At Arkose Labs, we observed both innovative and status-quo attacks, ranging from device and browser signature manipulation and IP system abuse to coordinated attacks in partnership with fraud farms. We also noticed that attackers consistently abuse our customers’ sign-up flows using fake email addresses, an attack vector that has traditionally been blind to bot prevention systems.
Email Addresses: A Great Tool For Abuse
Approximately 4.3 billion email users existed in 2022, and online services have always allowed new users to sign up for their services using an email address. This opens a massive window of opportunity for attackers.
A new email address is free and easy to create. Attackers leverage this flexibility to create new email addresses in troves and use those to create fake accounts on online services. What’s interesting is that a significant number of those cybercriminals don’t manipulate other attack vectors such as browser and device fingerprints, proxy usage, network-level manipulations, etc., making it immensely difficult for traditional bot detection systems to detect this abuse. Additionally, attackers stay under the radar by performing low and slow attacks so that rate-limiting systems are not triggered.
This is why Arkose Labs built Arkose Email Intelligence™ within our Arkose Bot Manager stack. The service analyzes more than 50 signals related solely to the email address in real-time, which are then used to apply pressure dynamically on the traffic to prevent bots from attacking our customers.
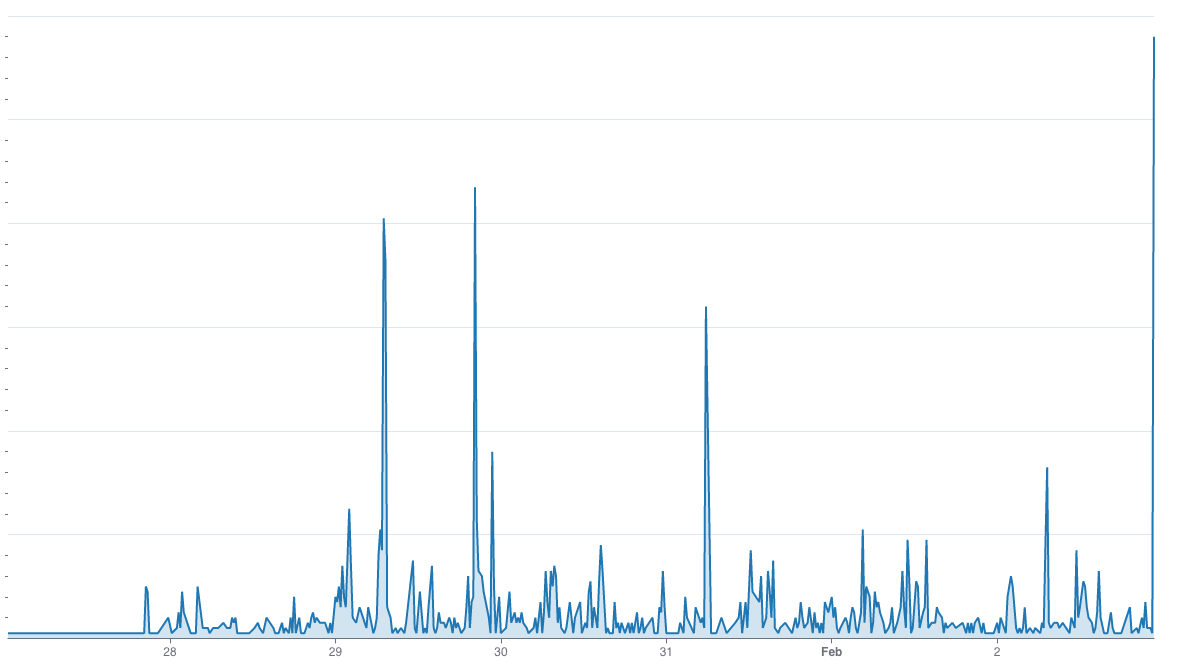
Below is a graph showing the traffic to the Arkose Email Intelligence from the service’s early adopters. Generally speaking, this graph doesn’t represent an attack except for a couple of random spikes.
