What is smishing?
Although methodologies may differ, the objective of every cyberattack is to steal consumers’ personally identifiable information (PII), which can then be used for illegitimate financial gain. Smishing, or SMiShing, refers to when an attacker uses text messages or common messaging apps to trick users into sharing their information or downloading malware to their phones.
A smishing text message, often, would also include a link, which when clicked takes the user to a fake website where they are asked to share their personal and financial information, such as name, address, username, passwords, credit card numbers, credit card codes, and banking data among others.
What is smishing phishing?
A smishing attack is a type of phishing attack where mobile phones are used as the attack platforms. There are three main categories of smishing phishing attacks as described below:
- Text phishing: Using compelling text messages, purportedly emanating from a user’s bank, attackers try to lure users into sharing their bank information. They may coax users into clicking a link in the text message to take immediate action on the pretext of a suspicious activity, complete KYC, or confirm a transaction. Alternatively, they may request the user to call the customer service number mentioned in the text message to steal user details.
- Cell phone phishing: In this type of smishing phishing attack, users receive a message with discount offer or upgrade phone message, along with a link to avail of the offer. If the user clicks the link, the website requires them to provide details including credit card number, address, and sometimes even social security number for confirmation.
- Instant messaging phishing: Using smishing messages, with discount offers and deals, sent through social media messengers or WhatsApp, attackers try to gain personal information of the users.
Since most users do not suspect messages on social media messengers and WhatsApp to be fraudulent, they are more likely to respond.
Types of smishing attacks
Smishing attacks are often quite similar. However, attackers adapt their messaging to the latest happenings around the world and disseminate topical messages that users can easily connect with.
Some of the most common types of smishing attacks are as under:
- Public health smishing: Attackers still use the COVID-19 fear to scam people on the pretext of government-aided health programs and contact tracing to elicit information such as social security numbers, credit card details, phone numbers, addresses, names, and so forth.
- Financial services: Created to mimic messages from financial institutions, these messages create an urgency for the user to take action lest their accounts be blocked. At times, financial smishing messages may offer loans or credit cards at deep discounts on the pretext of rewarding the user for being a loyal customer, provided the user avails of the limited-time offer by immediately clicking the link included in the message.
- Free rewards and gifts: These smishing messages exploit the names of reputed retailers to offer free services or products through rewards programs, giveaway contests, and the like to a few selected users. Often, these messages play on the idea of freebies and include time limits to urge users into taking quick action to confirm their names, addresses, email IDs, social security numbers, and at times bank account details to deposit the reward money.
- Order confirmation: Fake invoice details are included in a text message and the user is requested to urgently confirm the order, failing which a certain amount of money may be charged.
- Customer support: Presumably coming from a representative of one of the user’s service providers, customer support smishing attackers try to ‘resolve’ account, billing, or service-related issues by resetting password, confirming or rejecting a recent order, and so forth.
- Account issues: SMS is a popular method most businesses try to communicate with their customers. Attackers exploit this methodology to send smishing messages claiming some issue with user accounts and requesting personal details for resolution.
- MFA codes: For multi factor authentication, codes or OTPs are sent as SMS messages. Attackers design smishing messages to steal these codes by tricking users into sharing these codes on the pretext of identity verification.
Smishing examples
The ubiquitous presence of SMS is powering smishing attacks globally. Attackers use automation to achieve scale and evade detection while abusing the stolen credentials. The number listed in the message usually points to a VoIP service, which makes it difficult to know the true number behind the message.
Attackers exploit the SMS service to disseminate a variety of smishing messages according to the target. Some of the common smishing examples are shared below:
- Freebies: Users receive smishing messages where they are asked to share the details of their bank accounts or credit cards to cover the shipping fee to receive a free product or service.
- Product delivery: Also called FedEx scams, these smishing messages inform users that their shipment was delivered to an incorrect address and direct the users to a website URL to confirm their details or the delivery preference so that the item may be delivered at the correct address.
- IRS message: Attackers send out text messages posing as IRS and asking recipients to call back immediately or face penal action. Once the user calls the specified number, they are tricked into sharing details or funds.
