What is International Revenue Share Fraud (IRSF)?
International Revenue Share Fraud or IRSF is where attackers artificially inflate traffic to international premium rate numbers (IPRN). Usually, attackers collude with telecom operators and premium rate service providers to orchestrate IRSF. It is one of the most persistent frauds plaguing the telecom industry which causes losses running into millions of dollars annually. That said, IRSF and artificially inflated traffic are not restricted to the telecom industry alone. They are evolving into a menacing challenge for any digital business that uses a voice- or SMS-based one-time password (OTP).
The modus operandi of IRSF
Bad actors use stolen SIM cards as well as compromised mobile devices and corporate PBX phones to make innumerable fake calls to premium numbers. They also exploit voice- or SMS-based OTPs to execute International Revenue Share Fraud.
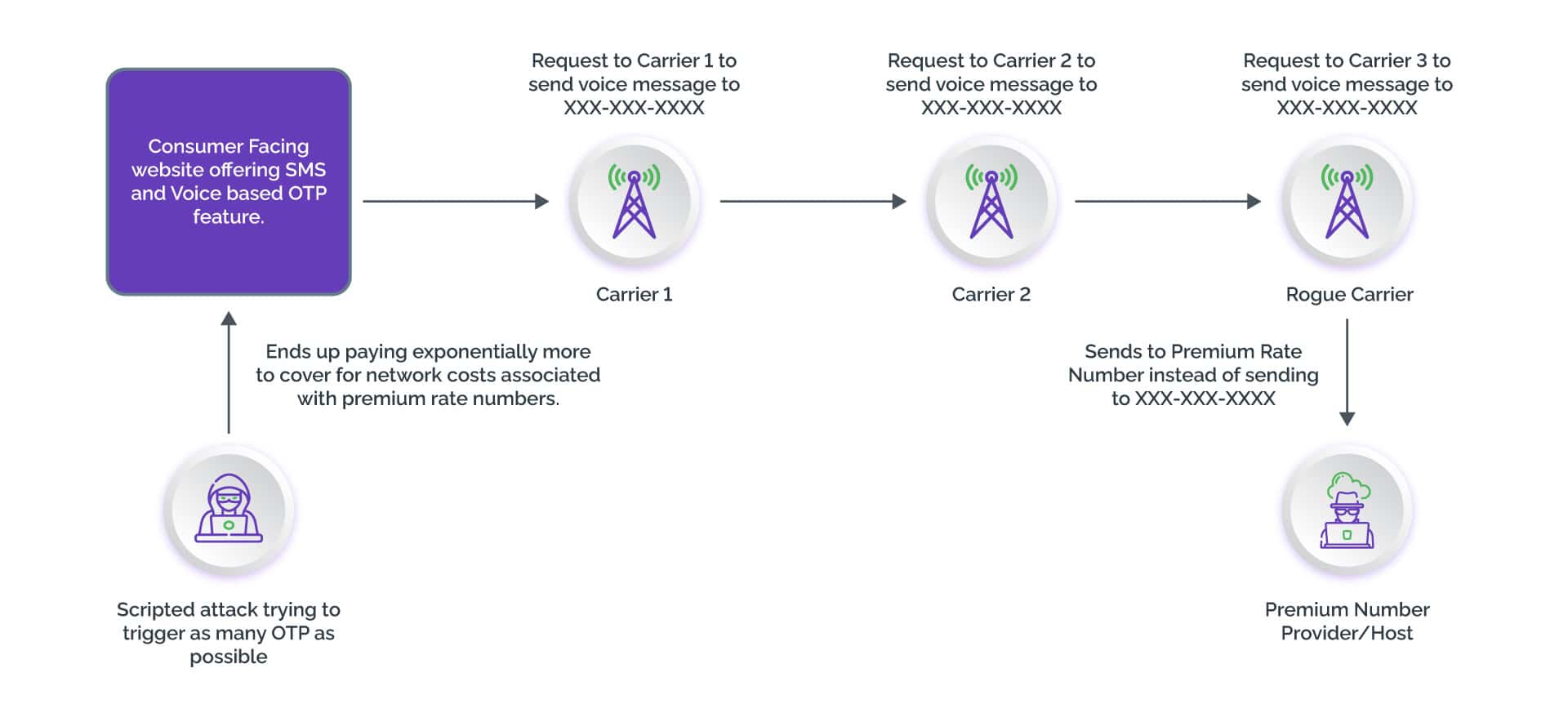
The steps of an OTP-based IRSF are:
Step 1: An attacker initiates a manual or a scripted attack on a webpage to trigger voice- or SMS-based OTPs. Depending on the returns, attackers can opt for high-volume attacks or low-and-slow attacks.
