Automated extraction of data, such as posts, comments, user profiles, and any other information, from across several social media platforms is called social media scraping.
![]() A lot of time researchers, businesses, and developers often browse through social media sites and engage in the data collection process for market research, sentiment analysis, predicting market trends, or understanding consumer behavior. However, when attackers scrape and use data from social media platforms for nefarious activities, it violates ethical standards and raises legal concerns, especially regarding user privacy.
A lot of time researchers, businesses, and developers often browse through social media sites and engage in the data collection process for market research, sentiment analysis, predicting market trends, or understanding consumer behavior. However, when attackers scrape and use data from social media platforms for nefarious activities, it violates ethical standards and raises legal concerns, especially regarding user privacy.
In this guide we will delve into automated social media scraping, where attackers use bots, automated scripts, and malicious human fraud farms to scrape data from social media sites and use this harvested information for criminal activities.
The mechanics of social media scraping
Manual scraping of data takes time and cannot be scaled up. Therefore, attackers use bots and scripts to automate the process of gathering data from various social media platforms. They either use official APIs of the social media platforms or web scraping tools and techniques to scrape valuable information.
Why social media scraping is a growing threat to social platforms
Due to unauthorized access and theft of user data, potentially resulting in identity theft and violation of users’ privacy, social media scraping has grown into a huge challenge for social platforms.
Automated bot attacks at scale can strain the target platform's servers and infrastructure, causing operational disruptions and performance issues. Further, by undermining the social platform's ability to control and monetize access to its data, social media scraping impacts its business strategy and erodes user trust.
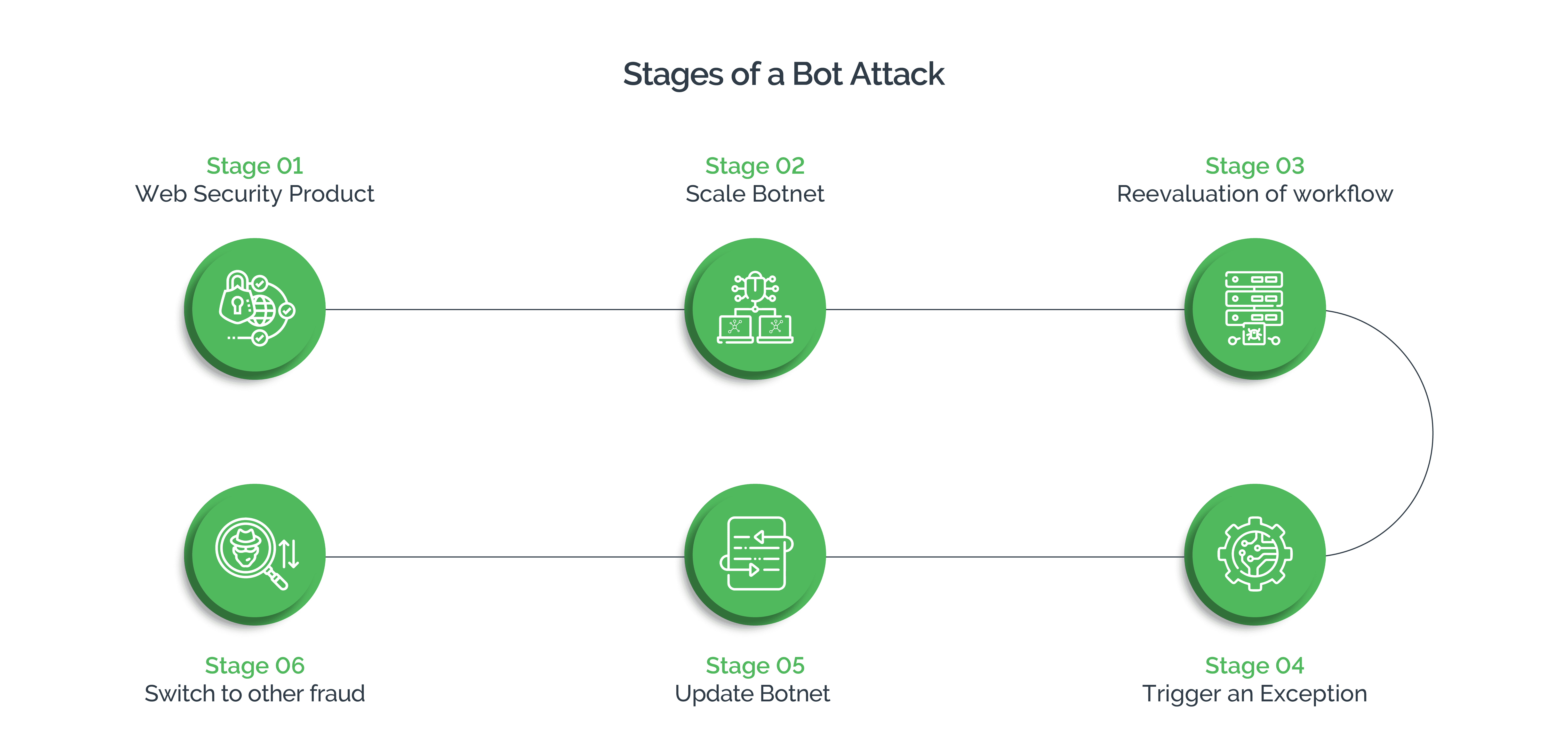
Role of bots in social media scraping
In recent times, attackers extensively use bots to automate the data extraction process. Automated data scraping is a quick and dirty way for attackers to harvest social media data at scale and speed, with minimum investment. A combination of open accessibility, unprotected Application Programming Interfaces (APIs), easily structured HTML, insufficient anti-scraping measures, and more, contribute to the ease of website scraping.
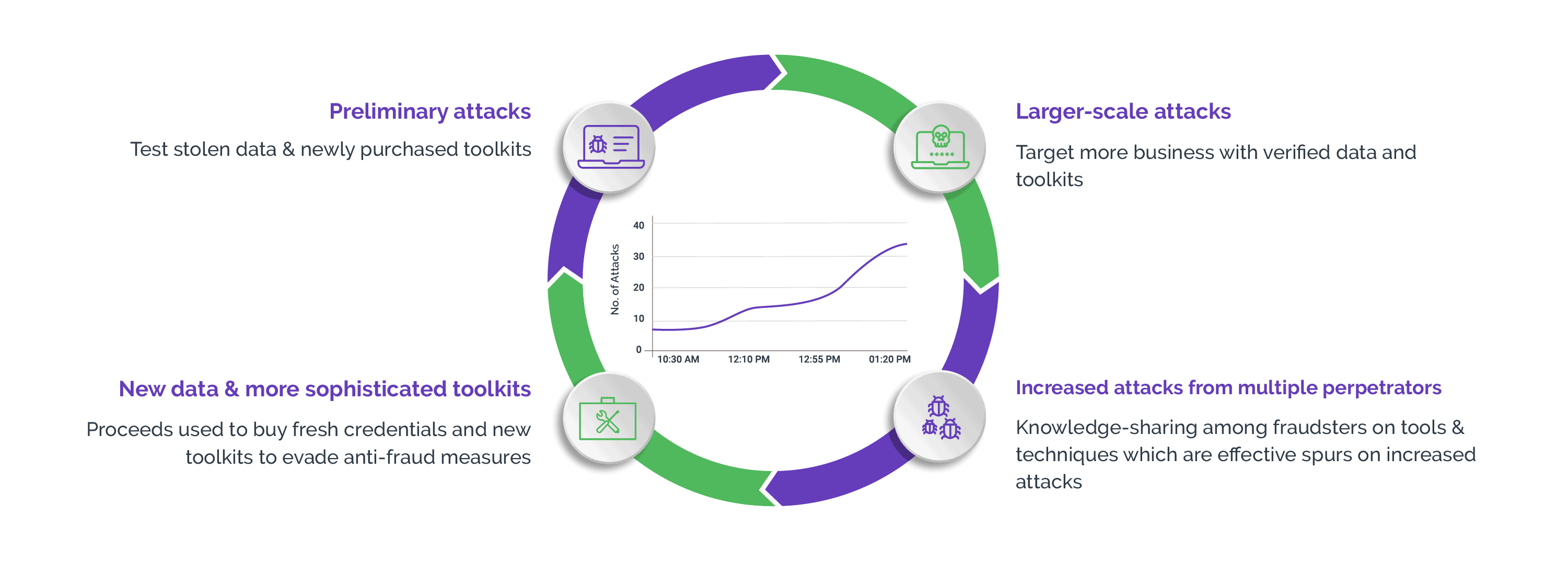
Attackers program bots to mimic human behavior, enabling them to navigate social media platforms and collect sensitive data. These bots can seamlessly access the social media platform’s APIs or use scraping techniques to systematically extract information from web pages.
