How it works
An attacker initiates a manual or scripted attack on a webpage to trigger voice, or SMS-based, OTPs. These can either be high-volume attacks or low and slow attacks.
The consumer-facing business generally forwards the OTP request to a cloud communication provider.
The provider would then send a request to a carrier. In any given region, there are generally multiple network providers involved before the OTP can reach the intended consumer.
In this chain sits a ‘rogue carrier’ that may have an agreement with the PRN provider/host to forward the request to the PRN number instead of the intended recipient, whenever the network provider gets a OTP delivery request.
Since ‘terminating’ a call on a PRN is expensive, the costs keep adding up for the consumer-facing business to eventually fulfill.
The fraudsters end up earning a good share ($1 or more) per transaction.
Early Detection to Prevent Costly IRSF Losses
The problem with IRSF is that oftentimes it is not detected until it is too late and fraudsters have already done their damage. It’s challenging for businesses to get visibility into these attacks early enough to prevent them, as fraudsters have access to a range of tools that can help them bypass identification systems.
However, businesses can thwart these attacks by utilizing robust anti-automation technology. Fraudsters rely heavily on automated scripts to carry out these attacks at scale. Businesses should have defenses in place that can detect even human-like bots, and be able to stop them. Since fraudsters often evolve their attacks to overcome known defenses, businesses should have in place a security platform that can learn and change to adapt to evolving attacks.
Bots keep getting smarter and more difficult to stop, so businesses should have fraud defenses in place that are resilient to even the latest innovations in offensive machine learning. By accurately detecting advanced bots, and having the means to stop them, businesses can ensure that IRSF attacks are stopped.
Beyond that, knowing unused PRN ranges to predict the possibility of an IRSF attack, along with access to phone intelligence data is useful to see if the same numbers were used elsewhere to commit IRSF, are helpful tools in fighting these attacks.
The Arkose Labs Approach
Businesses can insert Arkose Labs at any touchpoint which is protected by one-time passwords. such as the login flow or new account registration, in order to detect fraudulent traffic. Furthermore, due to Arkose Labs’ unique in-session authentication that combined real time risk classification with interactive challenges, businesses will be able to rely less on multi-factor authentication methods.
Accurate Classification:
Arkose Labs analyzes hundreds of data points around device, network, behavior and location to create “telltales” to determine whether traffic is suspicious or not. This is partially informed by data from our global network, where we create telltales of known previous attacks. Arkose Labs also can implement industry-specific telltales customized for individual merchants based upon their business model and industry Traffic is then segmented based on whether it is likely to be legitimate, a bot or a malicious human, which informs the platform of any required secondary screening and the type of enforcement challenge shown.
Challenge and interact:
To understand the intent of traffic in a deterministic way, secondary screening must be paired with the risk assessments stage. The platform tests and challenges high-risk traffic using interactive technology designed to foil even the most advanced automation. Meanwhile, increasingly complex challenges are served to human attackers, which increases the amount of time it takes them to complete a task, thus reducing their ROI. This leads them to abandon their attacks. The platform tailors the type of challenge based on the nature of the attack.
The Arkose Advantage
Long-Term Deterrence
Arkose Labs increases the cost of fraud making it economically unsustainable to fulfill attacks
Effortless Management
Powerful decision engine selects the most effective response strategy to reduce manual reviews
Protection Across The Customer Journey
One flexible solution that protects against different attack vectors and extensive user touchpoints
Early Detection
Eliminate losses, reduce costs, and streamline efforts by preventing attacks before they advance in your ecosystem
Privacy Friendly
Arkose Lab technology achieves unparalleled accuracy without compromising data protection compliance
Results Fast
New customers will see results within days, not weeks or months
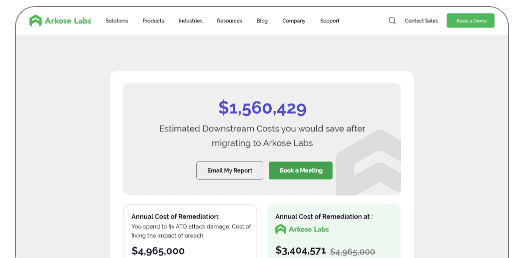
Now your business can estimate the cost savings associated with stopping SMS Toll Fraud, also known as IRSF.
SMS Toll Fraud (IRSF) is a type of cybercrime in which hackers use stolen accounts/numbers to send large volumes of SMS messages to premium rate numbers, resulting in significant charges for the account owner. IRSF can disrupt business operations, damage a company's reputation, and lead to major financial losses, as well as a diminished ROI.
Quickly and easily estimate the potential cost savings associated with stopping SMS toll fraud, to make better decisions about cybersecurity strategies for the new year.
Use our calculator to estimate the potential cost savings from stopping SMS toll fraud in the new year!

$1 million Sms Toll Fraud Warranty
Introducing the industry’s first warranty against telecommunications service provider costs resulting from SMS toll fraud attacks.
Read About Warranty BenefitsBook a Meeting
Meet with a fraud and account security expert