What is inventory fraud?
Inventory fraud, also known as inventory hoarding or denial of inventory, refers to adding too many items, particularly expensive and limited-edition items, to a shopping cart without completing the purchase. Inventory fraud attacks include booking hotel rooms, flight tickets, or in the most recent inventory fraud cases of online shopping during peak shopping seasons such as Black Friday, Cyber Monday, or Christmas. The aim of inventory fraud is to prevent genuine customers from accessing these items and causing an artificial increase in their prices.
Attackers use different types of bots and other automated tools to execute denial of inventory attacks. These bots quickly hoard specific items, which undermines fair market dynamics and contributes to price inflation. This, in turn, degrades user experience and contributes to consumer discontent, which can be detrimental to business reputation and revenue potential.
Types of inventory fraud
Inventory fraud is most widespread in the eCommerce, travel, and ticketing industries. Attackers resort to automated bot attacks to quickly score deals, use scalper bots to scalp in-demand items, and add them thousands of times to the shopping carts, much before genuine users can even access them.
The common types of inventory fraud in prevalence are as listed below:
- Retail Arbitrage: In this type of fraud, attackers use bots to automate deal-scoring at scale to later resell these items at a premium. As a result, legitimate consumers are deprived of finding discounts or deals, which can lead to consumer discontent.
- Reduction in Inventory: Attackers use bots to purchase a large quantity of specific items meant for a wider section of consumers.
- Denial of Inventory: In a denial of inventory attack, otherwise known as inventory hoarding, bad actors use specialized bots to hoard several in-demand, exquisite, or limited-edition items, which prevents genuine users from buying them. They program cart abandonments in such a way that facilitates them to quickly buy the freed items.
Inventory fraud negatively impacts businesses
Inventory fraud scandals can have a significant negative impact on businesses, which can result in loss of customers and brand reputation. It affects market dynamics, limits consumers’ choices, causes revenue losses to businesses, and erodes customer trust.
It is safe to say that inventory fraud cases cause colossal damage to an affected business, much more than even lost merchandise. This is because not only do bad actors prevent genuine customers from accessing the items in the inventory, but large-scale bot attacks can also overwhelm business networks and crash the website.
This denial of inventory can cause significant financial damages, including loss of valuable inventory, revenue, and chargebacks. Unlike genuine customers, who cannot monitor prices, bots can be programmed to continuously monitor price drops and complete multiple transactions in a matter of seconds. This creates artificial scarcity of sought-after items and makes it really difficult for legitimate customers to find deals and discounts. Further, this scarcity of products drives the prices up and makes the items unaffordable for consumers.
It has been observed in recent inventory fraud cases that in addition to direct revenue losses and costs incurred on remediation, impacted businesses also incur indirect costs such as loss of productivity, operational disruption, extra burden on customer support staff, additional investments in security apparatus, and damage to brand equity.
How inventory fraud is committed
Inventory fraud scandals can be committed through various methods and schemes. Attackers study the inventory management systems of the target business and the defense mechanisms it has put in place. This information is then used to maneuver the attacks, mobilize the resources, and evade detection.
One of the easiest ways attackers use to execute inventory fraud schemes is to use bots. Scalper bots, sneaker bots and specialized inventory hoarding bots are programmed to search specific items, such as limited edition or exotic products and add them to shopping carts in huge volumes. The transactions for added items are not completed, which makes these items unavailable for regular consumers. This unavailability of products drives consumers to the competitors, resulting in loss for the affected business.
Another common inventory fraud scheme is to use fake account creation. By creating thousands of fake accounts and genuine-looking proxies that originate from different IP addresses, attackers can buy the entire inventory, while evading detection.
Telltales of an inventory fraud attack
Inventory fraud can be challenging to detect. Attackers use intelligent bots, armed with human capabilities, to interact with the defense systems and bypass them. However, there are several measures that can help identify telltales of a potential inventory fraud attack.
