Securing Your Site: Web Application Firewall 101
Security is a major concern for businesses and organizations when it comes to web applications. With increasing cyberattacks and data breaches, it's important to safeguard web applications from potential threats. In this article, we're going to discuss what a WAF (Web Application Firewall) is, how it works, and why it's important for all businesses to consider using one.
What is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) is a security tool that scrutinizes incoming traffic to an app or site. It identifies and blocks malicious traffic patterns while enabling legitimate traffic. It helps protect against common cyberattacks such as XSS, SQL injection, and DDoS attacks. Implementing a WAF can improve your website's security posture.
Why Use a WAF for Internet Security?
The primary purpose of a WAF is to protect web apps from attacks that may exploit vulnerabilities in the application and compromise sensitive data. Unlike network firewalls, which protect network traffic, WAFs protect the application layer, where HTTP requests and responses are transmitted. A web application firewall provides visibility into the traffic flowing through the network. It analyzes requests and responses, looking for patterns that might indicate an attack attempt. If such a pattern is detected, the firewall will take action to block the request, thus preventing attacks such as cross-site scripting (XSS), SQL injection, and other HTTP vulnerabilities. Acting as a reverse proxy server, WAFs monitor and filter web traffic between servers and clients while enforcing security rules for data packets.
Furthermore, WAFs can provide visibility into API traffic, allowing security teams to monitor and analyze the behavior and usage of APIs. This visibility enables organizations to identify unusual or suspicious API activities, detect API abuse or misuse, and respond promptly to security incidents.
While WAFs primarily focus on securing web applications, they can also provide protection for other network services. For example, some WAF solutions offer email filtering capabilities, allowing organizations to prevent the delivery of malicious emails and block phishing attempts. Similarly, WAFs can be configured to provide DNS filtering, which helps in preventing domain-based attacks and blocking access to malicious websites.
How WAFs Work
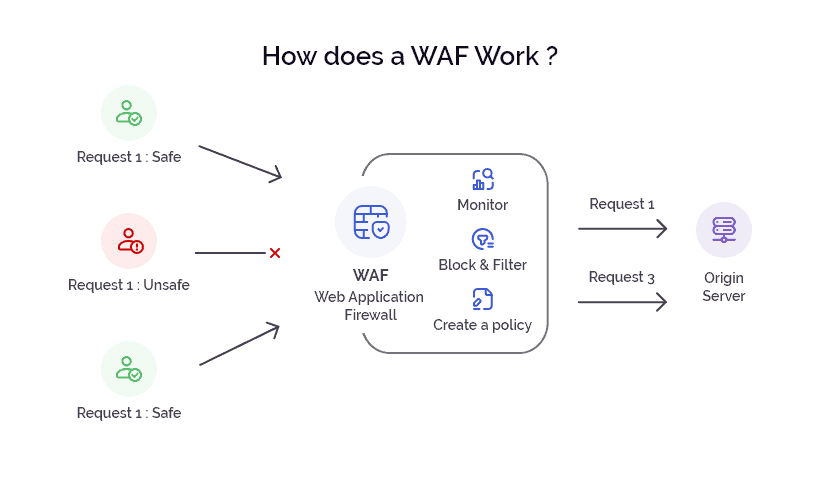
WAFs leverage OWASP's (open web application security project) knowledge to defend web applications against common attacks by acting as an intrusion prevention system (IPS). When the WAF receives an HTTP request, it compares it to a set of predetermined rules intended to spot known attacks. If a rule matches the request, the WAF will block it and reject the connection. The WAF can also perform additional checks, such as blocking requests that are malformed or outside the normal range of values. This gateway functionality allows WAFs to provide real-time protection against attacks without requiring changes to the underlying application code.
A fundamental concept utilized by WAFs is the positive security model. Instead of solely relying on a blacklist of known attack patterns, WAFs adopt a proactive approach by defining a set of rules that explicitly allow only valid and expected traffic. This positive security model helps prevent false positives and provides a more accurate and effective means of protecting web applications.
Key Features of WAFs
Web application firewalls come with many features that can help safeguard a web application. Some of the key features of WAFs include:
- Malware detection: WAFs can detect and block malware that may be embedded in web pages or files.
- Access control rules: WAFs can enforce access control policies, such as blocking traffic from specific IP addresses or countries.
- Real-time traffic monitoring: WAFs can monitor traffic in real-time, allowing for quick detection and response to attacks.
- Integration with other security solutions: WAFs can be integrated with other security solutions, such as intrusion detection systems, content delivery networks (CDN), and security information and event management (SIEM) systems.
- Detailed logging and reporting: WAFs can log and report on all traffic that passes through them, providing valuable insight into potential threats and attack patterns.
- Customizable policies and rules: WAFs allow administrators to create custom policies and rules to meet the specific needs of their web application.
Types of WAFs: A Comparison
A WAF may be a physical or virtual appliance. The different types include network-based, host-based, cloud-based, open-source, and hybrid. Open-source WAFs allow for customization but may require technical expertise. Hybrid WAFs are a combination of two or more approaches for added protection.
Network-based WAFs
Network-based WAFs are deployed within a network, usually at the perimeter, to protect all web applications that are hosted within the network. These WAFs monitor all traffic that passes through the network and can intercept any malicious traffic before it reaches the web application. Network-based WAFs are particularly effective at improving security across larger networks that host many applications. However, they can be complex to deploy and manage, and may require specialized hardware or software. They can also introduce latency into the network, which can impact application performance.