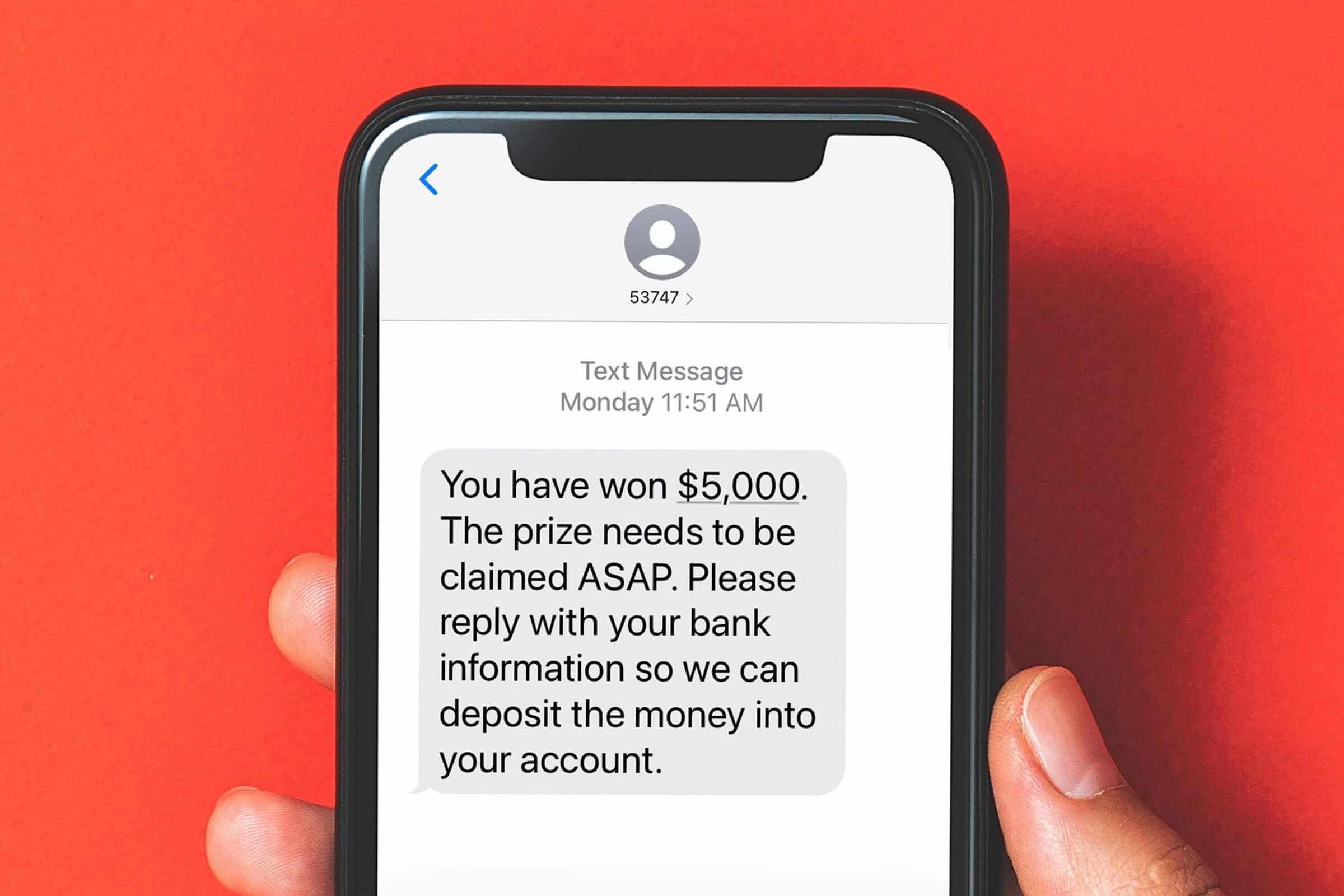
- Rewards: A common smishing attack requests users to reply with their bank account details so that the monetary reward can be deposited directly in their accounts.
- Survey participation: To lure people into making money quickly, some smishing messages ask users to participate in quick surveys.
Why smishing attacks are on the rise
There are several factors powering the rise in smishing attacks. Not only are they easy to execute but also only need users’ phone numbers and messages to trick them into sharing the desired information. Some of the other drivers of smishing attacks include:
- A staggering volume of 23 billion text messages¹ are shared every single day, globally. It is worth noting that 64% of the world’s population² receives or sends a text message every day. This provides attackers with more than enough opportunities to execute smishing attacks.
- Compared to emails, people are more trusting of the messages they receive through SMS or messaging apps and are more likely to reply or take action as requested in the message.
- Getting access to phone numbers is easy as people are less hesitant in sharing their phone numbers on digital channels as well as in person.
- People can send or receive text messages from anywhere in the world.
