In their quest to maximize returns from these attacks, bad actors are increasingly using bots and automation. Not only are bots cheap and easily available, but their abilities to mimic human behavior and scale up attacks in no time increases the success rate for attackers.
What Are Bots?
Bots, or automated software programs, can enable high-volume spoofing attacks by automating the process of creating and sending a large number of hoax messages, requests, or interactions in a relatively short amount of time.
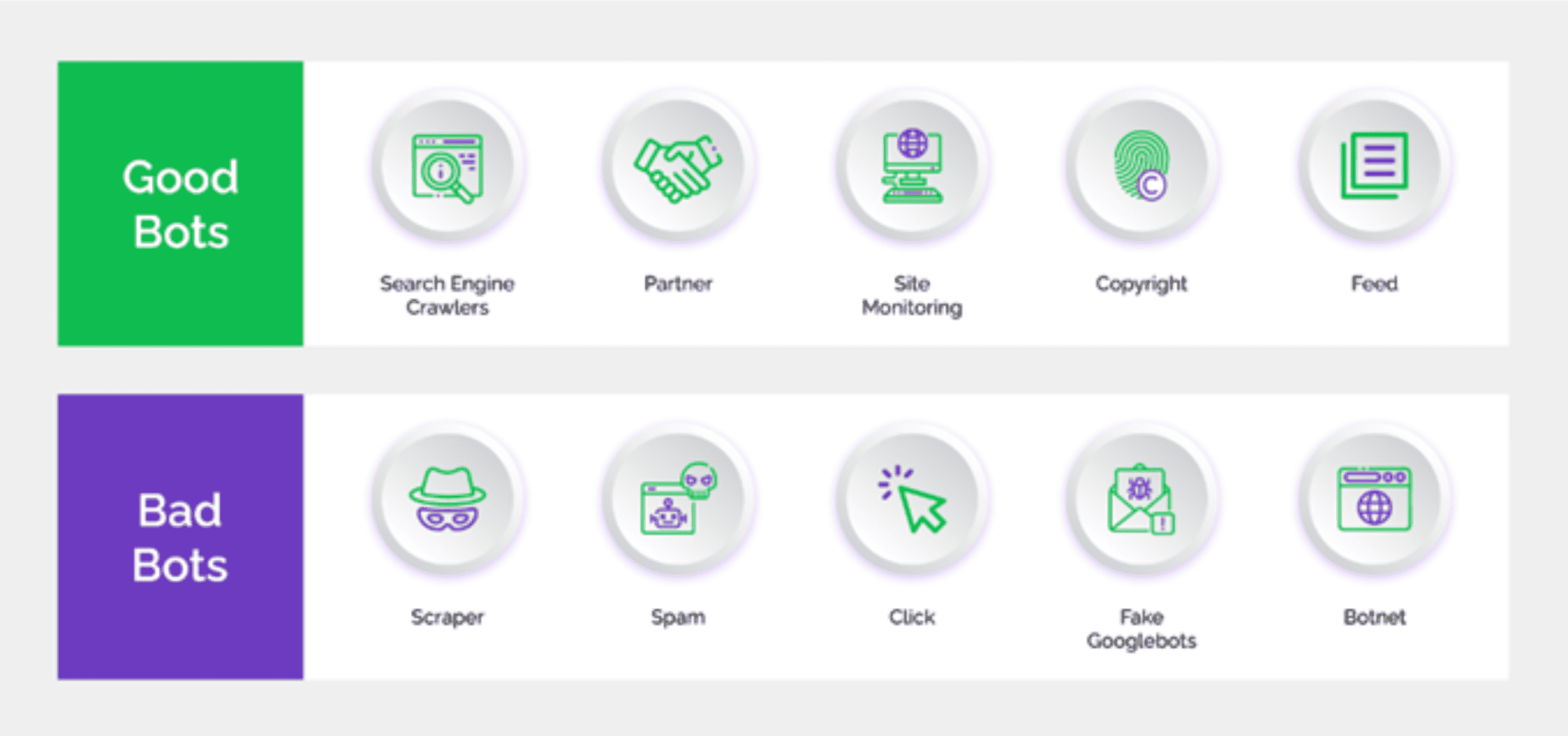
Bots and High-Volume Attacks
In addition to their ability to facilitate high-volume attacks by repeatedly generating and disseminating bot traffic in the form of spoofed messages, emails, or requests without manual intervention, automated bot attacks can allow attackers to target a wide audience quickly.
