Small and medium-sized businesses are particularly vulnerable, as they often lack the necessary resources to implement effective protection against DDoS attacks. As a result, companies today need to understand the impact of DDoS and how they can be prevented and mitigated through more comprehensive security measures.
What is a DDoS Attack?
A DDoS attack is a well-known cyberattack where an attacker floods a web server, service, or network with an overwhelming amount of traffic to disrupt normal operations. To carry out such attacks, cybercriminals typically flood the targeted server or network with messages, requests for connections, or fake packets. This giant increase in traffic causes the server to slow down, crash, or become unavailable as it exceeds its bandwidth limit.
When a critical server is targeted, it can lead to a complete network infrastructure shutdown, bringing business operations to a standstill. Additionally, while the server is down, other cyber attacks like ransomware and extortion may be launched, resulting in substantial economic losses for organizations. Typically, the attack traffic originates from a group of compromised systems and devices known as botnets, which often attack using malware. With the rise of internet-connected devices, particularly IoT devices, launching such cybersecurity threats has become increasingly effortless.
Tired of reading? Find out how your business can design a dynamic fraud response by downloading and listening to this recent webinar.
Types of DDoS Attacks
There are various types of DDoS attacks that can differ based on the attack vectors and methods employed. Some of the most commonly used DDoS attack types include:
Volumetric Attacks
Volumetric DDoS attacks aim to overwhelm a machine's network bandwidth with large amounts of false data requests. This common type of attack occupies the machine with malicious requests, preventing legitimate traffic from passing through. Two types of volumetric attacks are UDP floods and ICMP floods. UDP attacks exploit the UDP format's fast data transmission feature to generate amplification and reflection attacks. ICMP floods send false error requests to network nodes, causing the target to become overwhelmed and unable to respond to real requests.
Protocol Attacks
Protocol attacks consume server resources by targeting network areas responsible for verifying connections with slow pings, malformed pings, and partial packets. This overloads the memory buffer in the target computer, causing a system crash. Web application firewalls (WAF) may also be compromised by protocol attacks, making it impossible for firewalls to stop DDoS threats of this type. The SYN flood attack is a prevalent protocol attack that initiates a TCP/IP connection without finalizing it. It works by sending a SYN packet from the client, followed by an ACK packet from the server. The client is then supposed to respond with another ACK packet but doesn't, causing the server to wait and exhaust its resources.
Application Layer Attacks
Application layer attacks target the L7 layer, focusing on web traffic through HTTP, HTTPS, DNS, or SMTP. They exploit vulnerabilities in the application layer to prevent content delivery, and are difficult to prevent because they use minimal resources, often just a single machine. This makes it challenging to distinguish between legitimate and malicious traffic. Hackers can also combine various approaches for a multi-pronged attack on a target.
Business Impact of a DDoS Attack
DDoS attacks are not going anywhere soon, mostly because they are often successful. The financial and operational impact of an effective DDoS attack can be devastating. Businesses of all sizes are vulnerable to these threats, and the consequences can be catastrophic. In addition to the obvious financial losses, a successful attack can also cause serious reputational damage. System disruptions can lead to a loss of productivity, customer dissatisfaction, and permanently dissatisfied customers.
DDoS attacks can also provide an entry point for malicious actors to gain access to sensitive information, putting an organization’s data and resources at risk. It is therefore essential for businesses to take steps to protect themselves from these attacks, such as investing in robust DDoS protection solutions and instituting a comprehensive cybersecurity strategy.
Ways to Prevent a DDoS Attack
While automation technology can aid in the prevention of cyberattack, it cannot provide complete protection without the addition of human intelligence and monitoring. Traditional web structures are no longer adequate to ensure maximum security. To achieve the best protection, it is recommended to implement a security platform that is developed and overseen by skilled and dedicated engineers and / or a SOC team.
Knowledge of DDoS attack methods and awareness of network behavior are essential in thwarting intrusions, interruptions, and downtime caused by cyberattacks. The following tips may be useful in preventing these threats:
Monitor Network
To effectively mitigate DDoS threats, the initial step is to detect an impending attack. This necessitates the use of technology that enables real-time and visual monitoring of your network. Understanding the typical bandwidth consumption of your website is vital so that anomalies can be identified promptly. DDoS attacks present visible indicators, and being well-versed with your network's typical behavior can aid in the swift detection of such attacks in real-time.
Maintain Digital Hygiene
Every business can implement straightforward measures to guarantee a fundamental level of protection against DDoS threats. These measures include adhering to best practices such as utilizing intricate passwords, enforcing periodic password resets, and refraining from recording or writing down passwords. Although these practices may appear insignificant, it is astonishing how frequently businesses neglect basic security hygiene, leading to compromise.
Establish Traffic Thresholds
Several technical security measures can partially alleviate the impact of DDoS attacks. These measures include implementing traffic thresholds and limits, such as rate limiting on your router and filtering packets from dubious sources. Adopting lower thresholds for SYN, ICMP, and UDP flood drop, IP blacklisting, geo-blocking, and signature identification are additional techniques that can serve as a preliminary level of mitigation. Even though these are uncomplicated measures that can provide additional time, DDoS attacks are continuously evolving in sophistication, and further strategies are necessary to completely prevent them.
Maintain Security Infrastructure
The strength of your network is determined by its weakest link. As such, it is crucial to recognize the presence of legacy and outdated systems in your infrastructure, as they often serve as entry points for attacks when compromised. It is advisable to maintain the latest versions of your data center and systems and to patch your web application firewalls and other network security programs. Additionally, collaborating with your ISP or hosting provider, security and data center vendor to integrate advanced protection capabilities is a prudent course of action.