By identifying inventory fraud cases early, businesses can enhance account security of their consumers and take timely remedial action to mitigate risks and losses. Some of the common inventory fraud examples that can help businesses identify inventory fraud attacks are:
- Anomalous shopping patterns for specific items.
- Large volumes of order for a specific product on any given day.
- Unusual spike in traffic from unfamiliar IP addresses.
Ways to prevent inventory fraud
Often, attackers use bots to execute inventory fraud, as it allows them to achieve scale quickly. To identify these malicious bots from among good users, businesses can use advanced machine learning models, behavioral biometrics, device intelligence, and big data analytics, among others.
There are several techniques and tools that can help businesses protect themselves and their consumers from inventory fraud. Some of the common ways to prevent inventory fraud are described below:
- Additional Layer of Authentication: By using CAPTCHAs, multi-factor authentication (MFA) and other challenge-response authentication mechanisms, businesses can add verification steps and introduce friction to subject risky users for further review. It will also make it difficult to use bots to automate the inventory fraud attack.
- Firewalls: Using web application firewalls (WAFs) can help monitor suspicious activity on the website and authenticate incoming traffic.
- Continuous Monitoring: Ongoing monitoring of incoming website traffic can help businesses detect anomalies and flag suspicious user behavior for further review.
- Device Intelligence: Using parameters like operating system, browser, language, and time zone, businesses can create unique device IDs. Any deviation in behavior from known device IDs can indicate an attempted inventory hoarding attack, and trigger corrective action.
