SQL Injection, Explained
Cyber threats are a growing concern for businesses, and one of the most common cyberattacks is SQL injection. But what exactly is SQL injection? How does it work? And what can you do to prevent it? Here, we will break down the threat of SQL injection and explore how attackers exploit vulnerabilities in your system's SQL queries to gain unauthorized access to sensitive data. We also discuss the different types of SQL injection attacks, their impacts on servers and databases, and explain how bot management and the prevention of SQL injection attacks are related in the context of web application security.
What is SQL Injection?
SQL injection (SQLi) is a type of attack that targets vulnerabilities in web applications' handling of SQL queries. It occurs when an attacker manipulates user-supplied data to modify the intended SQL commands executed by the application. By exploiting these vulnerabilities, attackers can gain unauthorized access to the underlying database, extract sensitive information, modify data, or even execute arbitrary commands on the server. These attacks can have severe consequences for the security and integrity of the underlying SQL server, SQL database, and associated web application.
Successful attacks can expose sensitive information stored in the database, including user credentials, personal data, or financial records. Attackers may also tamper with the database tables, modifying or deleting data, which can have serious consequences for the application's integrity and functionality.
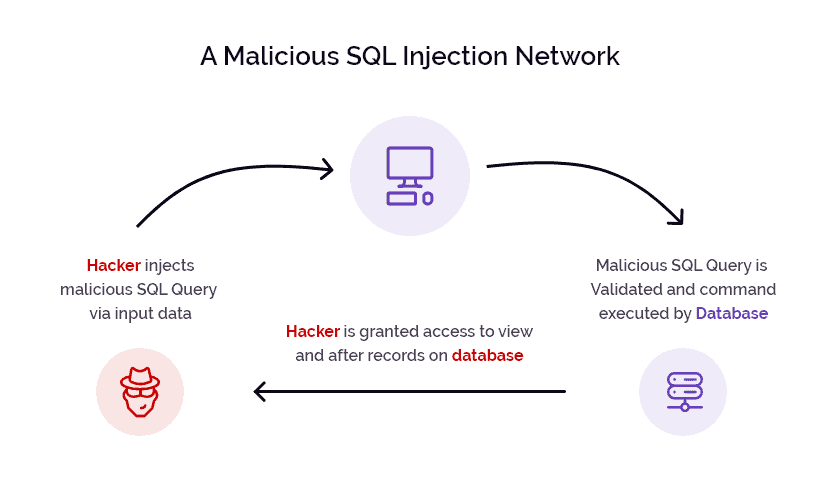
Understanding SQL Injection
In order to fully comprehend how SQLi attacks work, it's important to have a basic understanding of SQL (Structured Query Language). SQL is a programming language that is used to manage data in relational database management systems (RDBMS). SQL syntax is used to construct and manipulate databases.
The SQL server manages and stores the application's database, and is a prime target for SQL injection attacks. The injection occurs through the web page's forms or input fields, where attackers inject malicious SQL code. This code can be designed to extract sensitive data from the database, modify existing data, or even gain control over the entire SQL server.
The web server acts as an intermediary between the user's web browser and the SQL server. If the web server does not properly validate or sanitize user input, it can pass the injected SQL commands to the SQL server without any checks. This allows the attacker to exploit the SQL injection vulnerability and execute their malicious code.
Web forms, such as login forms or search boxes, are commonly targeted in SQL injection attacks. Attackers can manipulate the input fields in these forms to inject their own SQL code. For example, an attacker may inject additional SQL statements that modify the original query, allowing them to bypass authentication mechanisms and gain unauthorized access to sensitive information.
If successful, a SQL injection attack can extend its impact beyond the database and affect the operating system hosting the SQL server. In some cases, attackers can execute arbitrary commands on the server, potentially compromising the entire system. This underscores the importance of keeping the web server, operating system, and associated software up-to-date with security patches and best practices.
What Does SQL Injection Look Like?
SQL injection attacks work by manipulating SQL queries in the web application's backend. Attackers can inject malicious SQL code into vulnerable parameters, such as user input fields or URLs. The backend server can then execute this code, which could have unintended consequences.
For instance, if an attacker injects the following code into a login form:
' OR 1=1 --
The backend server will execute the following SQL query:
SELECT * FROM users WHERE username='' OR 1=1--' AND password=''
This query will return all records from the 'users' table, effectively bypassing the login page altogether.
Common Types of SQL Injection Attacks
SQL injection attacks come in several forms, including:
- Union-based SQL injection: This type of attack involves using the UNION statement to combine the results of two or more SELECT statements. This can be used to retrieve data from tables that the attacker does not have access to.
- Error-based SQL injection: Error-based SQL injection involves triggering errors in the SQL query to reveal information about the backend database. This technique can be used to extract sensitive data or gain access to the system. For example, an attacker could use an error-based SQL injection to retrieve the version of the database software, which could then be used to find known vulnerabilities. To prevent error-based SQL injection attacks, it is important to sanitize user input and use prepared statements. It is also important to limit the amount of information revealed in error messages.
- Blind SQL injection: This type of attack involves sending SQL queries to the backend server and analyzing the responses to determine whether the query was successful or not. This can be used to extract information from the database without actually retrieving any data.
- Time-based SQL injection: This type of attack involves using time delays in SQL queries to extract information from the database. For example, an attacker might use the SLEEP function to delay the response from the backend server, allowing them to determine whether a query was successful or not.
Developers should be aware of these types of attacks and take steps to prevent them, such as using parameterized queries and input validation.
