SMS pumping, also known as SMS traffic pumping or International Revenue Share Fraud (IRSF), is a growing menace in the telecommunications industry. It is a type of fraud where cybercriminals manipulate mobile networks to inflate charges for SMS messages sent to premium or high-cost destinations. It is becoming a huge challenge for any digital business that uses web forms to collect mobile numbers, or businesses that use SMS-based one-time passcodes (OTP).
What is SMS Pumping Fraud?
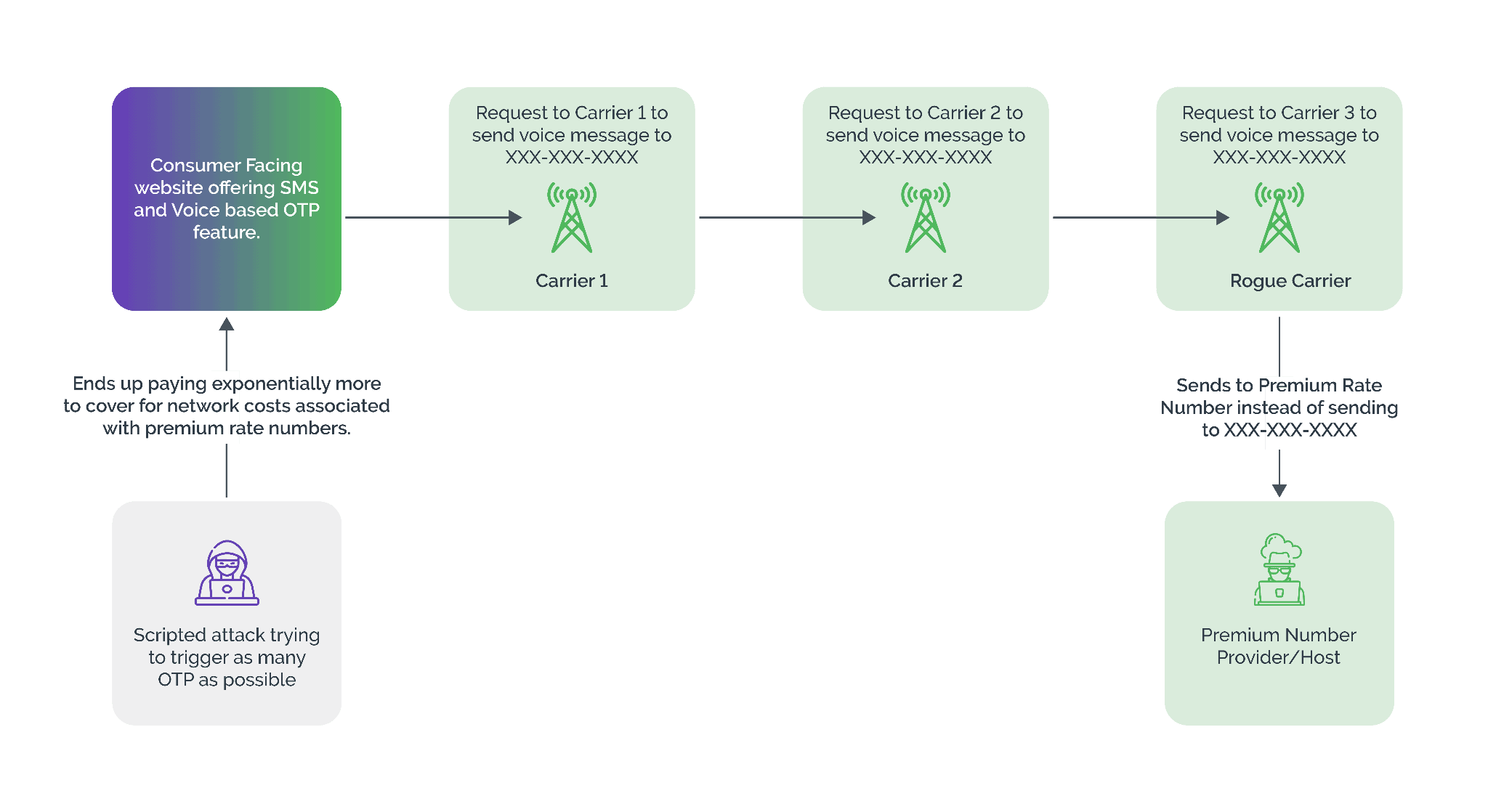
SMS pumping fraud, also known as SMS toll fraud, is a type of bot attack that sends large volumes of SMS messages to premium rate numbers, resulting in fraudulent SMS charges to a business. These charges can amount to millions of dollars a month. Often, attackers collude with rogue carriers, or illegally access a mobile network operator's networks to reroute SMS messages to premium rate numbers or countries. Next, to generate a per-transaction reward of $1 or more, malicious actors launch automated attacks on digital touchpoints, such as logins and account sign-ups, that activate OTP.
How SMS Traffic Pumping Works
SMS traffic pumping is a fairly involved scheme. In these attacks, the fraudsters send SMS messages to a range of numbers controlled by a specific mobile network operator (MNO).
A criminal organization may try to collude with a specific MNO to generate revenue by exploiting the provider's phone numbers. By working with an MNO, a fraudster can use automated systems to send thousands of text messages to high-cost destinations, inflating the cost of the attack for a business, which is then on the hook for millions of dollars of fraudulent SMS charges.
