The business impact of credential harvesting can be severe, as it puts an organization’s entire network and sensitive data at risk. In this blog, we will dive into what credential harvesting is, how it impacts an organization, and how to prevent these attacks.
What is credential harvesting?
Credential harvesting is the process by which cybercriminals collect millions of stolen user credentials — the username and password combinations used by authorized users to access protected systems and data. These stolen credentials are sold in bulk on the dark web and may then be used to launch further credential stuffing attacks.
Email phishing is the most successful method of credential harvesting. In 2020, 75% of organizations worldwide experienced a phishing attack, and 96% of credential harvesting attacks arrived via email1. Malware, man-in-the-middle (MITM) attacks, social engineering attacks, and insider threats are also used for credential harvesting.
When an employee falls victim to a phishing attack, threat actors gain initial access to the employee's personal data and credentials. The stolen information then may be used to impersonate them or to initiate future data breaches against the organization. Once attackers have the stolen login credentials, they can easily gain access to more systems, harvesting massive amounts of credentials and sensitive data.
The rise of credential harvesting
Credential harvesting is on the rise and has become increasingly alarming in recent years. Phishing attacks and social engineering rely on user behavior. Unsuspecting victims provide credentials or other confidential information that becomes part of the credential harvesting attack.
According to IBM’s Cost of a Data Breach 2022 Report, the most common initial cyberattack vector in 2022 was stolen or compromised credentials, responsible for 19% of all breaches2. This attack vector also had the longest mean time to identify and contain the breach, at 327 days3.
The Verizon 2022 Data Breach Investigations Report (DBIR) reports that the top two types of data breached in 2022 were credentials and personal data4:
“Credentials are the favorite data type of criminal actors because they are so useful for masquerading as legitimate users on the system.”5
Top confidentiality data varieties over time in breaches
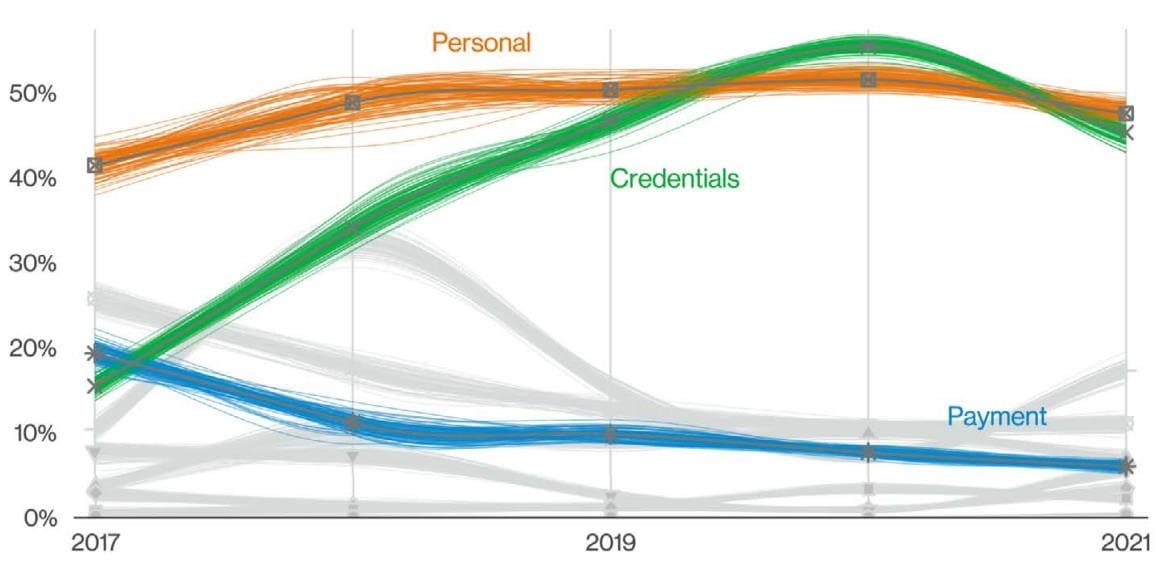
Credential harvesting attacks target multiple industries, including finance, healthcare, and retail, and have the potential to cause significant long-term damage. It's important for businesses to take this threat seriously and implement proper security measures to protect their sensitive information.
The business impact of credential harvesting attacks
Credential harvesting can cause massive damage to an organization when cybercriminals collect thousands of stolen usernames and passwords. These types of data breaches have several consequences, such as financial losses, lost business, and damage to the organization's reputation.
According to IBM’s Cost of a Data Breach Report 2022, breaches caused by stolen or compromised credentials had an average cost of USD 4.50 million. These breaches also had the longest lifecycle — 243 days to identify the breach, and another 84 days to contain the breach.
Perhaps worst of all, credential harvesting attacks can exploit cybersecurity vulnerabilities in an organization’s IT infrastructure, giving attackers wide access to sensitive systems and data, and putting the organization's entire network at risk.
How to prevent credential harvesting attacks
Fortunately, there are effective ways to prevent these attacks. One strategy is to provide employee user education, such as anti-phishing training, and to enforce multi-factor authentication. This can block most attacks, but it can be made more powerful by using machine learning to detect and enforce risk-based access control.
Implementing application security best practices is also essential. By fortifying email systems, you can reduce the risk of phishing attacks. Awareness initiatives and behavioral training can also go a long way in helping individuals understand the risks and how to avoid them.
An insider threat program can help to identify insider threats, address the problems they cause, and raise awareness of insider threats in an organization. By being proactive and taking these steps, individuals and companies can greatly reduce the risk of these dangerous attacks.
The best way to prevent credential harvesting attacks is actually to prevent phishing attacks with a robust bot management solution. Arkose Labs protects against advanced bots, thwarting the automated scripts that use phished credentials by embedding a token in the legitimate web application. Each request dynamically verifies that the token passed from the client to the server, causing sessions originating from a phishing website to fail.
In fact, Arkose Labs is the first and only bot management solution to provide a warranty against credential stuffing attacks. Our $1 Million Credential Stuffing Warranty protects businesses from the multi-faceted costs that result from hacked accounts.
Conclusion
Credential theft has become increasingly sophisticated, making it difficult to detect and respond to. Cybercriminals use these attacks to steal sensitive information, including usernames, passwords, credit card numbers, and other confidential data. Companies need to take proactive measures to identify and prevent credential harvesting attacks, such as deploying a bot management solution, training employees on safe browsing practices, implementing multi-factor authentication, and regularly reviewing access credentials.
If you'd like to learn more about how to stop the phishing attacks that lead to credential harvesting, book a demo now!
- Credential Harvesting Attacks Can Threaten Your Networks
- A Cost Of A Data Breach 2022: A Million-Dollar Race To Detect And Respond
- A Cost Of A Data Breach 2022: A Million-Dollar Race To Detect And Respond
- 2022 Data Breach Investigations Report
- 2022 Data Breach Investigations Report
- 2022 Data Breach Investigations Report







