What is Account Takeover Protection?
Account takeover protection is the combination of security measures and protocols used to safeguard users’ digital accounts from unauthorized access. Account takeover protection is critical in today’s fast-growing digital economy because compromised accounts can lead to financial losses, identity theft, and misuse of sensitive information.
The ultimate goal of account takeover fraud prevention is to protect sensitive business and user information from being compromised and to enhance overall user account security
Why Account Takeover (ATO) Protection is Crucial
The digital economy continues to grow at a rapid pace with consumers increasingly relying on online platforms for numerous life activities, such as work, financial transactions, banking, socializing, entertainment, and more. In an interconnected digital ecosystem, compromise of online accounts can result in severe financial losses, identity theft, payment fraud, and the misuse of sensitive data.
Further, cybercriminals are leveraging sophisticated methods, including employing advanced botnets to execute targeted ATO attacks, exposing businesses and their consumers to heightened risks. While businesses face significant financial, operational, and reputational losses, consumers are exposed to financial losses, identity theft, and mental trauma.
For example, a compromised financial account would give attackers the ability to drain funds, steal financial information, misuse saved credit card details for fraudulent purchases, abuse reward points, and even apply for loans or new credit cards. The affected customer would not only face financial losses but would need to put in tremendous amounts of effort to restore their digital identity. Additionally, if the attackers used the compromised account for criminal activities such as money laundering or money muling, the affected consumer might have to face legal action.
Account takeover protection is, therefore, crucial to defending businesses and consumers from the consequences of unauthorized access to digital accounts, ensuring account security, and preserving the integrity of the online environment. Businesses should consider fortifying their defenses with measures that meet their unique business needs.
Subpar Account Takeover Detection Increases Risks
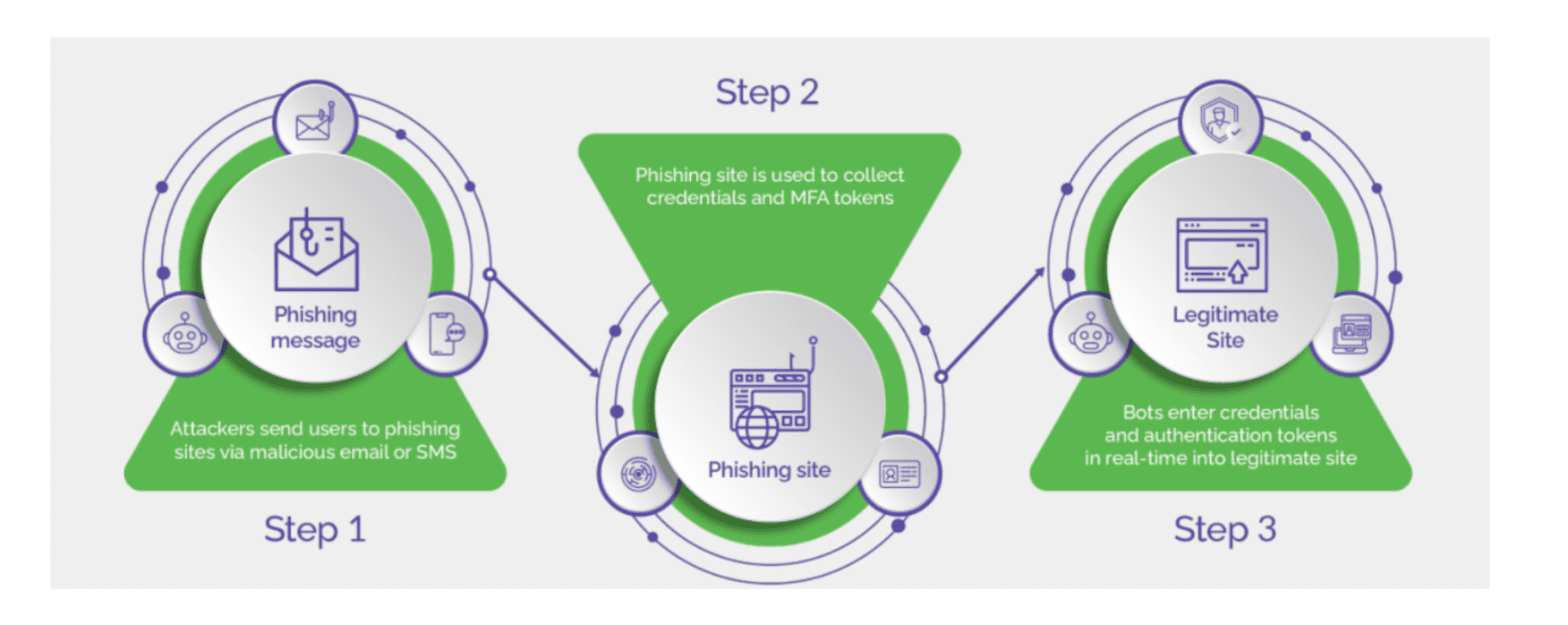
Cybercriminals leverage a full-fledged cybercrime ecosystem to power their attacks. This includes criminal toolkits, bots on demand, cybercrime-as-a-service, 24X7 support, and the sharing of cyberthreat expertise. Attackers have also studied the defense mechanisms that businesses use. Armed with the relevant knowledge and tools, attackers can execute automated bot attacks that allow them not only to achieve scale but also evade detection.
