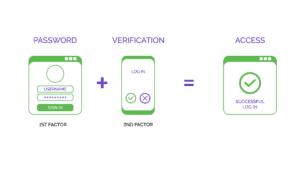
What is Identity Proofing?
Identity Proofing is the process of matching the claimed identity of a digital user with the actual identity, using elements such as credit reports or biometrics. It helps businesses to confirm that the users are indeed who they say they are. Identity proofing is a common protocol followed by a company before issuing an account and login credentials to a user.
Identity proofing also provides businesses with an interactive method for face-to-face, telephonic or web authentication. For instance, providing a valid document to verify identity before checking into a hotel. In an increasingly digital world, identity proofing can be an especially useful authentication method for risky transactions such as fund transfer or accessing sensitive information.
How Identity Proofing Works
Companies can use manual verification, which requires users to provide valid identity documents whether in-person or through video conferencing. However, manual reviews are not only time-consuming, they also need a lot of human effort and are prone to human errors. For large businesses that handle thousands of customers every day, manual identity proofing is unscalable. Besides, it can also degrade user experience by delaying the fulfillment of user requests.
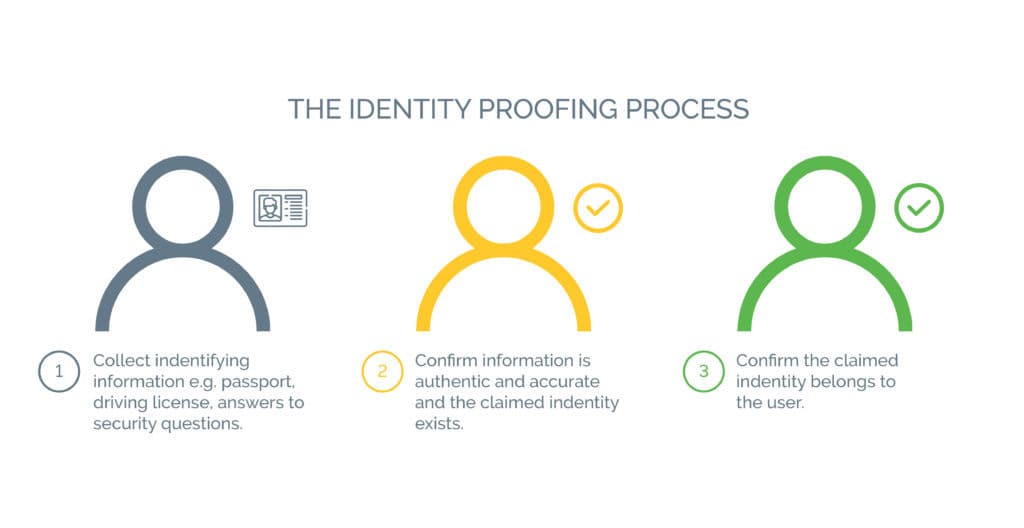
With automatic identity proofing – where companies can complete the verification process without human intervention – enables them to authenticate users in real-time and preserve the user experience. According to the Digital Identity Guidelines prescribed by the National Institute of Standards and Technology, there are three key steps to identity proofing: These include:
- Resolution: It refers to determining a user’s identity in the right context.
- Validation: The second step is that of gathering the user’s personally identifiable information and confirming its accuracy.
- Verification: Finally, verifying the user as who they claim to be.
Automatic identity proofing solutions perform the aforementioned steps in real-time for a secured authentication process that does not disrupt the user experience. Therefore, in today’s digital-first economy, automated identity proofing is the way forward.
Importance of Identity Proofing
Over the years, the number and frequency of incidents of data breach have only increased. This means the risk of exposure for an average business has increased manifold. An average company experienced 22 data breaches a year in 2020. These incidents of data pilferage provide attackers with volumes of personal information, which further fuels identity fraud.
On an average it takes about six months to detect a data breach, which allows attackers a significant amount of time to manipulate the data. Theft of critical business information, compromised user accounts, and non-compliance to prevailing regulations cause serious financial and reputational losses to businesses.
In the wake of these risks, identity proofing assumes a critical role in protecting the business ecosystem and preserving consumers’ account security.
Current Identity Proofing Approaches and Their Limitations
At a time when fraud levels are at a record high, digital businesses need effective security measures to safeguard business and consumer interests. Businesses are using several identity proofing methods that have their own limitations. Some of these include:
-
Multi-Factor Authentication:
An additional layer of security above the password-based authentication, MFA makes use of a verification element which the user is, knows, or possesses. These may include a one-time password (OTP) sent via SMS, answering a security question, verification through an automated, among others. MFA is often expensive and adds an extra step that may cause discomfort to the user. Furthermore, fraudsters can steal SMS based authentication code or divert automated calls for spurious verification.
-
Password Reset:
This requires users to change their passwords at regular intervals and defines the length and complexity for creating a new password. Creating unique passwords is a chore for most users who tend to reuse or recycle their passwords across digital accounts. This can expose all digital accounts to account takeover attempts should a username-password combination be validated through credential stuffing or password spraying.
-
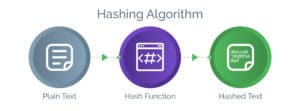
One-way hashing:
In this method the users’ passwords are encrypted using customizable hashing salt. Since it is one-way hashing, the passwords are only encrypted and cannot be decrypted. Consumers can choose any hashing salt for their password, which effectively allows anyone to access these passwords.
-
Access control:
To restrict access to data, emails from specific domains can be blocked or allowed. User accounts with suspicious activity can be blocked. In either case, user experience can get disrupted as due to evolving consumer behavior and manipulated identities attackers can impersonate good users while good users may be misread as fraudsters. This can lead to false positives and affect revenues.
-
CAPTCHA:
Designed to stop bots and automated attacks from accessing the business network, CAPTCHAs have failed to keep pace with the advancement in bot technology. This has rendered them nearly ineffective in bot detection. Instead, they only add friction to good users, degrading their digital interaction.
Identity Proofing with Arkose Labs
It is no exaggeration to state that we are all dependent on digital channels for everyday activities. As the volume of digital interaction with websites and apps continues to grow, the susceptibility of businesses to evolving cyber threats is only rising. It is, therefore, critical that digital businesses acquire capabilities to effectively tell fraudsters from good users; and prevent attackers from causing fraud losses – both direct and indirect.
Today, businesses need identity proofing solutions that can pinpoint bad actors with accuracy so as to allow good users to continue enjoying their digital journeys without any disruption. With growing digital traffic, businesses need identity proofing solutions that allow users to self-verify their identities. Arkose Labs uses real-time risk assessment and combines it with targeted friction in the form of enforcement challenges to help businesses accurately identify attackers from good users, while maintaining superior user experience.