Phishing attacks continue to be one of the most used attack methods by bad actors to steal sensitive information. As per the latest statistics produced by the FBI’s Internet Crime Complaint Center (IC3), phishing attacks are the number one crime type method and account for 37.5% of all the reported complaints (total cases 800,944)1. The FBI’s IC3 report also estimates that the total reported complaints, including phishing, contributed to losses exceeding $10.3 billion (about $32 per person in the U.S.) in 2022. As per Verizon’s Data Breach Report, phishing attacks accounted for over 20% of all the data breach attacks analyzed and second only to credential breach2.
Figure 1:IC3 2022 Report
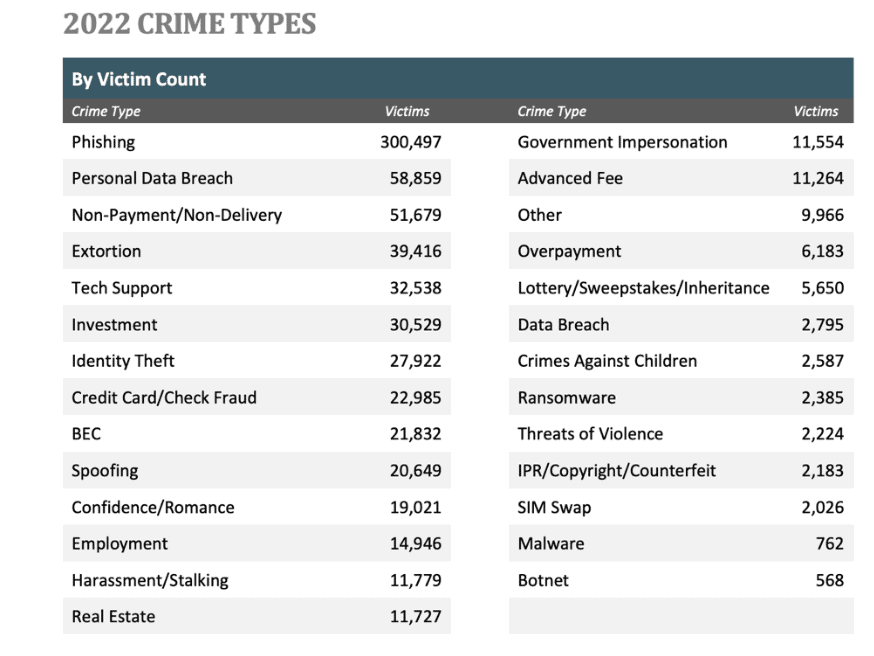
3
Phishing methods and their efficacy have evolved in recent years with the introduction of sophisticated platforms that are built to easily evade detection. Industry analysis found that attackers used malicious URLs as a method of attack in 60% to 70% of the cases as compared to attachments. The new breed of phishing methods, like Adversary-in-the-Middle (AITM) reverse proxy, and cybercrime-as-a-service platforms like EvilProxy and Caffeine Proxy, are making it difficult to detect and mitigate attacks.
Traditional phishing detection solutions either rely on curated domain block lists or heuristic analysis of the URL or website contents. Domain block lists are produced by different methods but are usually delayed. Further, the level of accuracy depends on if the list is scrubbed or not. The heuristic-based methods use text and similarity analysis methods like:
- Homograph analysis
- Typing distance analysis
- Typosquatting detection
- Special character analysis
- Domain reputation analysis
- IP Reputation
Traditional methods of phishing detection are effective against unsophisticated attacks but fall short in detecting moderately advanced attacks. A bad actor could easily bypass most of the heuristic-based checks, creating malicious domains with unsuspecting domain names and deployment services. For instance, about 20% of the phishing domains we analyzed during February and March were less than 15-characters long and would not be detected by typical URL string checks.
More advanced detection solutions rely on methods like brand logo detection and website image matching. These methods, in conjunction with the traditional methods, can help achieve higher accuracy but at a cost. These solutions use technologies like image recognition that are expensive to run on a large scale, especially given the number of websites registered or updated daily. An analysis of Certificate Transparency Logs (CT Logs) shows that there are more than 1000 new certificates issued per minute, on average. If the number of new certificates issued is a good proxy for the volume of new domains, the cost of proactively analyzing each of those domains in a timely manner is going to be exorbitant.
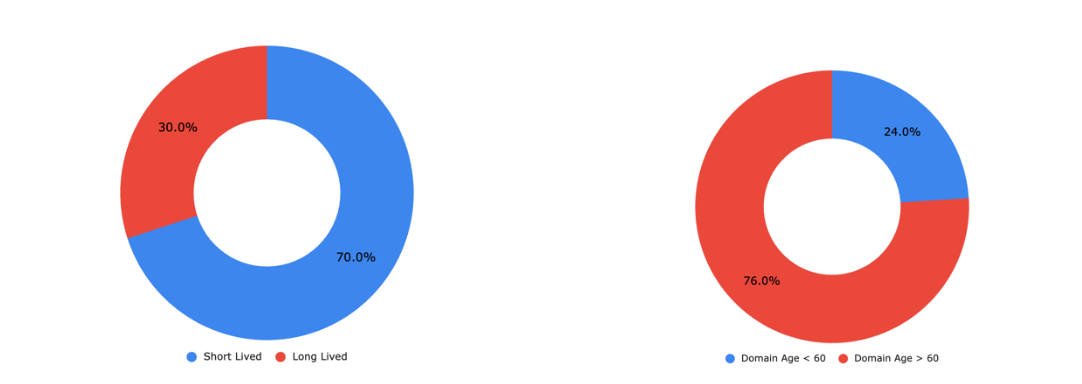
Ease of access and lower infrastructure cost has resulted in bad actors creating short-lived websites that are disposed of as soon as the phishing campaign is finished. These websites are often hosted on popular cloud providers and content delivery networks to evade detection by IP reputation methods. We analyzed a sample set of 250 malicious websites that managed to evade standard detection techniques and found the following:
- 24% of malicious websites were created in the last 60 days
- 70% of the malicious sites had stopped resolving after short campaign
Phishing continues to quickly evolve, and like other crime types, needs a comprehensive security posture to defend against the malicious attacks. While traditional detection and mitigation methods provide security to a certain extent, they are often unable to provide comprehensive security within a reasonable cost and complexity.
If you would like to learn more about how Arkose Labs can help to secure your enterprise from advanced threats like modern phishing attacks, book a meeting with us today.


