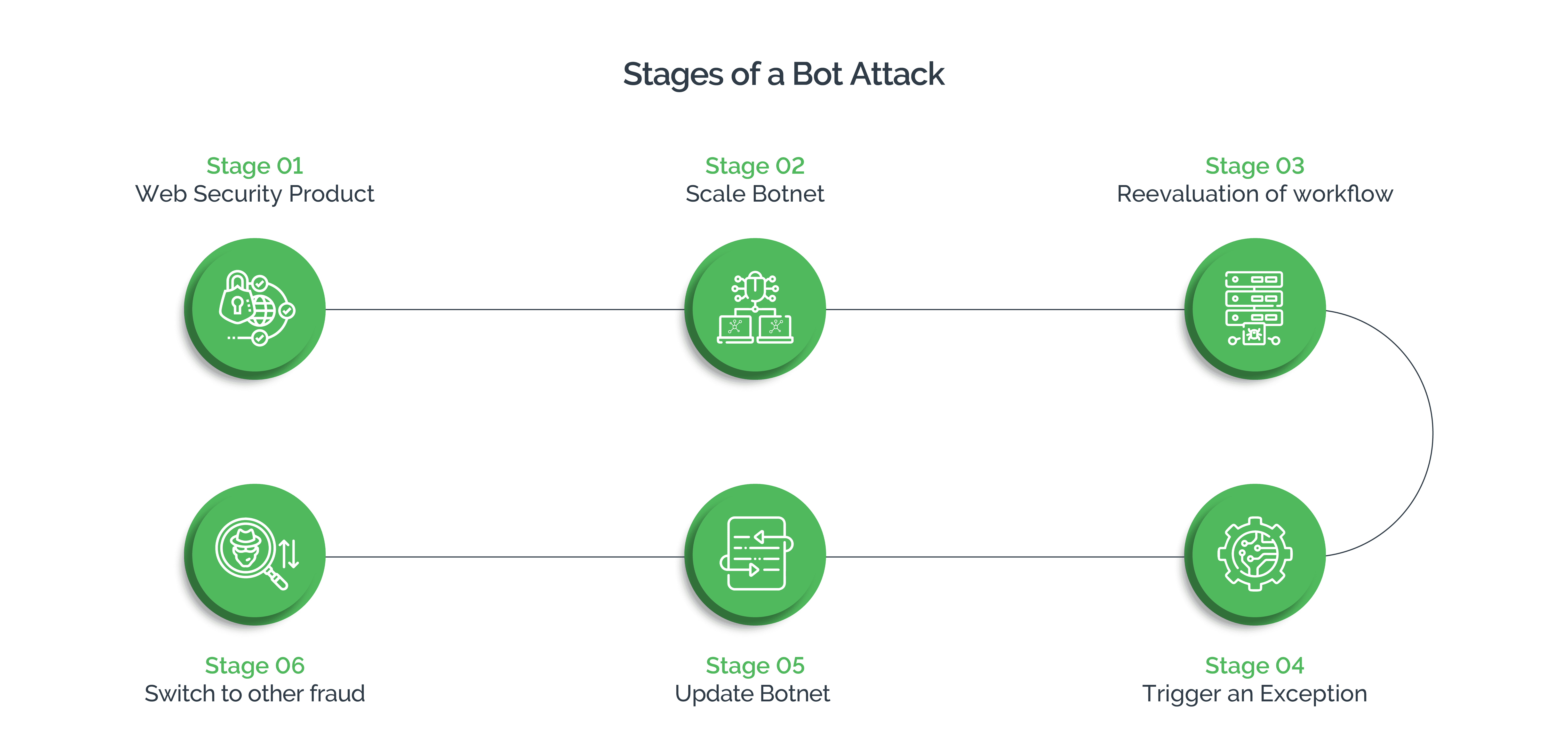
The six stages of a bot attack
Malicious actors study the bot detection techniques businesses deploy to exploit the loopholes. This knowledge also allows them to tailor their attacks using appropriate resources that fetch them maximum gain with the least investment. A bot attack, typically, follows the six stages explained below:
- Stage 1: In the first stage, a site administrator updates the workflows and introduces a web security product. This update detects all existing bots, as their default scripts cannot keep up with the changed workflow.
- Stage 2: To overcome this latest hurdle, bot operators scale their botnet to thousands of nodes that are hosted in cloud providers across diverse countries. This enables them to randomize their HTTP header signature.
