What is anti-spoofing?
The measures taken to prevent unauthorized use of stolen consumer and business information to protect users and systems from being manipulated is called anti-spoofing. Anti-spoofing measures help identify genuine users through identity proofing to ensure the authenticity and integrity of data, and account security of consumers.
What is spoofing?
Impersonating a communication to make it appear emanating from a genuine source, and extract illegitimate gain, is called spoofing. Bad actors may resort to spoofing emails, phone calls, websites, IP addresses, or Domain Name System (DNS) servers.
The common types of spoofing include IP spoofing, where an attacker changes the source address of an IP packet to circumvent security measures and gain access to a business network. Email spoofing uses fraudulent emails for phishing attacks to trick users into divulging sensitive information that can be used for several criminal activities. In caller ID spoofing, attackers forge the information displayed on a user’s caller ID to impersonate a trusted caller, whereas in DNS spoofing, DNS responses are manipulated to redirect users to malicious websites. Further, attackers use website spoofing to clone websites and cheat users, and spoof user identities to impersonate genuine users.
Anti-spoofing is critical for improved network resilience
Anti-spoofing is important for overall security of an organization as it helps maintain integrity and availability of data and the systems. By unearthing fraudulent activities, it prevents unauthorized access to resources and user accounts, thereby improving users’ privacy.
Bad actors generally use spoofing to bypass security measures and gain unauthorized access to business networks. They may also use spoofing as a means to overwhelm business systems and disrupt their operations. Anti-spoofing measures enable businesses to improve network resilience and protect their network infrastructure from attempted abuse.
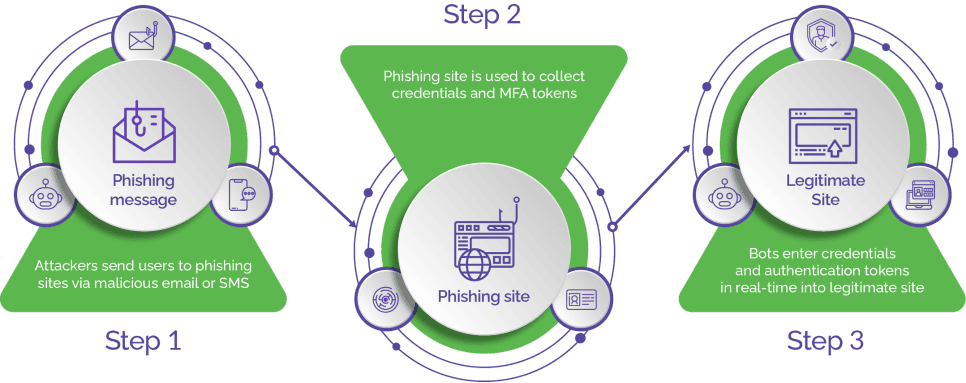
Attackers often use phishing attacks to impersonate trusted business entities to dupe users into sharing their personal or sensitive information, which is then used for payment fraud through illegitimate digital transactions and several types of other attacks. With anti-spoofing techniques, businesses can uncover impersonation or phishing attempts and prevent attackers from stealing sensitive information. By authenticating users, anti-spoofing measures help businesses minimize the chances of identity theft, prevent data tampering, ensure integrity of data, and protect users’ account security.
Greater user security helps businesses foster customer trust and maintain a positive market reputation. It also helps businesses remain compliant with several prevailing regulations related to data security and privacy.
Popular anti-spoofing techniques
To effectively combat the threat of spoofing, it is important that a combination of anti-spoofing techniques is implemented. However, the combination of anti-spoofing techniques used must be tailored to meet the specific requirements of the business systems.
The commonly used anti-spoofing techniques include implementation of filtering mechanisms to prevent IP spoofing, email authentication, caller ID authentication, two-factor authentication (2FA), multi factor authentication (MFA), encryption, certificate-based authentication, and intrusion detection systems and prevention systems.
How anti-spoofing techniques work
Anti-spoofing techniques often combine multiple methods for improved protection. These methods vary according to the unique requirements of a business such as the potential attack vectors or the level of security needed.
