With the advancement in technology, hackers have developed ways to stealthily access your website and conduct malicious activities through bots. These automated bot attacks are a threat to the security and stability of any enterprise and its digital touchpoints, including customer login flows. As such, it is crucial to understand how to defend against them.
How are bots used for attacks?
Bot attacks are a real threat to an enterprise's websites and applications. The attacks are usually automated and can vary in frequency and length and can be used to manipulate, cause data breaches, or disrupt a web application. These attacks, unfortunately, are becoming the norm against businesses and enterprises of all sizes.
Bots are automated programs that can be used for fraudulent activities or disrupting networks. For instance, malicious bots can be used to distribute malware, steal personal information and credentials, generate fake traffic, spam comments, and even launch attacks on competitors. Large-scale bot attacks can also be carried out using botnets to execute DDoS, phishing, brute force, and other attacks.
Types of bot attacks
Bot attacks continue to evolve in sophistication and have become advanced enough to mimic human interactions while causing harm to online systems. Bots are versatile and can perform various malicious activities under the control of cybercriminal bot herders who consistently evolve their tactics. For instance, bots can be created to scrape data from websites or post comment spam, irritating website owners and damaging the experience for legitimate users and consumers.
There are many types of bot attacks, which often include phishing attacks and sending spam, but bots can also automate other processes related to fraud, like account takeovers or credential stuffing. Botnets can send spam emails, engage in click fraud campaigns, generate malicious traffic for denial of service attacks, and steal personal data or business-sensitive information at scale. One of the most common forms of DDoS attacks today is volumetric attacks using botnets, which overwhelm the victim's network or server with traffic and cause downtime.
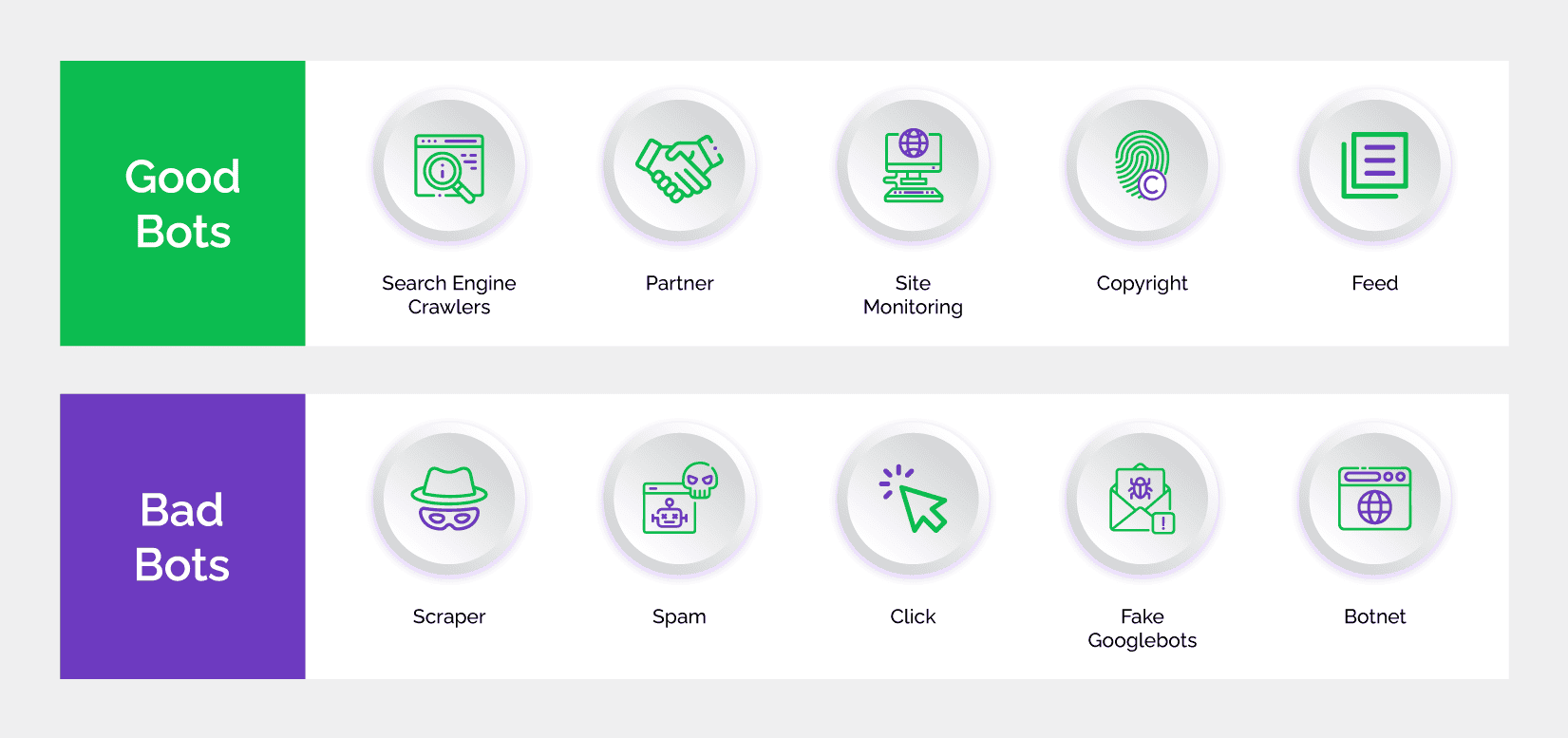
What are signs of a bot attack?
One of the most obvious signs of a bot or botnet attack is abnormally high page views, bounce rate, and session duration. Bots often lead to anomalies and high web traffic, consuming server bandwidth, and affecting the performance of websites. All of which can hurt an enterprise’s revenue, manipulate website metrics, and even damage an enterprise’s reputation.
How do you detect and defend a bot attack?
Protecting against bot attacks requires understanding the ways in which bots operate and implementing measures to detect and block them in real time. Bot attacks can be difficult to detect and security teams may not be aware that they are under attack until it is already too late.