Host-based WAFs
Host-based WAFs are installed on the host machine and provide protection for a specific web application. Host-based WAFs are ideal for organizations that have a small number of web applications or require customized security policies for each application. Host-based WAFs are generally easier to deploy and ideal for smaller businesses. However, host-based WAFs can be resource-intensive and may impact application performance. They may also require additional maintenance and management compared to network-based WAFs.
Cloud-based WAFs
Cloud-based WAFs are a type of network-based WAF that is hosted in the cloud. Cloud-based WAFs are scalable, cost-effective, and require minimal maintenance. This makes them an ideal solution for businesses of all sizes that host web applications in the cloud.
One of the main advantages of cloud-based WAFs is their ability to provide a low-maintenance security solution for web applications hosted in the cloud. Cloud-based WAFs can be deployed quickly and easily, and can be scaled up or down as required. They can also be integrated with other cloud-based security solutions like DDoS protection and bot mitigation. However, cloud-based WAFs may not provide the same level of customization as host-based WAFs, and may be subject to limitations imposed by the cloud hosting provider. They may also introduce additional latency into the network, which can impact application performance.
Benefits of Using a WAF
WAFs provide improved security, compliance with industry standards, protection against DDoS attacks, and enhanced performance.
Improved Security
The biggest benefit of using a WAF is improved security. With a WAF in place, web applications are protected from a wide range of threats, including network and application layer attacks. By detecting and blocking these types of attacks, WAFs help prevent unauthorized access to sensitive data and protect against financial losses.
Compliance with Industry Standards
In many industries, such as healthcare and finance, it's essential to comply with regulatory requirements that mandate specific security measures. Using a WAF can help meet these requirements and demonstrate that your web application is secure and compliant with industry standards.
For example, the Payment Card Industry Data Security Standard (PCI DSS) requires merchants to protect cardholder data by implementing a firewall. A WAF can help meet this requirement by providing an additional layer of protection against cyberattacks.
Protection Against DDoS Attacks
A distributed denial of service (DDoS) attack is a common form of attack that aims to overwhelm web applications with traffic. DDoS attacks can significantly impact business operations and cause massive financial losses. WAFs can mitigate the effects of DDoS attacks by blocking malicious traffic and distributing legitimate traffic across multiple servers.
WAFs can also detect and block botnet attacks, which are a common method used to launch DDoS attacks. By blocking these types of attacks, WAFs can help ensure that web applications remain available and accessible to legitimate users.
Enhanced Performance and Scalability
Web applications protected by WAFs often see improved performance and scalability because WAFs can cache frequently accessed content, filter out unwanted traffic, and prevent malicious requests from consuming server resources. By reducing the load on servers, web applications can run more smoothly and reliably, even during periods of high traffic.
Choosing the Right WAF for your Business
Web application firewalls are an essential part of any business that operates online. To choose the right one, you'll need to do the following:
Assess Your Security Needs
The first step in choosing a WAF is assessing your security needs. This involves taking into account the size of your organization, the number of web applications you have, the type of data you store, and any compliance requirements you must meet.
Evaluate WAF Vendors
When evaluating vendors, consider factors such as the level of support they offer, the cost of the solution, and the ease of deployment and maintenance. Some vendors offer 24/7 support, while others may only offer support during business hours. Some vendors may have a higher upfront cost but lower maintenance costs, while others may have a lower upfront cost but higher maintenance costs.
Consider Costs and Maintenance
Costs can vary depending on the size of your organization, the level of support you require, and the complexity of the web applications you want to protect. Some vendors may charge a flat fee for their solution, while others may charge based on the number of web applications you want to protect. Maintenance costs can also vary depending on the level of support you require and the complexity of your web applications.
Using a WAF with a Bot Mitigation Platform
Using a Web Application Firewall (WAF) alongside a bot mitigation platform can provide an effective defense against both traditional and automated bot attacks. Here's how you can combine these two technologies:
- Understand the capabilities of each solution: Familiarize yourself with the features and functionalities of your chosen WAF and bot mitigation platform. This will help you identify any potential overlap or compatibility issues.
- Implement the WAF: Set up the WAF to protect your web application against common security threats and known vulnerabilities. Configure the WAF rules based on best practices and the specific requirements of your application.
- Integrate the bot mitigation platform: Arkose Labs is a bot mitigation platform that complements your WAF. The bot mitigation platform should provide advanced detection and mitigation capabilities specifically designed to handle automated bot traffic.
- Configure the bot mitigation platform: This may involve DNS configuration changes to route traffic through the platform's infrastructure or setting up a reverse proxy. Configure the platform's settings to specify the desired bot detection and mitigation policies.
- Fine-tune rules and policies: This may involve adjusting thresholds, whitelisting specific IPs or user agents, or creating custom rules to handle specific bot patterns.
- Monitor and analyze traffic: Regularly monitor the traffic patterns and security alerts provided by both the WAF and the bot mitigation platform. Analyze the logs and reports to identify potential threats or anomalies. Continuously refine the rules and policies based on the observed traffic patterns.
- Collaborate with the bot mitigation provider: Maintain an ongoing relationship with your bot mitigation platform provider. Engage with their support team to address any emerging threats or challenges specific to bot mitigation. Arkose Labs provides 24/7 SOC threat analysis and tuning.
- Periodically assess and update: Conduct periodic assessments of your WAF and bot mitigation platform configurations to ensure they remain effective. Keep the solutions updated with the latest patches and releases to benefit from new features and enhancements.
If you'd like to learn more about how Arkose Bot Manager can work with your WAF, book a demo today!