Establish a Planned Response
Once a DDoS attack occurs, it will be too late to devise a response plan. It is necessary to prepare a response plan in advance to minimize the impact. An ideal response plan should comprise a checklist of tools, a response team, escalation protocols, and a strategy for promptly communicating updates to stakeholders.
Ensure Enough Server Capacity
Volumetric DDoS attacks function by flooding the network bandwidth, making it crucial to counter them by over provisioning bandwidth. By guaranteeing that your server capacity can accommodate high traffic spikes via additional bandwidth, you can be equipped for sudden and unforeseen surges in traffic due to DDoS attacks. It is important to note that this approach may not wholly halt a DDoS attack, but it will provide a brief window to prepare additional defenses before your resources are exhausted.
Arkose Labs Deters DDoS Attacks
The Arkose Labs platform offers security and fraud teams the ability to detect and combat large-scale, persistent attacks by providing real-time risk classifications of traffic, utilizing multi-faceted machine learning and round-the-clock analysis from a Security Operations Center (SOC).
The Arkose Labs’ security platform differs from black box solutions by using a "clear box" approach that emphasizes delivering actionable insights with clear explanations for risk classifications and a straightforward path to remediation. This approach surpasses solutions that provide probabilistic risk scores, which often require extensive resource time to integrate, fine-tune, and establish downstream authentication workflows.
Arkose Labs' unique combination of risk classification and dynamic attack response is effective against DDoS attacks. It provides the appropriate pressure to the attack signature while minimizing disruption to legitimate users. With its advanced capabilities, security and fraud teams can quickly identify and mitigate DDoS attacks, helping to safeguard their networks and systems.
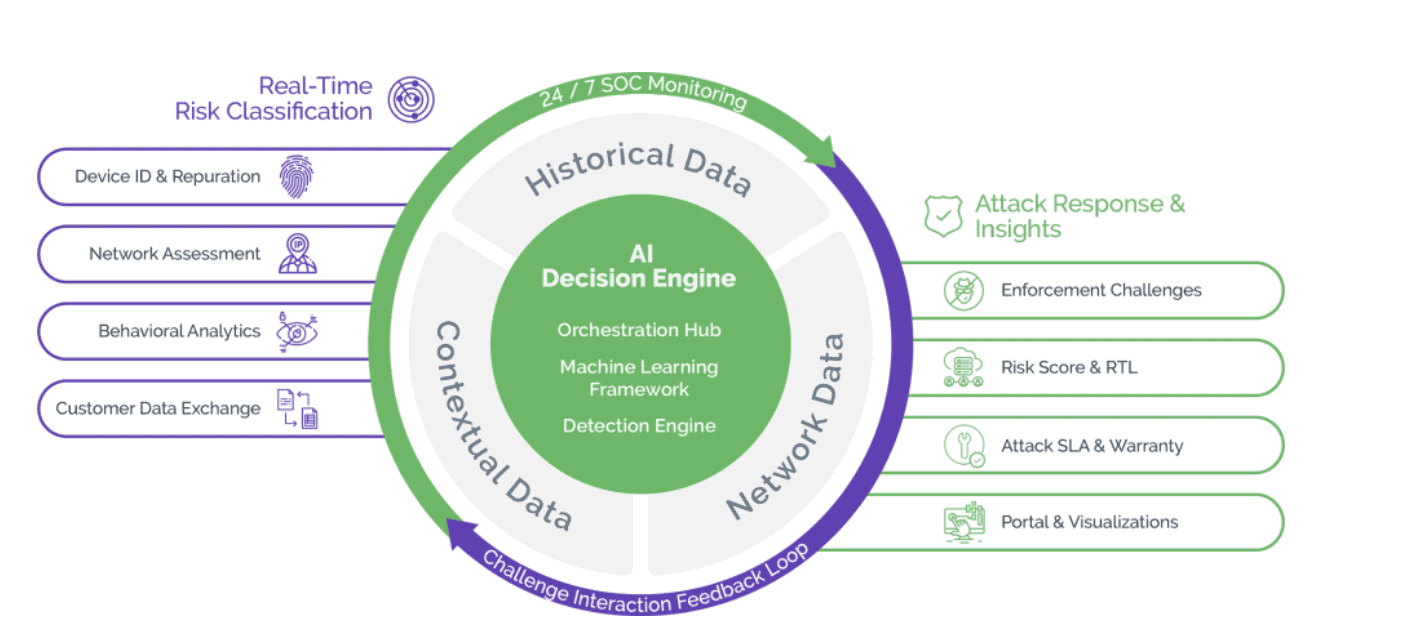
The Arkose Labs platform utilizes an AI-powered decision engine to effectively protect against real-time attacks. This engine processes real-time signals and deep historical intelligence to generate a targeted response to any attack. The engine is constantly learning from its assessment of past interactions, ensuring that genuine users can pass through without difficulty while adapting to emerging attack tactics.
To find out how we can help protect your business from potential DDoS attacks, contact us anytime or request a demo.
Bot Management Software: Guaranteed Results Stopping Bots With Arkose Labs
- What is a DDoS Attack?
- Types of DDoS Attacks
- Volumetric Attacks
- Protocol Attacks
- Application Layer Attacks
- Business Impact of a DDoS Attack
- Ways to Prevent a DDoS Attack
- Monitor Network
- Maintain Digital Hygiene
- Establish Traffic Thresholds
- Maintain Security Infrastructure
- Establish a Planned Response
- Ensure Enough Server Capacity
- Arkose Labs Deters DDoS Attacks