How smishing attacks are executed
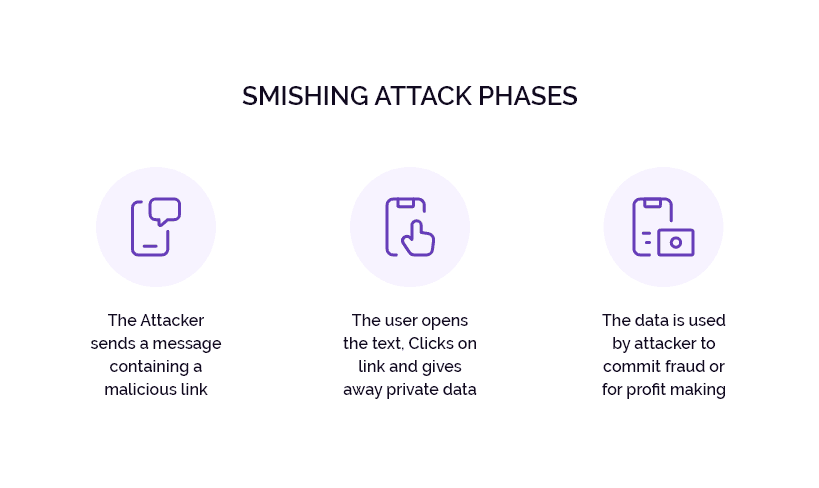
A smishing attack, like a phishing attack, plays on the psyche of the people to induce them into taking a desired action. Over the years, smishing messages have evolved and improved in messaging as well as the language used.
The most common features of a smishing attack are as listed below:
- Context: Attackers use relatable situations to create personalized smishing messages, which appear genuine and help lower user suspicion. For instance, they may create messages that mimic a service provider, such as a bank, telecom operator, favorite brand, and so forth that a user is accustomed to receiving.
- Target: Depending on the objective of the attack, attackers may choose their targets. The most popular method of choosing the target is based on their affiliation to an organization or a location, such as users or employees of a particular organization. As an example, to extort money, attackers may choose to send messages from a bank to its users and employees.
- Social engineering: Attackers exploit the emotions of the victims, such as impersonating a loved one in need of money and requesting financial help through money transfer, to force them into complying with the requests.
- Malware: One of the most common features of smishing attacks is malware that gets downloaded on the victim’s phone and compromises the device such that the attacker gains control of all the information and activities on the phone.
- Malicious attachments: An accompanying picture, video, or a document may well be a virus, adware, spyware, trojan, or ransomware, sent with the intention of compromising the user device and exploiting the victim for financial gain.
- Malicious links: Too often, smishing messages feature malicious links that redirect users to fake websites where they are tricked into sharing personal and financial data.
- Grammatical errors: A distinguishing feature of smishing messages is that they usually have spelling and grammatical errors.
- Deception: The most important feature of smishing text messages is deception, which often forces users to trust the sender and comply with the request.
How to identify a smishing attack
Smishing attacks are complex and often go unreported. To protect themselves, it is essential that victims know what is a smishing attack and take adequate protective measures. Further, they must look out for signals that may indicate smishing attempts.
Here are a few ways to identify a smishing attack:
- Use of a shorter number, comprising only a few digits, to send a message.
- Attempt to target information stored on the smartphone.
- Messages that create a sense of urgency to respond.
- Exclusion of the domain name of the company from the URL shared in the message.
How to prevent a smishing attack?
Smishing attacks play on the emotions of the users. They succeed in tricking people into responding to the messages the way attackers want them to by creating a sense of urgency. There are certain techniques that can be deployed to identify and stop smishing attacks.
Some of them are listed here:
- Verify identity: Check the phone number to confirm whether the number really belongs to the organizations the text message seems to have been sent from.
- Use MFA: Multi-factor authentication creates a hurdle in the way of attackers trying to log in to user attacks with stolen credentials.
- Use anti-malware solutions: They flag suspicious links and protect from malware.
- Work with a vendor: Choose a reliable vendor, like Arkose Labs, to identify and stop smishing attacks before they can cause any damage.
Prevent smishing attacks with Arkose Labs
Arkose Labs focuses on helping digital businesses fight a myriad of cyber threats while keeping interests of genuine consumers at the forefront. Using an unconventional approach, Arkose Labs fights automated smishing attacks with great precision and delivers long-term protection.
Arkose Labs uses a challenge-response authentication mechanism to assess the authenticity of users. Arkose Matchkey challenges are not only resilient to automatic solvers, causing bots, non-human traffic, and other off-the-shelf solvers to fail, but also feature a large repository of variations of the same challenge that requires attackers to spend immense amounts of efforts to clear the challenges at scale. This disrupts the economics of the attack, erodes the profits and forces attackers to abandon the attack and give up for good, thereby ensuring long-term fraud prevention.
Arkose Labs combines advanced detection technologies, real-time risk scoring, and behavioral biometrics to identify and block fraudulent activities across various digital channels. It successfully differentiates between legitimate users and malicious click-farms, including those involved in smishing campaigns, by analyzing patterns and behaviors in real-time.
Further, Arkose Labs helps organizations reduce the impact of smishing and other evolving threats by providing actionable intelligence, raw data and signals, complete with 24x7 support that helps security teams to thwart growing threats, while ensuring a great user experience for genuine consumers.