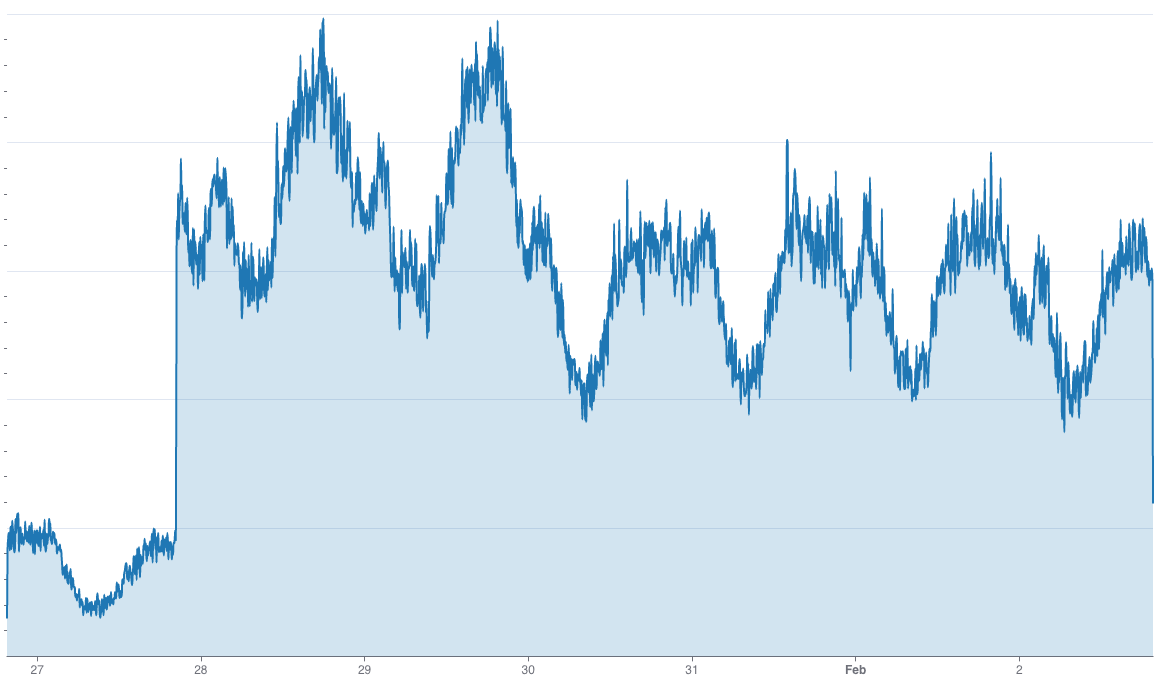
However, upon further investigation, we noticed a continuous presence of traffic from risky emails staying under the radar (shown in the graph below). There are occasional spikes, but they are relatively low in the grand scheme of things to trigger an alarm.
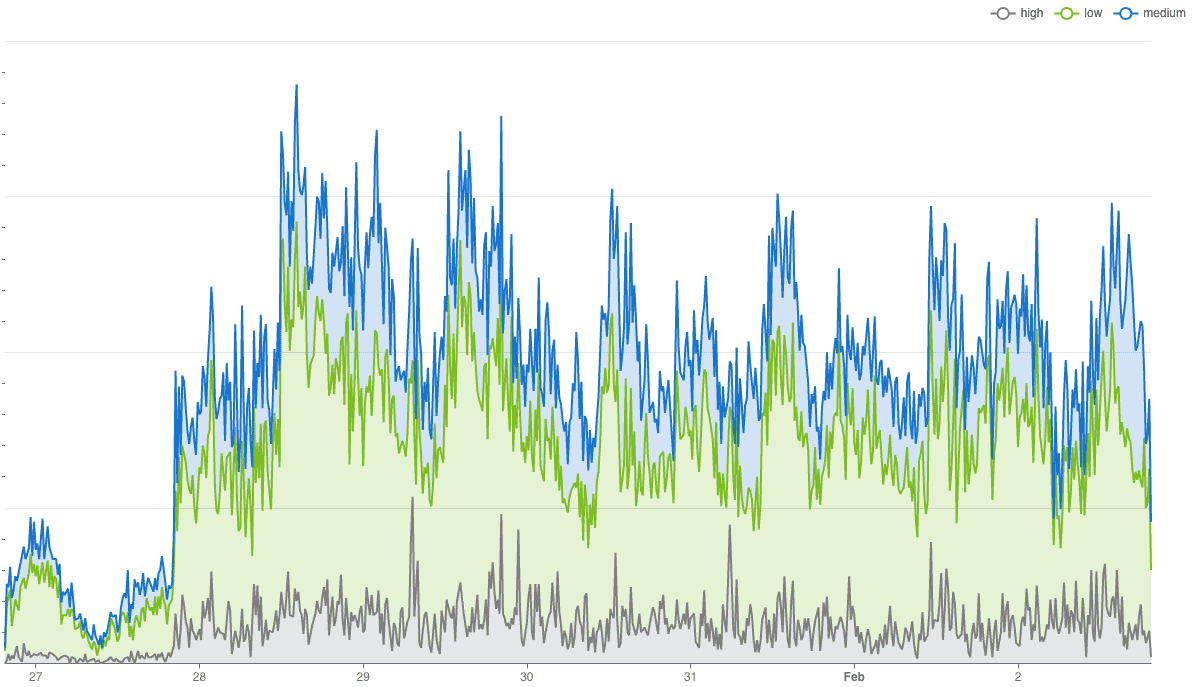
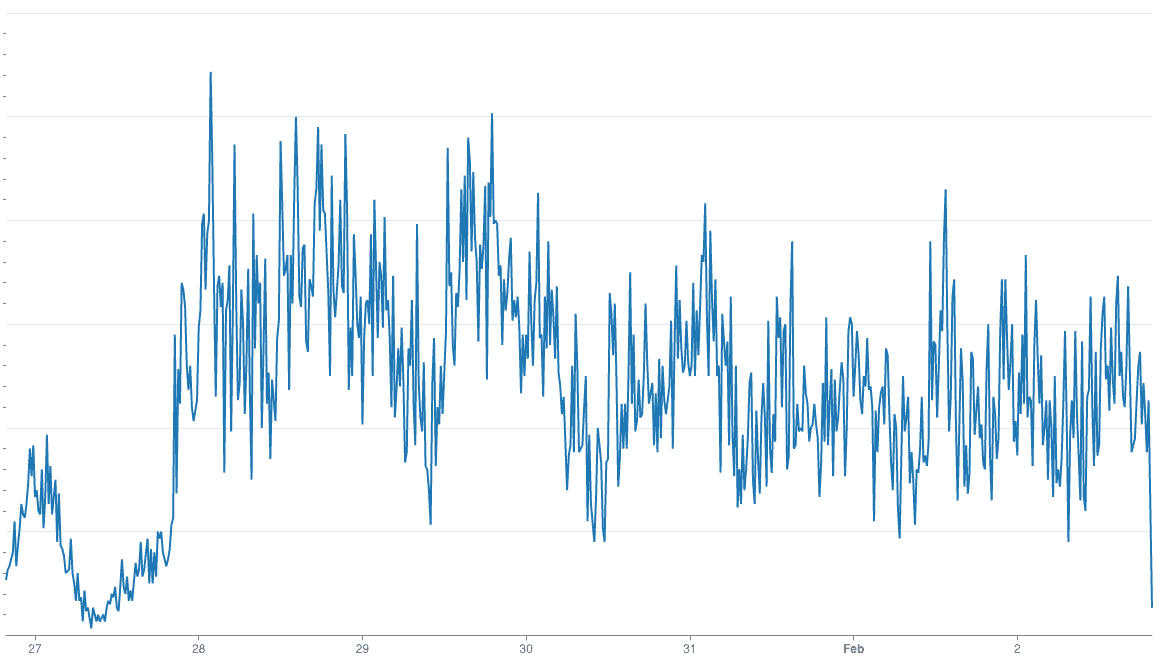
What’s more interesting is that a significant portion of the traffic from risky emails continues going undetected (shown in the graph below) by the traditional bot detection systems we had in place since these attackers didn’t manipulate anything else apart from email addresses.
A Methodical Approach To Abuse
There are several ways to use a risky email address to create fake online accounts, and attackers use a methodical approach to make such abuse successful. Some are easy to detect, but most are complex.
When bad actors intend to abuse an online platform for financial gain (such as abusing an ongoing promotion), they create new email addresses using one of the free services. They then leverage those new emails for multiple sign-ups and promotional campaign usage. This type of abuse, known as Email Enumeration and Email Tumbling abuse, is often contextual and difficult to detect since there are legitimate usages of tumbled emails.
Another way cybercriminals attack is by creating emails on disposable or recently created domains. Disposable domains are created for specific purposes and one such purpose is to commit attacks. There are several free and paid websites that offer an option to create new emails on disposable domains. Once the motive is fulfilled, attackers abandon that account and create a new one.
