In a card testing attack, fraudsters make small card payments for credit card testing. Using stolen credit card or debit card credentials along with automated scripts and bots, attackers test the compromised card details quickly, repeatedly, and at scale, without raising suspicion.
What Is a Card Testing Attack?
Card testing, carding, or card cracking is a tactic where fraudsters verify the validity of stolen credit card information and then make low dollar amounts purchases or authorization requests to verify whether the cards are still active. Once validity and status are established, fraud actors use valid card details for larger purchases, payment fraud, and card not present (CNP) fraud or to resell these details on the dark web.

How Card Testing Attacks Work
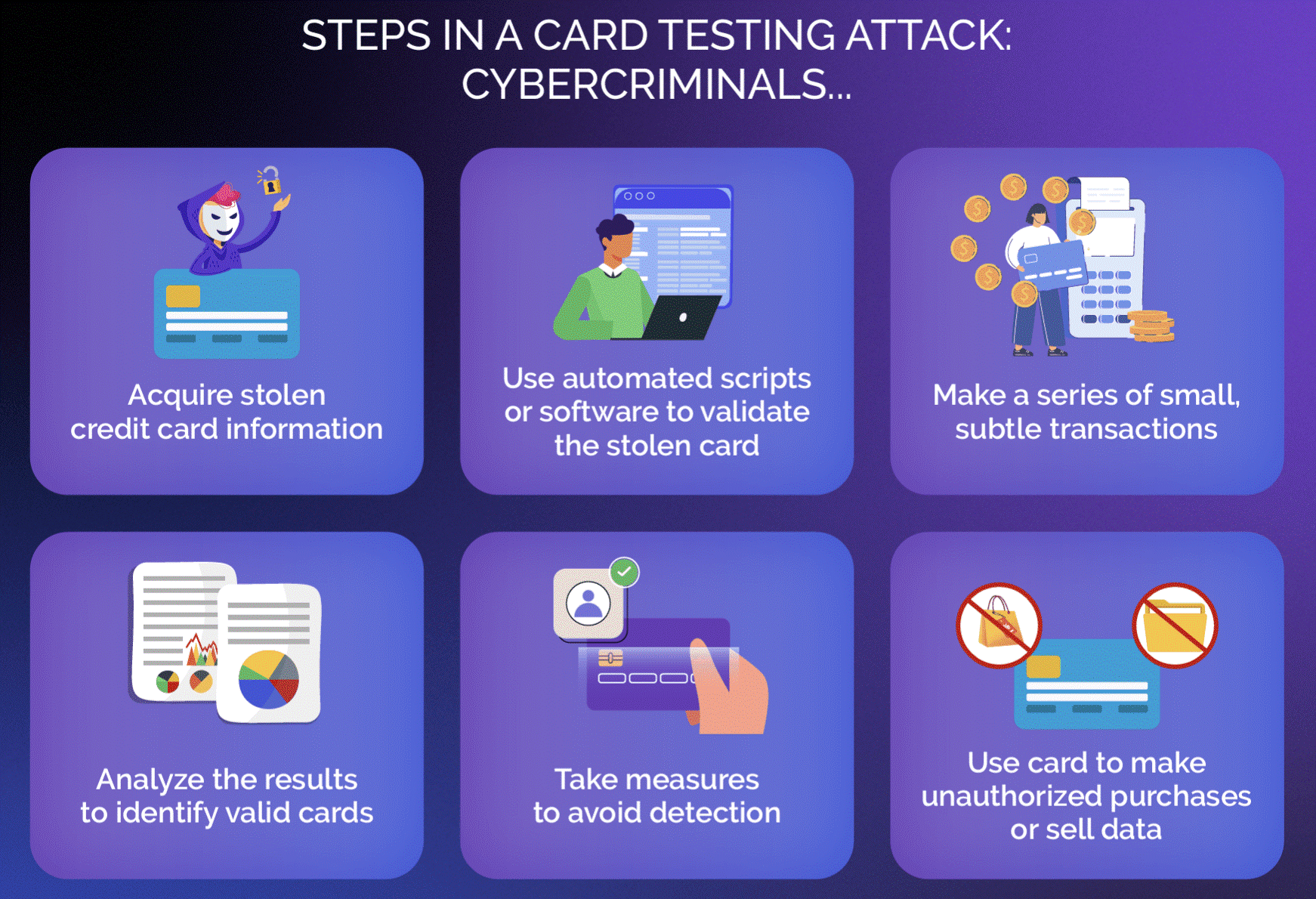
There are three key steps of a card testing attack, namely:
- Credential Harvesting: Access card credentials through theft or purchase from the dark web.