Many organizations use ATO detection solutions that do not provide the level of security that today’s modern digital businesses need. This can be detrimental for the businesses and their consumers. The inability to detect and prevent such attacks can expose sensitive personal information, financial data, and confidential communications to misuse. Cybercriminals can use this data for identity theft and the compromised accounts for numerous malicious activities, such as money laundering, phishing, malware, and spam, among others.
The lack of robust account takeover protection measures can result in damage to brand reputation and customer trust, affecting the ability to retain or acquire customers. Businesses may attract legal and regulatory action, if they fail to ensure data privacy. Operational expenses may rise as the business may need to compensate the affected users, provide assistance to customers, reset passwords, implement additional security measures, and deal with potential legal actions.
Subpar detection provides cybercriminals with opportunities to exploit vulnerabilities and compromise digital ecosystems, degrading the overall security posture and undermining the reliability of the online platform. Therefore, it is critical that businesses use robust and effective detection solutions to prevent the consequences of attacks and maintain the integrity of their digital platforms.
Account Takeover Fraud Prevention Across Industries
Account takeover attacks are a challenge for businesses across industries. As a result, the need for account takeover fraud prevention is universal. The pervasive threat of cybercriminals trying to gain unauthorized access to genuine user accounts underscores the need for robust account takeover fraud prevention, cutting across industries.
Here’s a look at how ATO affects various industries and what preventive measures can be taken:
- Financial Services: Unauthorized access to users’ bank accounts or digital accounts on finserv or fintech platforms can allow attackers to exploit compromised accounts for fraudulent transactions, fund transfers, and access to sensitive financial information, leading to severe financial losses. Banks and financial institutions must consider using robust authentication measures and real-time monitoring to detect and prevent cyberattacks.
- Retail and E-commerce: Attackers target e-commerce platforms to compromise accounts that can be exploited for financial gain through fraudulent purchases, stealing personal information, or manipulating order histories. In addition to investing in secure payment gateways and multi-factor authentication, retail and e-commerce businesses must continuously monitor user activities to detect anomalies and take timely corrective countermeasures.
- Social Media: Social media users face the risk of identity theft, misinformation, and misuse of personal data. Compromised social media accounts are often used for phishing attacks and spamming. With advanced account takeover protection measures, social media platforms can detect and prevent unauthorized access to user accounts.
- Technology Platforms: Account takeover attacks on technology platforms put invaluable intellectual property and sensitive corporate information, such as trade secrets, official communications, and other sensitive business information, at risk. It is recommended that technology platforms consider implementing strong access controls and conduct regular security audits.
- Healthcare: In the healthcare industry, ATO attacks can pose a significant risk to patients' medical records, resulting in privacy breaches and identity theft. Healthcare companies must implement strong authentication protocols and encryption measures to safeguard patient data and other medical information.
- Government and Public Sector: The vast repository of sensitive citizen data and national security information is at risk of unauthorized access and manipulation from cybercriminals targeting government systems. Strong user authentication, encryption, and continuous monitoring are some of the key measures for account takeover prevention in the government and public sector organizations.
Strategies For Account Takeover Fraud Prevention
To enhance their defenses, businesses across industries must craft strategies that ensure robust user account security and help maintain the integrity of digital platforms.
Often, effective ATO fraud prevention strategies involve a combination of technological measures, user education, and continuous monitoring. Some key strategies are:
- Behavioral Biometrics: Advanced behavioral biometrics helps monitor user activity to detect deviations from an established baseline of normal user behavior and trigger alerts for suspected account takeover attempts.
- Device Fingerprinting: Helps identify and verify the devices being used for account access. Flags unfamiliar, compromised, or rogue devices indicative of a possible account takeover attempt compromise.

- Continuous Monitoring: Detects suspicious activities, such as unusual login patterns, multiple failed login attempts, or changes in user behavior, in real-time. Informs immediate countermeasures and timely intervention for account takeover prevention.
- Fraud Detection Systems: Leverages machine learning and artificial intelligence to analyze patterns and identify suspicious activities. Adapts to the evolving threats for a proactive defense system against sophisticated account takeover attacks.
- Account Lockout: Temporarily restricts access after a specified limit of unsuccessful login attempts. Allows users the time to notice and respond to suspicious activities.
- IP Whitelisting and Geolocation Filters: Restricts access to accounts from high-risk locations or geographic regions.
- Multi-Factor Authentication (MFA): Reduces the risk of unauthorized access even if the passwords are compromised. Adds an extra layer of security above and beyond passwords by requesting users to provide additional pieces of information that may include something the user knows (password), something the user has (one-time password or code sent through SMS to the mobile device), or something the user is (biometric authentication).