Programmatic, Bot-Driven Attacks
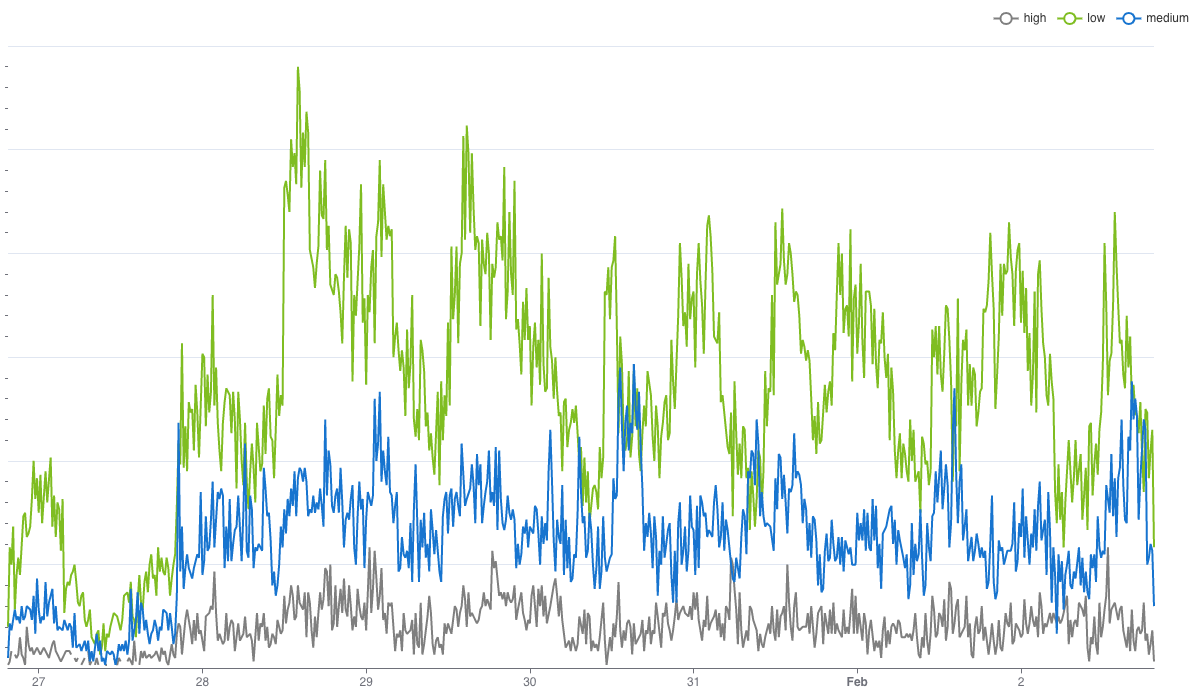
Not all attacks involving email address abuse are low and slow and manually-driven. There are attacks that can be launched programmatically. This involves creating new email addresses that look gibberish or fake to the human eye, but are indistinguishable from good email addresses to a machine. Attackers typically leverage bots for launching these attacks. Email handles are created using predefined patterns that are regularly rotated to avoid detection.
This is the most difficult type of attack to detect and hence, often is not a part of similar email intelligence services available in the market. The alternative, an email validation service, is too latency and error-prone to be used in the latency-sensitive flows. Our proprietary algorithm detects such attacks, and we continue to see attackers using this mechanism for fake sign-ups (as shown in the graph below).