About SQL Queries
To prevent SQL injection attacks, it is essential to understand SQL queries. Attackers can manipulate data by targeting vulnerabilities in web application code using malicious SQL statements through the user input field or URL. Securing your web application involves using parameterized queries with input validation and implementing security measures such as a web application firewall (WAF). Following the OWASP (open web application security project) Top Ten Guidelines for web application security can also help prevent successful SQL Injection attacks.

What Are SQL Query Parameters?
SQL query parameters are values entered by users to execute SQL queries. Attackers can exploit these parameters to inject harmful code into the database, leading to data loss or unauthorized access. Preventing SQL injection requires proper input validation and parameterization of queries, which separate user input from the code and make it difficult for attackers to manipulate.
SQL Syntax Basics for Injection Attacks
Understanding SQL syntax is crucial to preventing SQL injection attacks. Attackers exploit vulnerabilities in web applications by inserting malicious code into user input fields. The injected code modifies the original SQL statement, giving attackers access to sensitive data such as usernames and passwords. Developers must utilize security measures like prepared statements or parameterized queries while building web applications. These measures separate user input from the code and make it more difficult for attackers to manipulate the query string.
Identifying SQL Injection Vulnerabilities
Hackers may take advantage of the user-input parameters used in SQL queries to introduce malicious code into the system, and the ease of automation makes these attacks attractive on a large scale. Database errors can also provide valuable clues about potential SQL injection vulnerabilities. Developers should handle error messages returned by the database carefully to avoid revealing sensitive information or internal system details. Proper error handling can lessen the chance of exposing crucial information that attackers might use against you.
Regular security audits, code reviews, and penetration testing are essential to identifying and addressing SQL injection vulnerabilities. Security-conscious development practices and ongoing monitoring can significantly reduce the risk of successful SQL injection attacks, protecting both the web application and the associated SQL server from potential compromise. Web application security plays a crucial role in safeguarding against potential threats.
How to Prevent SQL Injection Attacks
One of the critical aspects of preventing SQL injection attacks is proper authentication and handling of user credentials. Web applications should enforce secure authentication mechanisms, such as strong password policies and encryption of stored passwords. It's essential to validate and sanitize user input to prevent SQL injection vulnerabilities. Prepared statements or parameterized queries can be used to separate user input from the SQL commands, eliminating the risk of injection.
Fortunately, there are several steps that developers can take to prevent SQL injection attacks:
Parameterized Queries
Parameterized queries separate user input from SQL code, making it impossible for attackers to manipulate the query itself. Instead of embedding user input directly into the query, developers use placeholders that are replaced with user input at runtime.
Parameterized queries can be used with most programming languages and database systems, including PHP, Java, .NET, and MySQL. They are generally easy to implement and can provide a high level of protection against SQL injection attacks.
Escaping User Input to Prevent SQL Injection
Escaping user input is a crucial security measure that web applications must take to prevent SQL injection. To do this effectively, developers need to modify user input by adding special characters. Along with this technique, using prepared statements and parameterized queries can significantly reduce the risk of SQL injection attacks. Proper input validation and sanitization are also essential for securing web applications against such attacks.
Least Privilege
Limiting the privileges of database accounts used by the web application can minimize the impact of a successful SQL injection attack. The principle of least privilege should be followed, ensuring that the application has only the necessary permissions to access the required database tables and execute specific SQL commands.
Whitelisting vs. Blacklisting for SQL Injection Prevention
Web developers should avoid using blacklisting techniques that involve listing prohibited input types; instead, they should opt for whitelisting techniques like allowing only approved input types to be used in SQL queries. Whitelisting makes it more difficult for attackers to exploit vulnerabilities, and limits the risk of data breaches or site crashes.
SQL Injection and Bot Management
Bot management and the prevention of SQL injection attacks are related in the context of web application security. Arkose Labs Bot Manager helps to detect and mitigate various types of malicious activities, including SQL injection attacks carried out by automated bots.
Bot management solutions employ various techniques to identify and block such malicious bots. They use advanced algorithms and behavioral analysis to distinguish between legitimate users and automated bots. When it comes to preventing SQL injection attacks specifically, bot management solutions can play a role in several ways:
- Request Analysis: Bot management solutions analyze incoming requests to identify patterns and anomalies associated with SQL injection attacks. They examine parameters, payloads, and other indicators to detect suspicious SQL injection attempts and block them before they reach the web application.
- Challenge-Response Mechanisms: Bot management solutions can implement CAPTCHA challenges or other forms of interactive authentication to verify the user's behavior and differentiate between humans and automated bots. These mechanisms can help prevent bots from successfully injecting malicious SQL commands.
- Rate Limiting: Bot management solutions can enforce rate limits on incoming requests to mitigate the impact of automated bot attacks, including SQL injection attacks. By limiting the number of requests a user or IP address can make within a specified time frame, they can prevent bots from launching a large number of injection attempts.
- Behavior Analysis: Bot management solutions employ behavioral analysis to identify unusual patterns or suspicious activities that could indicate SQL injection attacks. By analyzing the behavior of incoming requests, they can detect abnormal SQL-related activities and take appropriate action to block the attacker.
By implementing a robust bot management solution, organizations can strengthen their defenses against SQL injection attacks carried out by automated bots. Such solutions provide an additional layer of protection, complementing secure coding practices and other security measures aimed at preventing SQL injection vulnerabilities in web applications.
Conclusion
SQL injection is a severe threat to the security of your server and database. Attackers can exploit SQL vulnerabilities to gain unauthorized access to sensitive information, manipulate data, or even take control of your entire system. You must understand the common types of attacks and the techniques used by attackers to prevent them from exploiting your system's vulnerabilities. Adopting the latest technologies, complying with OWASP guidelines, and using a bot management platform like Arkose Labs, can help you stay safe from such attacks.
For more information on how to secure your system against SQL injection attacks, book a demo today!