- Stage 3: When the attacks continue to fail, attackers re-evaluate the workflow and study the latest web security protection introduced by the business. They identify the type of information that the security product collects, and use it to update the bot script with a “good fingerprint.” They also try to juggle or randomly change the data points and evaluate the results. If they find that the security product uses persistent ID or cookies, they try to harvest them from legitimate user sessions and replay them from a botnet.
- Stage 4: If the efforts in stage 3 fail, these bad actors try to send random data to trigger an exception, which can cause the product to “fail safe” and disable the defense.
- Stage 5: Black-hat hackers use selenium or headless chrome to upgrade the botnet to a headless browser—one that can run JavaScript—and simulate human behavior, which includes key presses, mouse movements, and clicks.
- Stage 6: In an instance where all the techniques fail against the upgraded security product, cybercriminals may switch over to human-driven attacks, provided they are cost-efficient.
Bot-driven attacks are on the rise
Arkose research shows that bot attacks are surging. This is primarily because consumers now use multiple digital channels, including desktops, laptops, mobile apps, and gaming consoles to interact with websites. Further, APIs have opened up yet another attack surface.
As a result, bad actors have found multiple entry points to target. Cyberattackers target this increasing traffic using bots and automated scripts, not only to scale their attacks but also to make the attacks more cost-efficient. Bots and scripts are easily available on the internet and are cost-effective.
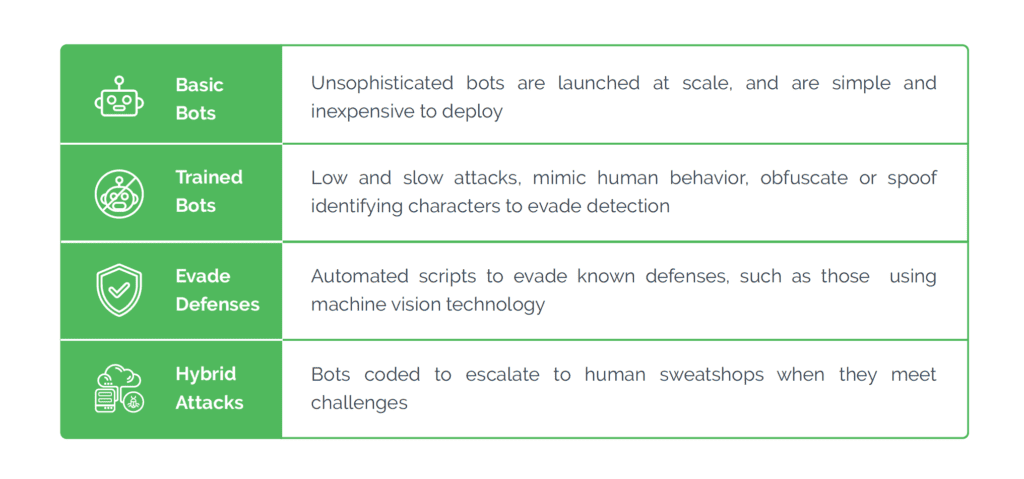
Bots are generally used for credential testing, credential stuffing, spam and abuse, and card testing. However, depending on the defenses deployed by the target businesses, cybercriminals can choose the sophistication of the bots and use them in multiple ways to tailor their attacks. These include:
- High-Volume Attacks: Often, basic bots are used to scale up the attacks. Even when using simple or unsophisticated bots, bad actors can pile up their exploits because of the volume these bots help achieve. When the volume is high, even a fraction of bots succeeding can translate into massive financial gain. For instance, spam, which is a low-value, high-volume activity, needs only a few users to click malicious links to make the attack profitable.
- Low and Slow Attacks: To orchestrate a long-term attack, criminals often lie low initially, deploying bots for the initial groundwork. These bots copy human behavior and spoof identifying characters to evade bot mitigation solutions. For instance, they attack peripheral customer touchpoints such as fake reviews, up/down voting videos, and abusing in-game economies.
- Evading Detection: Sophisticated, advanced bots are automated scripts that use machine vision technology to circumvent detection. These bots can impersonate true users with a fairly high accuracy rate and can fool bot management solutions.
- Hybrid Attacks: This is a combination of bots and human attack farms, which are low-wage laborers who launch attacks on behalf of the cybercriminals. These human farms take over when bots fail to overcome bot-prevention mechanisms that need more nuanced human interaction.
Why must businesses address this threat?
Digital is the flavor of global commerce today, and increased digital interaction is becoming cannon fodder for increased cyberattacks. Combine this with the fact that bots are now cheaper, easily available, more sophisticated, and easily deployable, and you have the perfect recipe for a large-scale bot-driven attack.
