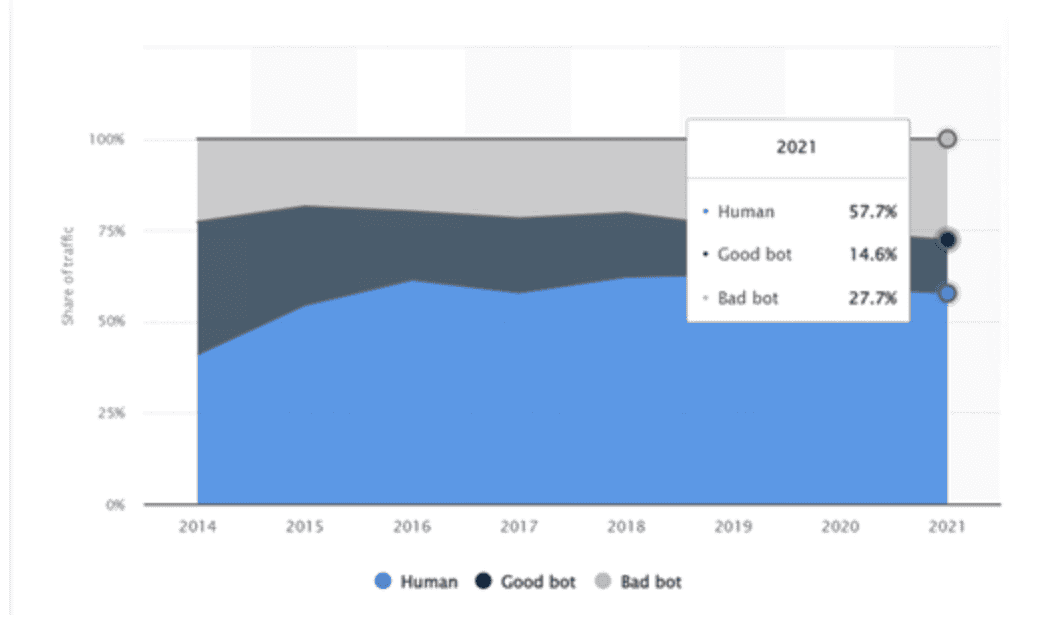
Bots have become commonplace on the internet and across devices, now making up nearly half of all online traffic. When in the hands of cybercriminals, bots can be created to spread misinformation and spam, steal information, or carry out denial-of-service (DDoS) attacks, among other uses.
Bot activity is often not easily detectable, especially considering more advanced bots currently in the wild. And they are programmed to follow a predefined script, which means finding a comprehensive solution to meet this challenge is vital.
Bot detection is an imperative cybersecurity strategy that involves identifying bots on systems and networks and determining whether their activity is malicious or benign. As with all cybersecurity strategies, bot detection should always be accompanied by security controls designed to thwart the malicious bot.
What are bots?
Bots are software programs that automate repetitive tasks such as form filling, link clicking, and text scanning. They can also converse with users through chatbots and post on social media platforms. Bots operate over a network and use algorithms to accomplish tasks such as natural language processing and pattern matching.
Although bots can be utilized for legitimate purposes like data collection and web crawling, they are also vulnerable to malicious activities like spamming and credential stuffing or account takeover attacks. The popularity of bots and their malicious potentials have given birth to bot detection technologies which aim to identify whether bot activities are legitimate or harmful by monitoring various behavioral patterns, networks, user agents, and data points.
How do cybercriminals use bots for their attacks?
Cybercriminals often use bots, or a collection of bots formed into botnets, to launch data theft and DDoS attacks, causing significant harm to enterprises. Bots can also be used to manipulate search engine rankings and click-through rates, which can hurt an enterprise’s reputation. Here are some common bot tactics used by cybercriminals:
Man-in-the-Middle attacks
One type of bot attack to be aware of is the Man-in-the-Middle attack. This occurs when a bot intercepts traffic between two parties and manipulates it in some way. In the context of cybersecurity, this type of attack can be used to steal sensitive data, such as passwords and financial information, or disrupt normal operations and steal one-time passwords as a way to commit SMS toll fraud or international revenue share fraud.