Because bots operate at high speeds, attackers can send large volumes of spoofed data or requests within a short duration and quickly scale up the attacks. Automation combined with speed and scale allows attackers to increase the impact of the threat.
Unlike human attackers, bots can persistently operate 24/7 without tiring or requiring breaks. However, like humans, some intelligent bots can mimic human behavior, such as the ability to vary the timing of their actions, imitate human typing patterns, or engage in human-like conversations. They can interact with security mechanisms that require nuanced human interaction to fool them and even use evasion tactics such as rotating IP addresses and different user agents. This makes it more challenging for security teams to detect them.
Spoofing Is a Common Characteristic of Bot Attacks
With spoofing, bots can deceive users and systems, hiding the real identity of the source of the attack. This provides anonymity to attackers and reduces the risk of detection.
Bots can impersonate legitimate users or systems to power credential stuffing, account takeover, fake account creation, or engage in other fraudulent activities. They can spoof trusted entities or individuals to trick users into taking actions they otherwise wouldn't, thereby scaling up phishing attacks.
By spoofing the source IP addresses, bots can amplify the volume of traffic directed at the target, resulting in disruption of online services or platforms. This high volume of spoofed requests can cause server overload and distributed denial of service (DDoS) attacks, making it difficult for legitimate users to access a service.
Further, bots use spoofing to mimic legitimate user behavior and evade detection by bypassing security measures. In some cases, bots use spoofing to hide the true destination of data being exfiltrated from a compromised system. This makes it harder for security teams to detect and prevent data breaches.
Different Types of Spoofing Attacks
Spoofing attacks come in various forms, each targeting different aspects of communication or interaction. These attacks are often used to deceive individuals, gain unauthorized access to systems, and carry out various forms of cybercrime.
Email Spoofing
Forging a sender's email address in an email message to make it seem as if it's coming from a legitimate source, thereby tricking recipients into revealing sensitive information.
Caller ID Spoofing
Manipulating the caller ID information displayed on the recipient's phone to make it appear as if the call is coming from a trusted source.
IP Address Spoofing
Spoofing the source IP address in network packets to make it look like the data is coming from a trusted source.
GPS Spoofing
Exploiting global positioning system (GPS) signals to deceive navigation systems and devices in order to mislead users about their physical location or route.
DNS Spoofing
Manipulating Domain Name System (DNS) responses to redirect users to malicious websites or resources when users believe they are accessing a legitimate one.
Website Spoofing
Creating fake websites that mimic legitimate ones to deceive users into sharing sensitive information, such as login credentials or personal details that are then used in phishing and other attacks.
MAC Address Spoofing
Changing the Media Access Control (MAC) address of their network adapter to impersonate a trusted device on a network, potentially gaining unauthorized access.
ARP Spoofing
Manipulating the Address Resolution Protocol (ARP) cache on a local network to associate a legitimate IP address with a different MAC address and intercept network traffic.
VoIP Spoofing
Exploiting the information sent in voice calls made using VoIP (Voice over Internet Protocol) to impersonate a different caller or hide their true identity for fraudulent telemarketing or phishing calls.
SMS or Text Message Spoofing
Sending SMS messages with a forged sender ID, making it appear as if the text message is coming from a different source.
Content Spoofing
Manipulating the content of a website or web application such as fake login pages, altering the content, or using misleading or false information to deceive users.
How are Spoofing Attacks Executed?
The effectiveness and consequences of a spoofing attack can vary widely based on the attacker's skill level, the target's security measures, and the specific type of spoofing being used. As a result, the steps involved in a successful spoofing attack may vary depending on the type of attack.
A general outline of the common steps that an attacker might follow are as mentioned below:
- Research: Conducting initial research to identify potential targets and vulnerabilities. This might include scanning for open ports, gathering information about the target network or system, and identifying potential weaknesses to exploit.