To make matters worse, bad actors understand the parameters that businesses use in the detection and mitigation of bot-driven attacks. They have devised ways to manipulate and circumvent these defenses at scale. They can use the anonymity of the internet to hide their true location and spoof IP addresses and legitimate customer devices. Today, bots are well-trained in machine vision technology that enables them to easily bypass CAPTCHAs. Further, mass manipulation of digital identities can successfully fool data-driven solutions, because bots can mimic genuine users.
Companies, therefore, have become more vulnerable to bot-driven attacks. They must make every effort to stop this onslaught to protect the business and preserve customer experience.
Limitations of traditional mitigation approaches to website bot detection
Traditionally, businesses have followed three main mitigation approaches to detect and fight bot-driven attacks. However, the inherent limitations of these approaches make it difficult to effectively ward off the threats of evolving bots:
- Blocking Traffic: Some of the prevalent bot defense solutions block all traffic that appears suspicious. However, with bots impersonating true users and true users displaying anomalous behavior, there is a high probability of good customers getting blocked while bots pass through. Blocking good customers can cause dissatisfaction and customer churn, which in turn can damage the bottom line and brand reputation.
- Risk scoring traffic: As bot attacks evolve to become more sophisticated, traditional risk scoring is losing its efficacy. Mass manipulation of digital identities has rendered risk scores less reliable. Further, since this method involves manual review of high risk scores that aren't explicitly accepted or rejected, it delays decisioning, allowing bots to pass through. In addition, many organizations are struggling to deal with the information overload emanating from complex tech stacks.
- CAPTCHA: Initially designed to stop automated attacks, innovations in bot technology have rendered CAPTCHAs near-redundant. They can now be solved with easily available (and possibly free) automatic solvers. Instead of blocking bots, CAPTCHAs end up causing unnecessary friction for good customers. Further, they are ineffective against a hybrid attack, which uses a combination of bots and humans. Since most CAPTCHAs are free or nearly free, they neither come with support services nor provide businesses with any insights into the attack patterns.
Creating an online business ecosystem that enjoys the trust of its users is critical to thriving in the digital economy. Digital businesses are therefore pressed to offer a seamless and safe digital experience to their customers.
An adaptive approach to bot detection
Arkose Labs provides a comprehensive solution, known as Arkose Bot Manager, designed to effectively identify, counter, and manage both human-based and bot-driven attacks. By leveraging advanced methodologies, this bot detection solution enables organizations to proactively detect and prevent automated threats, safeguarding their operations from potential harm.
Arkose Bot Manager incorporates a blend of machine learning, behavioral analytics, and risk assessment techniques to deliver real-time bot detection and mitigation capabilities. By employing the following strategies, it helps organizations protect themselves against the detrimental effects of bot-driven attacks, such as account takeover, web scraping, and other malicious activities. The Arkose Labs bot detection and removal solution includes:
- Advanced Bot Mitigation: Through in-depth analysis of user behavior, device fingerprinting, and real-time data, Arkose Bot Manager accurately differentiates between genuine human users and malicious bots. This capability effectively shields businesses from cyberattacks by blocking and preventing the activities of bots.
- Adaptive Challenges: Arkose Bot Manager leverages adaptive enforcement challenges using Arkose MatchKey, which authenticates users by presenting puzzles or tests that are difficult for bots to solve but straightforward for legitimate visitors. This approach ensures a seamless user experience while effectively thwarting automated bots.
- Real-Time Reporting and Analytics: With real-time reporting and analytics features, Arkose Bot Manager provides organizations with detailed insights into bot activity, attack types, bot origins, and patterns of suspicious behavior. Armed with this information, businesses can enhance their real-time bot detection with data-driven decisions.
- Continuous Optimization and Support: Arkose Labs offers ongoing support from a team of experts to analyze and optimize bot detection and mitigation strategies. This continuous collaboration ensures that businesses remain fortified against emerging threats and evolving attack techniques.
- Global Threat Intelligence: By maintaining an extensive network of global threat intelligence, Arkose Labs actively monitors bot activity and trends in cyberattacks. This proactive approach empowers organizations to stay one step ahead of emerging threats and evolving attack techniques.
In summary, Arkose Bot Manager equips businesses with a powerful set of bot detection tools and capabilities to combat the escalating threat landscape. Through its adaptive approach, real-time insights, continuous support, and global threat intelligence, organizations can effectively safeguard their operations from the risks posed by automated bots and malicious activities. Learn more about how Arkose Labs can help your business eliminate bot attacks.