Anti-spoofing methods are implemented in a layered approach to help identify and stop spoofing attempts early in their tracks. Some of the common methods that may form part of an overall anti-spoofing strategy are as listed below:
- Source Address Validation: The source address of incoming IP packets is validated using packet filtering or ingress filtering. Network routers and firewalls verify that the source IP address matches a legitimate range of addresses for that network segment. The packets that are detected as spoofed source addresses are rejected.
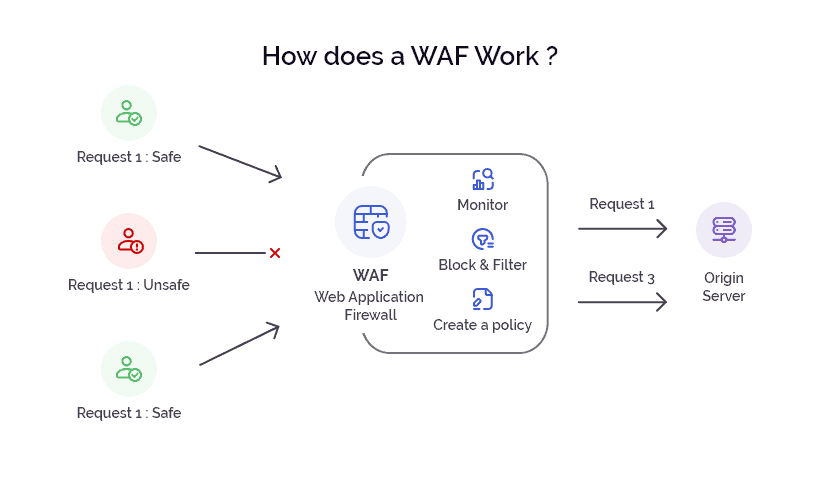
- Authentication and Verification: Authentication protocols and mechanisms such as SPF, DKIM, and DMARC are used to authenticate the sender's domain and verify the integrity of the email content. Similarly, protocols like STIR/SHAKEN help authenticate caller ID information on telecom networks to authenticate the identity of the entities involved.
- Two-Factor and Multi-Factor Authentication: 2FA and MFA add an extra layer of authentication by requiring users to provide an additional authentication factor, such as OTP, code, or biometric verification, apart from usernames and passwords.
- Encryption and Secure Protocols: Implementing SSL/TLS encryption and using secure communication protocols ensures only authorized users can access the data. This helps protect against data interception, manipulation, and spoofing during transmission.
- Intrusion Detection and Prevention Systems: IDS and IPS solutions monitor the incoming network traffic for suspicious patterns or anomalies, indicative of a possible spoofing attempt. Using techniques such as signature-based detection, anomaly detection, and behavior analysis, these solutions help identify spoofing attempts and make timely intervention.
- Ongoing Monitoring: Identify the telltales of a spoofing attack through continuous monitoring and auditing of network traffic, system logs, and user activities.
Areas where anti-spoofing is applicable
Bad actors engage in several types of spoofing activities. Therefore, anti-spoofing measures have a wide area of applicability and can be used to thwart different types of spoofing attacks.
However, specific application of anti-spoofing measures, often, depends on the context and the potential risks associated with spoofing in a particular domain or system. The most common areas where anti-spoofing is applicable include network security, email security, caller ID protection, web security, mobile device security, access control and authentication, IoT security, and physical security.
Arkose Labs delivers long-term protection from spoofing attempts
As a leader in identity and access management, Arkose Labs adopts an innovative approach to deter attackers by making it difficult for them to complete the attacks quickly or achieve scale. Using a combination of bot manager, device intelligence, email intelligence, behavioral biometrics and a host of other digital parameters, Arkose Labs accurately identifies synthetic identities and malicious users from incoming traffic and uses targeted friction to foil any spoofing attempts.
Automated traffic bots and scripts instantly fail when presented with the most resilient CAPTCHA ever, the Arkose Matchkey challenges. Persistent human attackers are required to invest disproportionate amounts of time, effort, and resources to try and automate solving Arkose Matchkey challenges at scale. In the process, the execution of the attack gets delayed and rising investments erode any returns from the attack. This forces attackers to abandon the attack and move on for good to unprotected targets.
Arkose Labs offers customer-centric protection from spoofing that enables businesses to maintain great user experience and undisrupted business operations. With 24x7 support and data-backed actionable insights, Arkose Labs empowers businesses to adapt to the evolving spoofing tactics, and partners in their success.