- Target Selection: Selecting a target for the spoofing attack.
- Gathering Information: Collecting information about the target, such as IP addresses, domain names, email addresses, or user behavior patterns.
- Spoofing Setup: Depending on the type of spoofing attack, setting up the necessary tools or configurations to impersonate a legitimate entity.
- Execution: Initiating the attack, sending spoofed data, messages, or requests to the target or network.
- Deception: Deceiving the target into believing that the spoofed information is legitimate.
- Exploitation: Exploiting the trust or access granted through the spoofing attack.
- Evading Detection: Erasing or obfuscating evidence of spoofing by deleting logs, clearing traces, or exiting the compromised system.
- Persistence: In certain scenarios, attackers may aim to maintain a presence on the target system or network for future exploitation by planting backdoors or malware to ensure ongoing access.
- Escalation: Attackers may use spoofing as a stepping stone for further attacks, such as launching additional attacks from the compromised system or leveraging the spoofed access to gain more privileges. This enables them to further exploit systems and further monetize their crimes.
Tools and Techniques Used in Spoofing
Spoofing attacks can employ a variety of tools and techniques to manipulate data, deceive users, and impersonate legitimate entities. Some of the tools and techniques attackers commonly use in spoofing attacks include:
- Network packet crafting tools
- Proxy servers
- Script libraries to forge email headers, sender addresses, and other email attributes
- Tools to intercept and manipulate web traffic
- Online services to change the displayed caller information when making phone calls
- GPS signal generators
- Tools to manipulate HTML or JavaScript code to deceive users or make fake web pages appear more convincing
- Proxy chaining to hide their true source IP address
Common Patterns in Spoofing Attacks
Although spoofing attacks take various forms, they feature common patterns and characteristics. These may include impersonation, deceptive communication methods, manipulation of data, and phishing email attacks.
Some traffic-related patterns include manipulating URLs, sender addresses, and caller IDs, misdirecting web traffic to malicious sites or resources, amplifying the volume of attack traffic by using multiple spoofed sources, establishing ongoing access or control over a system, or flooding recipients with deceptive messages for service disruptions or network congestion.
Often, spoofing involves identity theft where the attacker pretends to be a specific device or user, deceiving recipients into revealing personal or financial information, and evading security measures.
Identifying a Spoofing Attack
Threat actors use various tactics to manipulate communication or data. This makes identifying a spoofing attack challenging. Recognizing spoofing attacks often requires a combination of vigilance, knowledge, and best practices. Businesses must stay updated with the threat trends and maintain continuous monitoring to identify a spoofing attempt.
Some common indicators that can help businesses identify a potential spoofing attack are:
- Discrepancies in sender's identity, such as unusual characters or inconsistencies
- Anomalous email headers with inconsistencies in the message headers
- Altered or misspelled domain names
- Generic greetings instead of personalized greetings as used by most legitimate organizations
- Poor grammar and spelling
- Email or website content that requests sensitive information
- Unexpected attachments
- Lack of valid SSL/TLS certificates, missing padlock icon in the address bar
- Caller ID discrepancies
Protective Measures Against Spoofing Attacks
It is critical for businesses to adopt protective measures against spoofing attacks to safeguard their digital presence and sensitive information. With proactive protective measures, enterprises can significantly reduce the risk of falling victim to spoofing attacks and enhancing their overall cybersecurity posture.
Businesses should consider implementing bot preventative measures such as:
- Email authentication mechanisms like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) to verify the authenticity of email senders and reduce email spoofing
- Two-factor authentication (2FA) or multi-factor authentication (MFA) to add an extra layer of security against unauthorized access to email, social media, and other online accounts, even if login credentials are compromised
- Secure communication protocols like HTTPS for web browsing and SSH for secure remote connections and prevent man-in-the-middle (MitM) attacks
- Updates to operating systems, applications, and security software, and patches for vulnerabilities that attackers may exploit
- Intrusion prevention systems (IPS) to monitor network traffic and detect spoofing or suspicious activities
- Network-level security measures, such as firewalls, to block unauthorized access and filter out malicious traffic
- Access controls on networks and systems, based on the principle of least privilege
- Encryption for sensitive data in transit (SSL/TLS for web traffic) and at rest (disk encryption) to protect against data theft
- Security Information and Event Management (SIEM) system to collect and analyze security event data from various sources, for bot detection and spoofing attempts
- Regular security audits and vulnerability assessments to identify and address potential weaknesses in the security infrastructure
Can Spoofing Attacks be Completely Avoided?