- Regular Security Audits: Helps identify vulnerabilities in systems and applications, such as access controls, security patches, and monitoring for any illegitimate activities, indicative of an account takeover attempt.
- Incident Response Plan: Outlines the steps to take if an account takeover attack takes place, enabling swift response and mitigation efforts to minimize the impact of the attack.
- User Education and Awareness: Helps educate users about the best practices for online security, recognizing phishing attempts, the need to use strong and unique passwords, the dangers of reusing passwords, and enabling additional security features like MFA.
Key Features of a Good Account Takeover Prevention Solution
A good account takeover detection solution features advanced behavioral analysis that helps monitor user behavior, detect anomalies, identify and mitigate bot activity, and trigger alerts for suspicious or devious user activity. Machine learning, device intelligence, continuous monitoring, and easy integration with fraud detection systems are some of the key essentials.
A comprehensive solution not just secures access, it also provides robust reporting tools that enable businesses to monitor, review, and refine security measures frequently. It adapts to the emerging threats and dynamically adjusts security measures based on real-time risk assessment. This adaptability ensures that the solution remains effective against known and evolving attack tactics.
An effective account takeover prevention solution is user-centric and leverages the advancements in technology to deliver exceptional defense against sophisticated and targeted attempts.
Arkose Labs is Synonymous with Robust Account Takeover Protection
Arkose Labs is a trusted partner for leading global businesses in account takeover prevention. With an innovative and comprehensive approach to fighting malicious humans and bot traffic, Arkose Labs offers comprehensive and long-term protection from cyberattack across industries.
Arkose Labs leverages a host of latest technologies including device fingerprinting, behavioral biometrics, artificial intelligence, and machine learning algorithms, among others to accurately identify risky users and prevent them from gaining unauthorized access, without in any way disturbing the user experience for legitimate consumers.
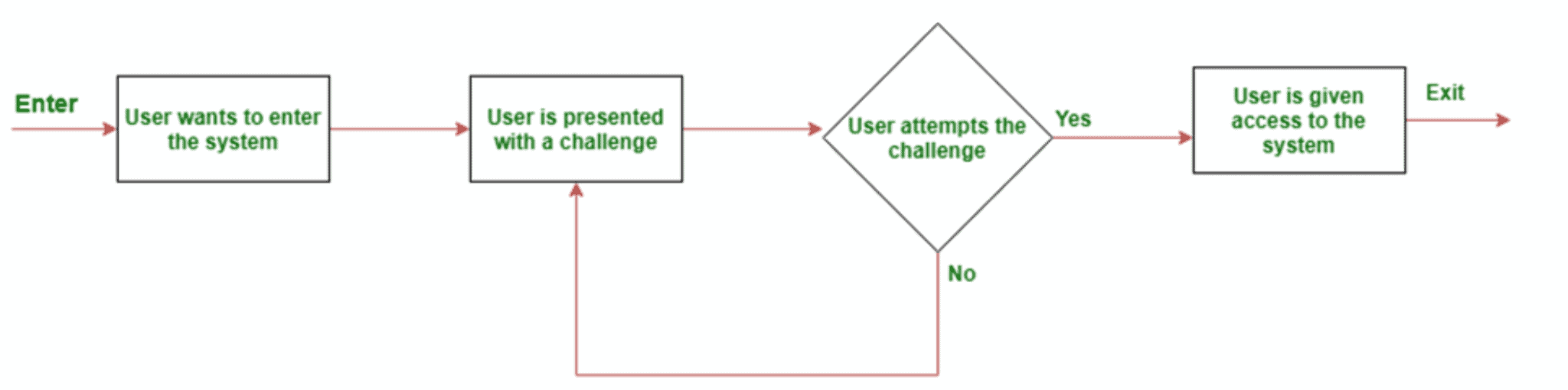
Instead of blocking any user, Arkose Labs allows them an opportunity to prove their authenticity through challenge-response authentication. Based on the real-time risk assessment, users face Arkose MatchKey challenges. Good users may not even encounter these challenges. However, those that do find Arkose MatchKey challenges are fun to solve.
That is not the case with scripts and bots, though, and they fail instantaneously. Persistent malicious humans and click-farms continue to face the many variations of Arkose MatchKey challenges that keep increasing in volume and complexity. This obstruction increases the time, effort, and resources needed to execute the attack. Since the attack becomes financially not worthwhile, attackers are forced to abandon the attack, thereby ensuring long-term protection from both human-driven and bot attacks.
In addition, Arkose Labs provides 24X7 SOC support, actionable insights, raw attributes, and the latest threat intelligence from its global network of clients, to empower its partners to mitigate the risks as soon as they are identified and ensure future-proof protection.
Looking for more information on how to protect your enterprise from ATO attacks? Check out our Account Takeover Solution Brief.