- Validation: Use bots to verify the validity of credit card numbers and other details.
- Fraud: Make small transactions of low-dollar amounts to check whether the card is still active.
Active card details can then be used to max them out with larger purchases, cash withdrawals, and other fraudulent activities.
Industries Most Affected by Card Testing
Due to an increase in digital transactions, every industry is facing the scourge of card testing attacks. The prime targets being:
- eCommerce platforms, due to high volumes of transactions processed.
- Financial institutions and banks for unauthorized transactions and to exploit ATM machines and online banking portals.
- Online Gaming, for purchase of in-game items, microtransactions, or making bets.
- Hospitality and Travel to book rooms or flights.
- Subscription Services such as streaming services, magazines, or software providers, to access paid content without legitimate payment.
- Digital Goods and Gift Cards for purchase and resale to third parties.
- Online Marketplaces to make unauthorized purchases or list items for sale.
- Charitable and non-profit organizations, to abuse charities for financial gain.
- Social Media Advertising to exploit the platform's ad targeting capabilities.
Negative Consequences of Card Testing Attacks
Card testing attacks cause significant financial losses to businesses. When the cardholder detects fraud and disputes the transaction, businesses suffer losses in the form of chargeback requests and refund amounts. Further, investments in fraud detection tools, customer services, incident response, and updates to fraud prevention measures, add to the financial burden.
Operational disruption is a major consequence of card testing attacks, resulting in a significant increase in workload of customer support, IT, financial teams, and delays in transaction processing, while also diverting resources from core business activities.
Damage to the market reputation of your business due to card testing attacks can erode customer trust, leading to customer attrition, serious brand damage, and negative publicity through social media. Implementation of fraud prevention tools may introduce friction, resulting in high decline rates, loss of revenue, and customer dissatisfaction.
Businesses unable to protect customer data face legal action, fines, and penalties due to non-compliance with the prevailing regulations.
Card Testing is a Headache for Businesses
Card testing attacks pose a growing challenge as more and more fraud actors use automated tools for card testing attacks.
In addition to aforementioned financial, reputational, operational and compliance related losses, organizations lose future business opportunities and become exposed to repeat attacks.
In recent years, with increasing prevalence of bot-driven automation, attackers can validate credit card information in bulk and in a matter of minutes to improve the success rate. Since bot traffic can initiate several small, inconspicuous transactions, attackers can check the validity of large volumes of card data within a short time frame, before getting detected or blocked.
Bots can scrape websites and distribute bot traffic by rotating IP addresses to evade being blocked by rate-limiting or IP-based blocking mechanisms. Further, by randomizing transaction details, bots can make the transactions appear more legitimate, and fool fraud detection systems by solving legacy CAPTCHAs.
Identifying Card Testing Fraud Attempts
To identify card testing attacks, businesses can monitor transactions and look for telltales listed below:
- Unusual transaction patterns, multiple and successive transactions within a short time frame.
- Common and low-dollar amounts for transactions (e.g., $1, $5, $10).
- Use of sequential, predictable, or those card numbers with easily guessable patterns.
- High volumes of transactions within a short time from a single IP address.
- Geographic inconsistencies, transactions with different shipping and billing addresses, transaction requests from regions that the business does not serve.
- Multiple failed authorization attempts with different card numbers, frequent use of incorrect CVV/CVC codes.
- A sudden spike in new customer account registrations with similar or suspicious email addresses.
- Frequent changes made to account information.
Ways to Prevent Card Testing Attacks
Preventing card testing attempts can be an arduous task due to the evolving attack tactics. Since no single solution can guarantee 100% protection against card testing attacks, businesses must consider various digital tools and strategies to prevent card testing attacks, including:
- Bot Management Solution: Use smart bot management solutions, such as Arkose MatchKey, to identify and stop automated bot attacks.
- CVV Numbers: Ask for Card Verification Value (CVV) during online transactions to ensure users have physical possession of the credit card, as most fraud actors don’t have valid CVV data.