Automated spoofing attacks are often carried out at scale by attackers, making them persistent threats. While it's challenging to completely avoid automated spoofing attacks, businesses can implement aforementioned cybersecurity measures to significantly reduce the risk and mitigate their impact. A combination of these measures can provide the organization with a robust protective shield against spoofing attacks. It is also important to maintain a proactive stance on cybersecurity and stay informed about emerging threats and evolving attack techniques.
Block Bots With Arkose Labs
Several Fortune 100 companies trust Arkose Labs for long-term protection against bot attacks. Arkose Labs leverages a unique approach and smart bot management solution, Arkose Bot Manager, to fight bot-driven spoofing attacks. Instead of outright blocking any user, which may include potential revenue-generating customers, Arkose labs allows every user to prove authenticity.
Based on their real-time risk assessment, users are presented with Arkose MatchKey challenges. This user-centric challenge-response authentication mechanism ensures good users can continue with their digital journeys with no disruption, whereas risky sessions are intercepted and challenged to establish their legitimacy.
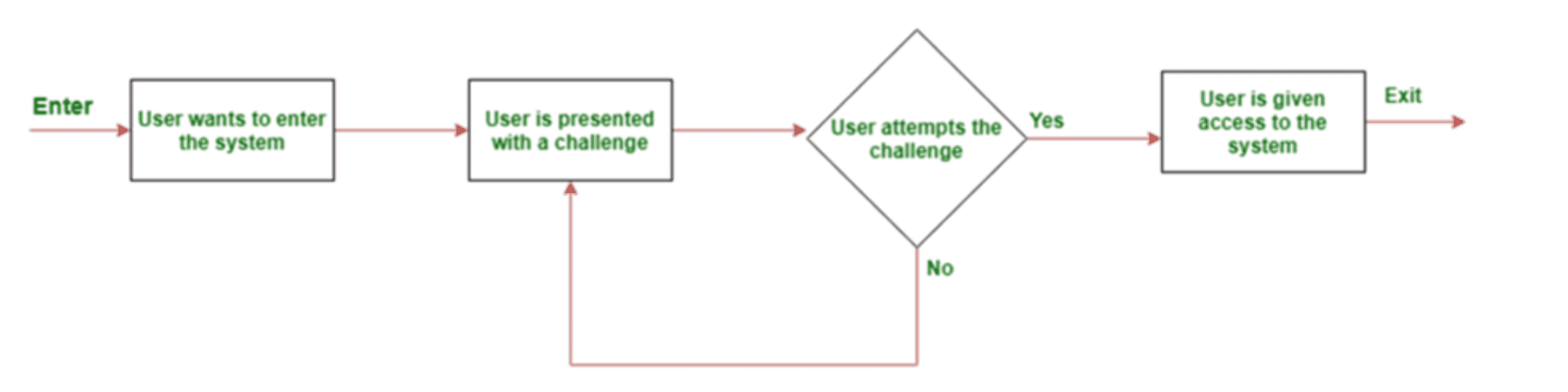
Bots and automated scripts are no match to these proprietary challenges and fail quickly. Persistent malicious human attackers and click farms trying to solve the challenges are bound to fail as each Arkose MatchKey challenge has a vast repository of variations, which makes it impossible to solve them at scale. This forces the attackers to give up for good, thereby ensuring long-term protection for the business.
Arkose Labs not only shares actionable insights, data and threat intelligence from its global network of clients but also provides 24x7 SOC support and helps partners understand the scope of evolving spoofing attacks. This empowers them to make informed decisions, mitigate risks, and stay ahead of emerging attack vectors.
To learn more about how Arkose Labs helps global businesses fight cyberattacks without impacting user experience, please contact us for a demo.