To detect a bot attack, behavioral analysis and browser fingerprinting can be used to analyze unique user features and distinguish between humans and bots. A bot mitigation solution can also trigger enforcement actions such as multi-factor authentication (MFA) to prevent further bot attacks.
Defending against bot attacks requires a comprehensive approach that encompasses multiple strategies and tactics for effective protection against these malicious attacks.To prevent bot attacks, businesses can use automated tools that can identify and block bot traffic. Alternatively, web admins can implement CAPTCHA software, which forces visitors to prove they are human, making it harder for bots to navigate through the website.
What is bot management?
To manage bot traffic, various tools and strategies can be employed by organizations to protect their websites from harmful attacks. One such strategy is implementing bot management systems that use machine learning or AI to detect and prevent malicious bot traffic. In addition, regular security audits and updates can also protect against potential bot attacks. It is crucial to deploy security measures constantly to protect against any potential cyberattacks.
Bot management enables businesses to detect bot activity, identify its source and stop malicious bots while allowing good bots (such as search engine crawlers) to access their websites and apps. Software solutions that allow the mitigation of business risks emanating from bot-driven attacks are a key component of this strategy. Bot management is useful in fighting automated attacks such as credential stuffing, account takeover, new account fraud, scraping, scalping, and more.
Over the years, a number of bot management solutions have been developed to help digital businesses filter out malicious bots. These solutions make use of multiple technologies including machine learning, artificial intelligence, and website development technologies.
How bot management works
Bot management solutions monitor the incoming digital traffic on a website, app, or an API to detect and block malicious activity. These solutions are a combination of several tools and technologies that help businesses to distinguish between malicious bots and good users. These include artificial intelligence, machine learning, data analytics, behavioral biometrics, device fingerprinting, and a host of other techniques.
Bot management solutions currently follow three approaches to identify and stop bot-driven attacks:
- static
- challenge-based
- behavioral
Depending on the level of threat they face, digital businesses use one or a combination of these approaches. They can also outsource bot management services to trusted vendors, like Arkose Labs, that specialize in this area.