When it comes to SMS pumping, the network traffic routes involved are incredibly complex and varied. This makes it difficult for businesses to detect bad actors and prevent fraudulent activity. The process usually involves multiple parties, including aggregators, content providers, and mobile carriers. Each party uses its own routing mechanisms to forward messages, obscuring the source of the fraudulent activity. As a result, detecting and stopping SMS pumping can be especially challenging for businesses.
SMS Pumping Fraud Examples
SMS pumping fraud can take many forms. Attacks may be targeted at web forms that ask a consumer for a mobile number in exchange for product or subscription discounts or other benefits. Another attack vector is websites that send one-time passcodes (OTP) for login attempts.
Web Form Attacks
In this type of attack, a business that collects mobile numbers in a popup web form is victimized when a fraudster uses bots to enter thousands of numbers into the phone number input field. The business could end up sending thousands of messages to high-cost SMS destinations or premium rate phone numbers. The business believes it is sending messages to potential customers, but it is actually a victim of SMS pumping.
SMS OTP Fraud
The banking industry is a frequent target of SMS pumping because fraudsters often focus on websites that send a one-time passcode for login attempts.
In these types of attacks, a cybercriminal obtains a cache of stolen credentials on the dark web. Then, they use OTP bots to quickly attempt a large number of logins on the targeted website or app. The targeted company will then incur huge costs for the delivery of a large number of OTPs as a result of the high number of fraudulent login attempts. The company will likely owe thousands—or millions—of dollars due to the high number of SMS messages diverted to high-cost SMS nations.
How to Detect SMS Pumping
A few ways to detect SMS pumping include:
- Monitoring the success of OTP verification, and look for high volumes of incomplete login attempts.
- Watch for adjacent number inputs in rapid succession.
- Look for unexpected traffic spikes.
Monitor the Success of OTP Verification
One effective way to detect SMS pumping is to monitor the success rate of OTP verification attempts. Because attackers often attempt to access accounts using fraudulent credentials, a high number of incomplete login attempts can be a sign of SMS pumping.
Look for Adjacent Number Inputs
One way to detect SMS pumping is by looking for patterns of adjacent number inputs in rapid succession. Bad actors may use automated tools or bots to generate high volumes of messages, often from sequential phone numbers, as a way to bypass spam filters and detection mechanisms. If you notice a sudden spike in messaging activity from unknown numbers or see patterns of sequential numbers, notify your mobile carrier or traffic provider immediately. Rapidly responding to these instances can help prevent further damage and potential financial losses.
Report Unexpected Traffic Spikes
Detecting SMS pumping requires vigilance and prompt action. One key strategy is to report unexpected spikes in traffic and investigate their source immediately. This can be done using monitoring tools that detect any unusual surges in messaging volumes or login attempts. Once detected, you should investigate the source of the traffic to determine if it's legitimate or a result of SMS pumping fraud.

How to Prevent SMS Traffic Pumping
Preventing SMS pumping attacks is critical because they can be very difficult to notice in real time. Tactics like setting message limits, using two-factor authentication (2FA) or multi-factor authentication (MFA) for premium services, and using a CAPTCHA to stop bot traffic, make it more likely that a business will be able to prevent SMS pumping.
Rate Limiting
One of the most effective ways to prevent SMS pumping is through rate limiting, which involves setting thresholds for message volume and frequency. By limiting the number of messages that can be sent from a single source in a given period, businesses can effectively mitigate the risk of SMS pumping attacks.
Rate limiting can also help protect against other forms of spam and abuse, such as email flooding or website scraping. However, effective rate limiting requires careful monitoring of traffic patterns and adjusting thresholds as needed to balance security with user experience.
Build a Blocking List
Building a blocking list based on the spammers' country codes is a successful strategy to stop SMS pumping. This can be done by working with your MNO or using third-party filtering software. By creating a list of blocked countries, you can prevent messages from being sent to numbers in those areas. This approach is most effective when targeting countries that have a higher risk of SMS pumping, such as regions with lower telecommunications regulations or higher rates of fraud activity.
It is essential to keep your blocking list up-to-date and accurate. Attackers are always looking for new ways to bypass security measures and exploit vulnerabilities. Review your blocking list regularly, and take note if you see a high number of SMS messages sent to an unexpected country.
Detect and Deter Bots with CAPTCHA
Fraudsters who want to make money through SMS pumping fraud frequently use malicious bots, which are software designed to automate tasks online. While traditional CAPTCHAs are unable to block most bots, a modern CAPTCHA—such as the Arkose MatchKey Challenge—can effectively detect and deter bots from infiltrating your SMS system. Arkose MatchKey Challenge is an intuitive challenge-response solution that thwarts attackers from accessing companies’ network systems by applying strategic friction based on challenges that evolve through constant iteration. It's an excellent tool for preventing bots from infiltrating web forms or stopping OTP bots.
Arkose Labs for SMS Pumping Fraud
SMS pumping is a serious threat that can cause significant financial damage to businesses through toll fraud. But Arkose Labs is prepared to stop the scourge of SMS traffic pumping.
Arkose Bot Manager’s anti-automation technology identifies and stops the bots that fraudsters use to execute SMS toll fraud attacks. Businesses can insert Arkose Labs at any touchpoint that is protected by one-time passwords in order to detect and challenge fraudulent traffic. In addition, Arkose Labs uses unique in-session authentication that combines real-time risk classification with interactive challenges to reduce reliance on multi-factor authentication methods.
The Arkose $1 million SMS Toll Fraud Warranty is included at no additional cost with the Arkose Bot Manager managed services offering. For more information about Arkose Bot Manager, sign up for a demo today!.