- Address Verification System (AVS): Use AVS and IP geolocation to match billing address provided during a transaction with the address on file with the credit card issuer and the location of the IP address from where the transaction originates, respectively.
- Velocity Limits: Prevent IP address card testing fraud by setting threshold limits to restrict the number of transactions from the same IP address, email address, or card in a short time frame.
- Checkout Attempts: Limit the number of times a buyer can attempt to complete an order in a single shopping cart session.
- Transactions from Unserved Geographies: Compare the geographic location of transactions with the cardholder's known location and block requests from geographies that the business does not operate in.
- Customer Sign Up: Eliminate guest checkout and permit transactions only from registered customers.
- Firewall to Guard Against Botnets: Use web application firewalls (WAFs) to detect and prevent access from botnets.
- Transaction Review: Review all credit card transactions to detect and block unusual activity. Keep fraud prevention rules and parameters updated to adapt to evolving fraud tactics.
- 3D Secure: Use 3D Secure to add an extra layer of security by requiring cardholders to authenticate their identity with a one-time password or PIN during online transactions.
- Machine Learning and AI: Detect anomalies or unusual transaction patterns to identify potential card testing activities.
- Device Fingerprinting: Recognize unique attributes of the user's device to identify suspicious devices.
- Third-Party Fraud Monitoring Tool: Outsource fraud monitoring tools that identify and protect against card testing attempts and trigger alerts for further investigation.
Key Features of a Good Bot Management Solution
Bot management solutions are essential for detecting and mitigating bot-driven card testing attacks.
Some commonly used bot management solution components are:
- Behavioral Biometrics
- Device Fingerprinting
- Rate Limiting and Throttling
- Bot Detection and Prevention Services
- Machine Learning and AI
- IP Reputation Lists
- Challenge-Response Authentication
- User-Agent Analysis
- Reputation-Based Risk Scoring
- API Security
- CAPTCHA
- Monitoring and Reporting
Work with Arkose Labs to Fight Automated Card Testing Attempts
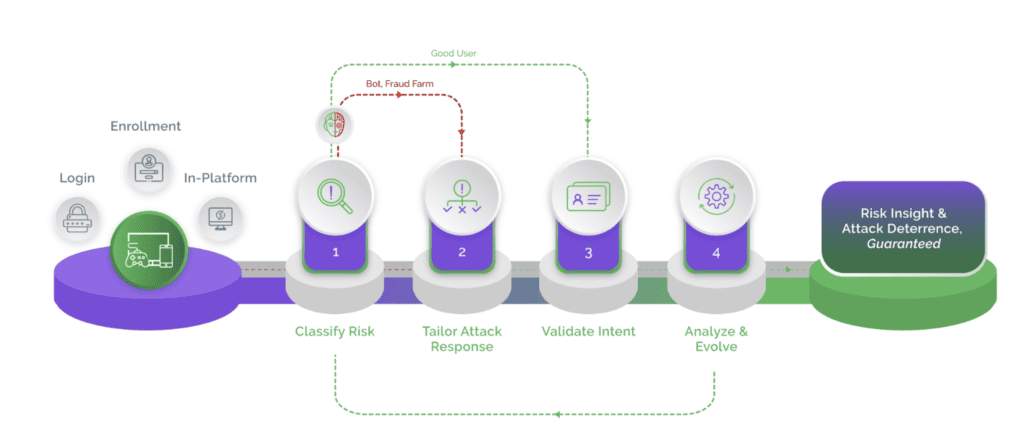
Several Fortune 100 companies trust Arkose Labs to fight bots of all advancement levels for future-proof bot protection. With Arkose Bot Manager, businesses can thwart automated bot attacks to provide businesses with comprehensive security against automated card testing attacks.
Depending on users’ real-time risk assessment, Arkose Labs administers Arkose MatchKey challenges. Good users find these challenges fun to solve, but even the most advanced bots fail instantly. This is because Arkose MatchKey challenges are trained against the latest computer vision technologies, and are resilient to the most intelligent bots. Using a continuous stream of increasingly complex challenges, Arkose Labs keeps human attackers engaged until the time, effort, and resources needed to continue the attack outweigh the returns, thereby forcing attackers to abandon the attack.
Arkose Labs provides 24x7 SOC support, data-driven actionable insights, and global threat intelligence, to help its partners stay ahead of emerging tactics and ensure long-term protection from card testing attacks.