Step 2: The consumer-facing business forwards the OTP request to a cloud communication provider.
Step 3: The provider forwards the request to a carrier. This request is necessary as multiple network providers in the region are involved before the OTP can reach the intended consumer.
Step 4: A compromised carrier, colluding with an attacker, forwards the request to an IPR number instead of the intended recipient.
Step 5: ‘Terminating’ a call on an IPR number is expensive; and ultimately it is the consumer-facing business that must absorb the losses.
Step 6: Attackers earn huge profits from their share of the fraud, usually $1 or more per transaction.
IRSF Continues to be Lucrative for Attackers
IRSF is a lucrative proposition for attackers due to the low risks involved. Attackers can execute the fraud from a distance. They can remotely redirect the inter-carrier billing to pocket the money from expensive telecom traffic.
Bad actors are also using smart IoT-enabled infrastructures to their advantage. They overwhelm the IoT-enabled deployments with artificially inflated traffic and disrupt their functioning to seek ransom. All they need to do is to repeatedly execute fraud through the IoT critical infrastructure until the deployment is closed down.
IRSF is difficult to detect
Businesses face an uphill task trying to check IRSF due to sheer complexity of the telecom network with multiple carriers involved. This complexity is the prime reason for the delay in identifying and blocking the called numbers. Since the numbers used in IRSF do not belong to the national numbering plan, detecting them becomes even more difficult.
Many attackers opt for low-and-slow attacks to bypass the attack identification rules. Businesses also lack visibility into downstream activities, which prevents them from arresting IRSF early in its tracks.
Ways businesses can fight IRSF and artificially inflated traffic
There are three attack vectors of IRSF that can help businesses protect themselves. These include:
- An attack script
- A range of unused PRNs
- Partnership with rogue networks
Businesses may not be equipped to deal with collusion. However, they can study attack scripts and unused PRNs to predict and mitigateIRSF. To protect themselves, businesses can:
- Prevent scripted attacks – Using a script breaker such as CAPTCHA can help stop a scripted attack. Like the attackers, who would evolve the script, businesses too should evolve to stop the attack.
- Gain PRN intelligence – Information about unused PRN ranges can help businesses identify rogue PRNs and predict the possibility of an IRSF attack. Attackers generally buy unused PRN ranges to attack. Similarly, phone intelligence data can enable businesses to leverage cross-customer data and determine if the number was used elsewhere to commit IRSF.
- Deploy billing alerts – Using billing alerts for steep transactions can help businesses identify IRSF.
- Prepare: Businesses can leverage network-level and signaling data and use smart fraud prevention tools to prepare themselves.
Limitations of Reactive Security Approaches
Traditional fraud defense mechanisms cannot keep pace with the fast-evolving threat landscape. What worked a couple of years back, may no longer be viable or reliable today. IRSF requires a carefully planned strategy that allows for continuous and proactive monitoring.
Businesses must leverage digital intelligence and use the latest technologies to mitigate the risks they face. They should adopt an approach that goes beyond mitigation and allows them to deter fraud – an approach that will ensure fraud prevention in the long-term.