Phishing and social engineering
Phishing and social engineering are common methods used by cybercriminals to gain access to user accounts or distribute malware; many of these attacks can be enabled by bots. Over the years, fraudsters have deployed various forms of phishing by masquerading as a reputable entity in an email or SMS. These malicious messages will divert users to cloned websites, prompting them to log in at the fake site in order to gain access to their credentials. These sites will use similar URLs to the legitimate website. These attacks put user accounts in jeopardy and not only cause financial loss but also have a negative impact on brand reputation as well.
Credential stuffing and account takeover attacks
Account takeovers and credential stuffing are common types of bot attacks. Credential stuffing attacks aim to automate attempts with stolen or leaked credentials, while account takeover attacks involve cybercriminals gaining access to legitimate user accounts and using them for fraudulent purposes. For instance, a legitimate user account on a financial services site can be leveraged by a cybercriminal to commit downstream fraud, including signing up for additional credit cards, or the account can be drained.
The need for bot protection
Bot protection has become an essential component of online security for websites and businesses. Bots account for more than 40% of internet traffic and can cause a variety of online attacks, including fraud, website slowdowns, and data theft. Without adequate bot protection measures, websites can be hijacked by bots, which may lead to significant financial losses, reputation damage, and legal implications for businesses. Bot mitigation and bot management can often fall under the bot protection umbrella, and they consist of the following:
- Bot mitigation is the process of identifying and preventing suspicious activity from bots to protect sensitive information from being vulnerable to attacks.
- Bot management is a technique that blocks attacks and abuses in various industries, such as ticket scalping and content scraping. Bot protection is essential for preventing cyber crimes such as ATOs, credential stuffing, distributed denial-of-service (DDoS) attacks, and more.
Benefits of bot protection
Implementing bot protection safeguards customer and enterprise data, prevents website slowdowns and outages, and stops cybercriminal activities like financial fraud and denial-of-service attacks, among others. Therefore, it is crucial to have effective bot protection in place to protect your website and its users.
Bot protection often involves detecting and blocking malicious bots that can harm websites and steal sensitive information. A bot management solution will enable security teams to distinguish between human and bot traffic in real time. Bot detection is a key piece to protecting against automated bots. Bot detection tools often analyze web traffic to block malicious bots, often using CAPTCHAs, while allowing access to legitimate visitors and legitimate “good” bots.
Why bot protection should be part of your cybersecurity strategy
Bot protection should be a key part of any cybersecurity strategy. Bot attacks can have a severe impact on websites and applications, leading to data breaches, downstream fraud, or website outages. These attacks can hurt an enterprise’s bottom line and reputation amongst its customer base.
Bot protection and mitigation involves detecting and blocking malicious bots from accessing your website or application, protecting your data from being stolen or compromised. Blocking unwanted bot traffic frees up valuable resources and enables your security teams to focus on innovation, growth, and continue digital transformation. When the proper advanced solution is applied, bot management can even improve the user experience for legitimate customers as they won’t be faced with frustrating puzzles to solve, in many instances.
Conclusion
Bot detection is a critical cybersecurity protection measure that companies can use to ensure their digital assets and customer data are not compromised. It is essential for organizations to leverage a layered approach to security so that malicious bots do not infiltrate their systems. Enterprises can leverage artificial intelligence (AI) and machine learning capabilities to detect bots in web traffic. The use of automated tools for bot detection ensures human resources and time are not wasted on malicious bots attempting to breach cyber defenses. It also reduces the chance of malware infection and other bot-related cyberattacks.
Arkose Labs Secures Enterprises from Bots
Arkose Labs’ effective bot management solution effectively mitigates malicious bots targeting enterprises. Arkose Labs accurately distinguishes between human and automated traffic to neutralize automated spam attacks. Using a combination of dynamic risk decisioning and targeted friction, through Arkose MatchKey challenges, Arkose Labs makes the attack incrementally more costly for cybercriminals, which prevents them from scaling up their operations. Once a cybercriminal realizes that their attack is no longer financially tenable, they will look elsewhere.
Bot management from Arkose Labs is so effective that it is even backed by a service level ZeroBot Guarantee. This provides assurance that Arkose Labs will defeat bot attacks within a set timeframe, protecting legitimate users from phishing scams, malicious messages, and more.








 1
1