- IP Blacklisting: Blocking IPs that try to access multiple accounts can help businesses prevent account takeover attempts and unauthorized access. Further, businesses can compare the incoming IP addresses with suspicious IPs to reduce false positives.
- Rate-limiting: It is easy to identify bot traffic emanating from commercial data centers. Setting rate limits and blocking anomalous IPs can help prevent inventory fraud.
- Encryption: Use SSL encryption to protect password directories.
- Bot Management Solution: Implement an effective and comprehensive bot management solution, such as Arkose Labs’ Bot Manager.
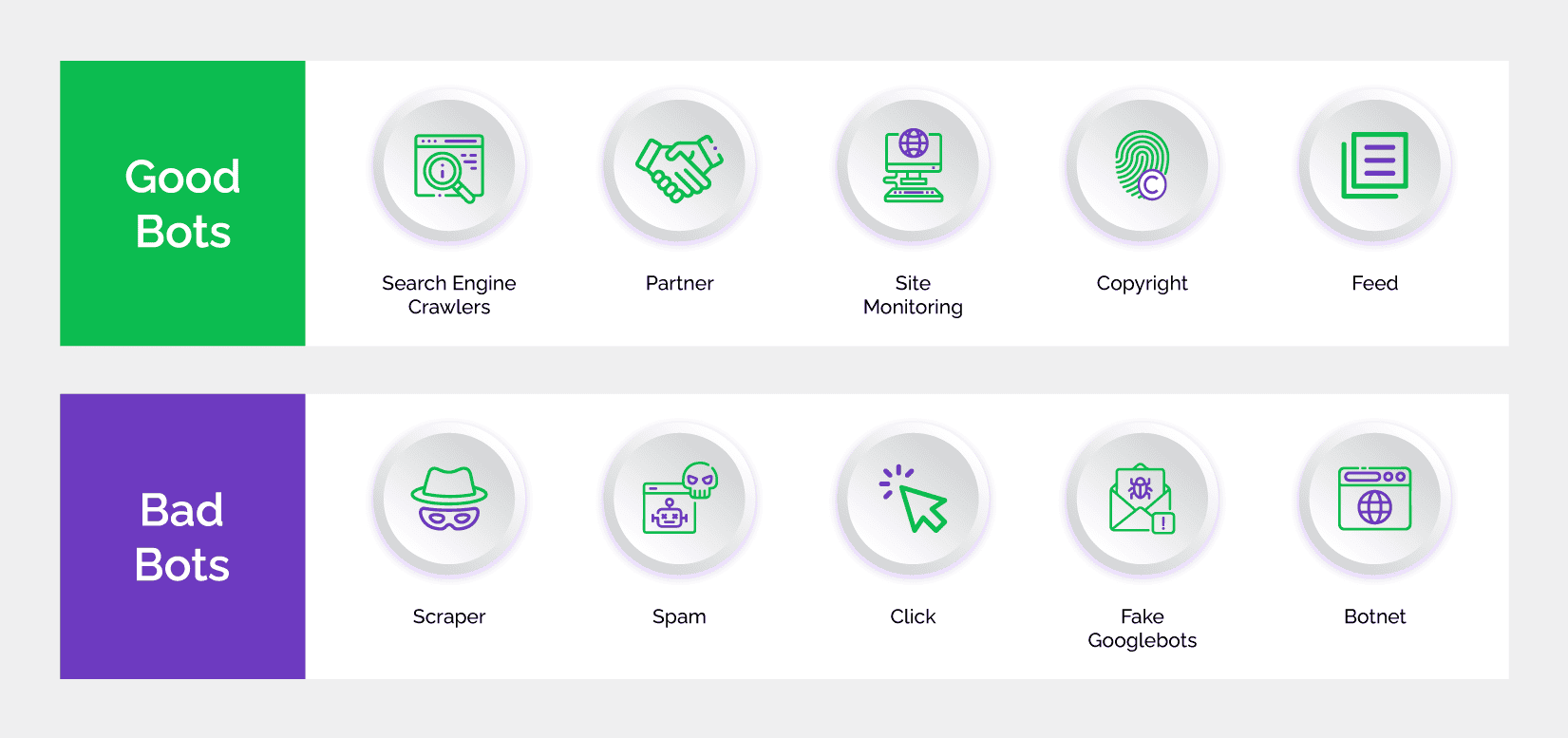
- Review: Regularly audit logs of suspicious activity to review known inventory fraud examples and use this knowledge to improve the existing security mechanisms.
Stop inventory fraud with Arkose Labs
Arkose Labs provides optimized and proactive protection to all consumer flows from inventory fraud. Arkose Bot Manager is a comprehensive bot management solution that incorporates device fingerprinting, IP reputation checks, behavioral biometrics, and Arkose Matchkey challenges—the strongest type of CAPTCHA on the market today—to provide long-term protection from automated inventory fraud attempts.
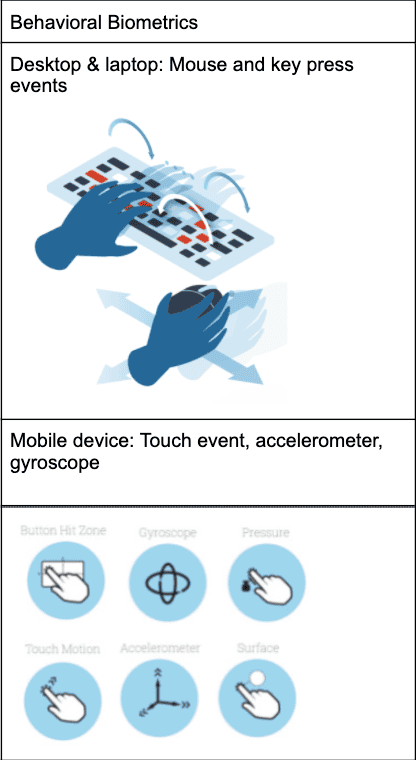
By analyzing real-time device, network, and behavioral signals throughout the customer workflow, Arkose Labs uncovers subtle indications of bot-driven and human-driven attacks, including device and location impersonation.
With real-time threat intelligence, optimized data sets, and real-time challenge feedback signals, Arkose Labs provide proactive defense and the ability to stay ahead of the evolving attacks. Arkose Labs provides transparent and actionable risk intelligence, 24x7 support for precise decision-making for improved bot mitigation and tailored threat responses, and SLA guarantee for protection from automated inventory fraud attacks.
