Microsoft has made a groundbreaking revelation, uncovering the workings of a nefarious cybercrime syndicate identified as Storm-1152, a group specialized in creating and distributing fraudulent Microsoft accounts.
This announcement follows an intensive collaboration with Arkose Labs, a leading cybersecurity defense firm, leveraging threat intelligence insights to unmask the illicit activities of Storm-1152.
The group Storm-1152, operating within the shadows, has been fabricating counterfeit Microsoft products, contributing to a range of cybercrimes, including phishing scams, identity theft, fraud, and distributed denial of service (DDoS) attacks. These fraudulent accounts, acting as gateways for criminal activities, were distributed through illicit websites and social media platforms, providing tools to evade identity verification measures across prominent technology platforms.
Estimates reveal that Storm-1152 has generated roughly 750 million fraudulent Microsoft accounts, resulting in illicit profits in the millions while inflicting substantial financial damages on Microsoft and associated companies in their efforts to combat these criminal endeavors.
Microsoft, in its bid to impede the rapidity of cyberattacks orchestrated by such criminal entities, aims to raise the cost of their operations. However, the investigation remains ongoing as the company continues to prioritize safeguarding its customers and online users.
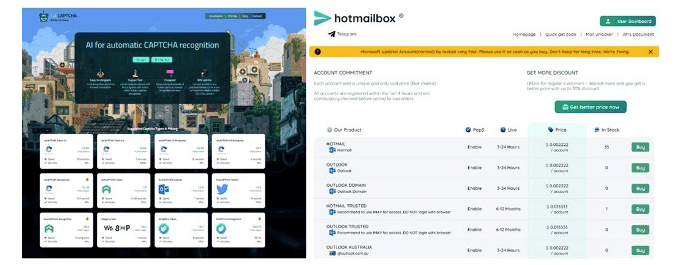
Storm-1152’s role within the cybercrime landscape extends beyond mere fabrication of fraudulent accounts. The syndicate operates as part of a sophisticated cybercrime-as-a-service ecosystem, catering to the escalating demand for fraudulent accounts necessary to fuel automated criminal activities. Rather than investing time in creating numerous accounts, cybercriminals can conveniently purchase them from Storm-1152 and analogous groups, channeling their efforts toward executing malicious agendas such as phishing, spamming, ransomware, and other forms of fraudulent behavior.
Microsoft Threat Intelligence has flagged multiple ransomware and extortion groups utilizing Storm-1152 accounts, including Octo Tempest, aka Scattered Spider, engaged in financially motivated cybercrime activities worldwide. Moreover, the syndicate’s impact extends to other threat actors like Storm-0252 and Storm-0455, enhancing their attacks through purchased fraudulent accounts.
Taking decisive action, Microsoft obtained a court order from the Southern District of New York to dismantle Storm-1152’s U.S.-based infrastructure, effectively shutting down their websites. The crackdown targeted platforms selling fraudulent Microsoft Outlook accounts and tools facilitating identity verification bypass services for various technology platforms.
While reinforcing its commitment to ensuring a secure digital environment, Microsoft, in collaboration with Arkose Labs, has deployed an advanced CAPTCHA defense system. This system mandates users seeking to open Microsoft accounts to prove their human identity, deterring bot-related activities.
The investigation has pinpointed key figures behind Storm-1152’s operations – Duong Dinh Tu, Linh Van Nguyễn (also known as Nguyễn Van Linh), and Tai Van Nguyen – based in Vietnam. These individuals orchestrated the syndicate’s operations, developing code for illicit websites, providing tutorials on using their products, and offering customer support for their fraudulent services. Their actions not only breach Microsoft’s terms of service but also aim to harm users of Arkose Labs by deceiving and defrauding victims under the guise of legitimate users.