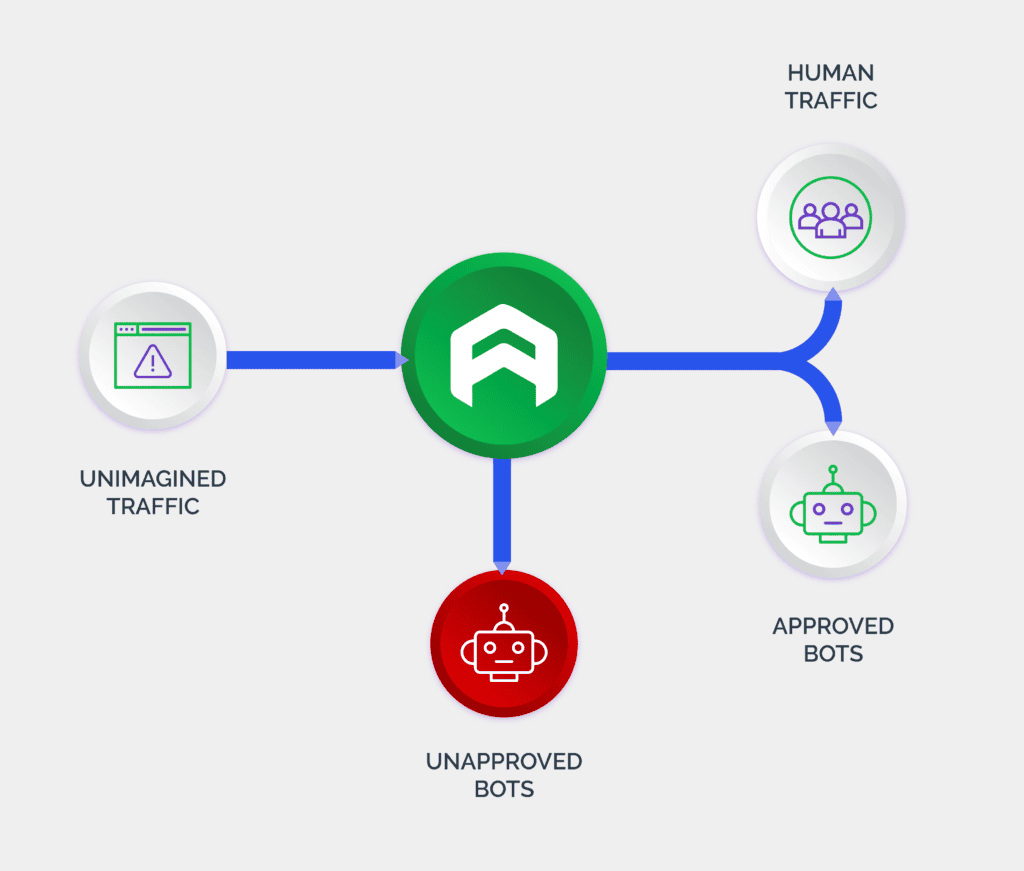
Arkose Labs stops bot attacks in their tracks
Bot management solutions have an important role to play in the fight against automated attacks. However, blocking users on a slight suspicion or lowering the guards for the purpose of customer acquisition can be counterproductive. Extremely stringent authentication can introduce unnecessary friction, like legacy CAPTCHA technology or geofencing, and cause consumer discontent. Whereas, lenient authentication can open the gates for attackers to rush in.
To make matters worse for digital businesses, bot management solutions such as CAPTCHAs have lost their supremacy over bots. While bots have become sophisticated using advanced technologies, CAPTCHAs have not been able to evolve at the same pace. This has resulted in CAPTCHAs being cleared by even some of the basic bots.
Arkose Labs accurately distinguishes between human and automated traffic to neutralize automated spam attacks before they can scale. Using a combination of dynamic risk decisioning and targeted friction, through Arkose MatchKey challenges, Arkose Labs makes the attack incrementally more costly for fraudsters, which prevents them from scaling up their operations.
The Arkose Labs solution is so effective at rooting out automated attacks that it is backed by an SLA guarantee. This provides commercial assurance that it will defeat bots attacks within a set timeframe, protecting your users from phishing scams, malicious messages and other forms of abuse.
For more information on how Arkose Labs can partner with your enterprise to stop bot attacks, be sure to book a meeting with us today.