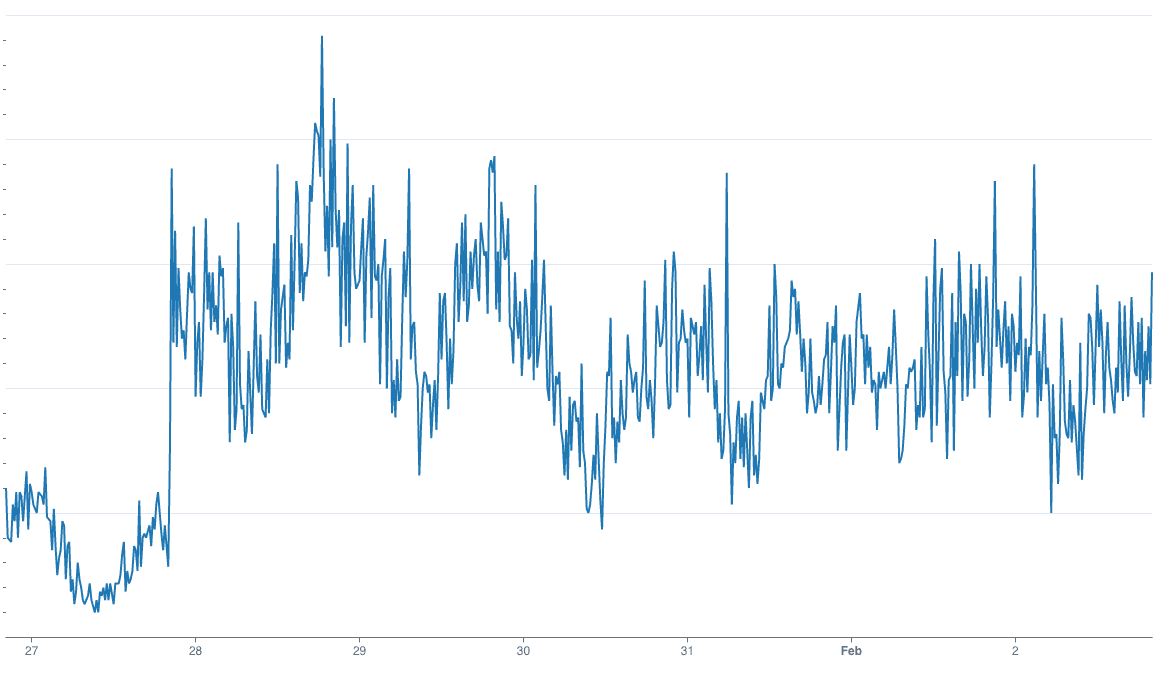
These are just some of the ways attackers use to create fake accounts using an email address. Arkose Email Intelligence looks for several such possible attack types to determine risk. Additionally, a dedicated R&D team continuously looks out for additional threat vectors that can be incorporated to make the service more effective.
These are just some of the ways fraudsters use to create fake accounts using an email address. Arkose Email Intelligence looks for several such possible attack types to determine risk. Additionally, a dedicated R&D team continuously looks out for additional threat vectors that can be incorporated to make the service more effective.
Arkose Email Intelligence: An Ingenious And Cost-Effective Way To Mitigate Bot Attacks
Traditional email Intelligence offerings are too expensive for businesses to leverage at a bot scale, and most businesses leverage these services only on already flagged traffic or on specific, high-value transactions.
From the beginning, our goal was to make Arkose Email Intelligence economically viable for our customers so that it can be utilized for ALL incoming traffic that contains an email address. In fact, we are the first in the industry to leverage email intelligence for bot mitigation.
Advantages of Arkose Email Intelligence
- Seamlessly integrates within Arkose Bot Manager
- Uses a combination of heuristics and self-learning models to detect abuse
- Provides crucial inputs to the Arkose challenge technology so that the right amount of pressure can be applied to mitigate bot attacks. This means it can be used for automated bot attacks as well as “low-and-slow” human-driven attacks.
The early results are extremely positive and we have seen our overall attack catch rate go up between 20% and 70% depending on the customer’s traffic. The positive results have prompted several of our customers to either onboard Arkose Email Intelligence, or test with an intent to onboard gradually.
Rich Threat Intelligence Via API Response
To continue our commitment to transparency and to enable our customers to use the intelligence generated by the Arkose Labs platform, we will share rich, actionable insights via the Verify API response along with a suggested action that customers can directly leverage to create downstream workflows.
Summary of Arkose Email Intelligence
The massive use of email addresses as a tool for abuse by automated bots and human-driven attacks is a major issue for businesses. Arkose Labs built the Arkose Email Intelligence service to address this problem by analyzing more than 50 signals related solely to the email address in real time, making it a cost-effective solution to mitigate bot attacks.
Arkose Email Intelligence can detect various types of email abuse including email enumeration and email tumbling, disposable domains, and programmatic attacks. This is achieved through a proprietary algorithm and continuous research and development by the dedicated R&D team. With Arkose Email Intelligence, businesses can effectively prevent fake account creation and protect their online platforms from fraudulent activities.
To find out how we can help your business stop bots in their tracks, send us a message! We are here to help.