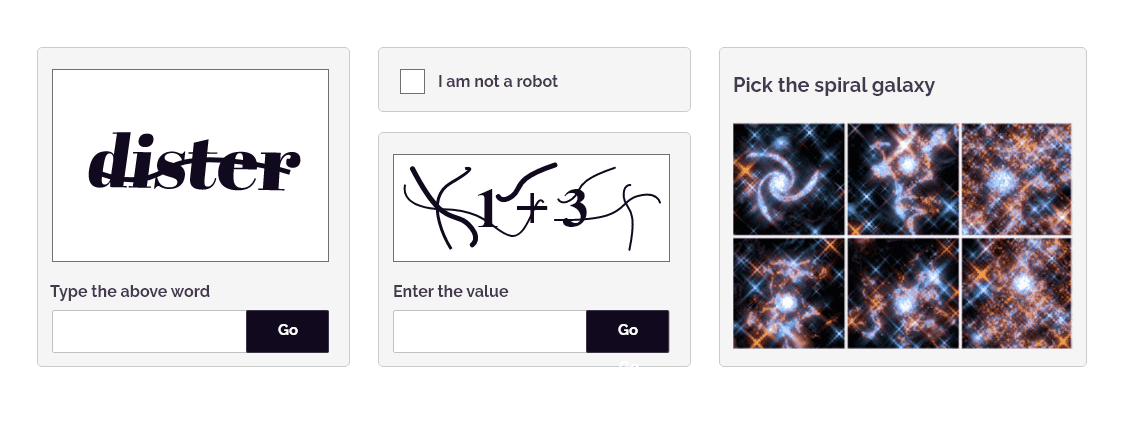
Thanks to advancements in technology, bots can interact with defense mechanisms in a nuanced human-like manner to circumvent traditional bot detection solutions like legacy CAPTCHAs.
They use a combination of dynamic IP addresses, continuous adaptation of attack tactics, and the presence of human-assistants to continue with the attack, convoluting the characteristics displayed by legitimate users. This complexity makes it harder for security teams to define clear patterns for bot detection and tell genuine users from malicious non-human traffic.
The impact of social media scraping on platforms
Social media scraping has far-reaching consequences on platforms. Unauthorized collection of sensitive customer data not only can result in breaches of privacy and erosion of user trust, but also put a strain on the platform's servers, causing performance disruptions, slowdowns, or crashes, which can negatively affect user experience.
Data is at the core of the commercial viability of social media platforms. Web scrapers extract user data, including personal details, contact information, posts, and messages, which can lead to significant data privacy breaches and intellectual property violations when copyrighted content is stolen. Attackers may use stolen data for spamming, phishing, or spreading misinformation, resulting in reputational damage to the platform and reduced user engagement. This theft, exploitation, or manipulation of data can cause financial damage, and lead to deficit in customer trust.
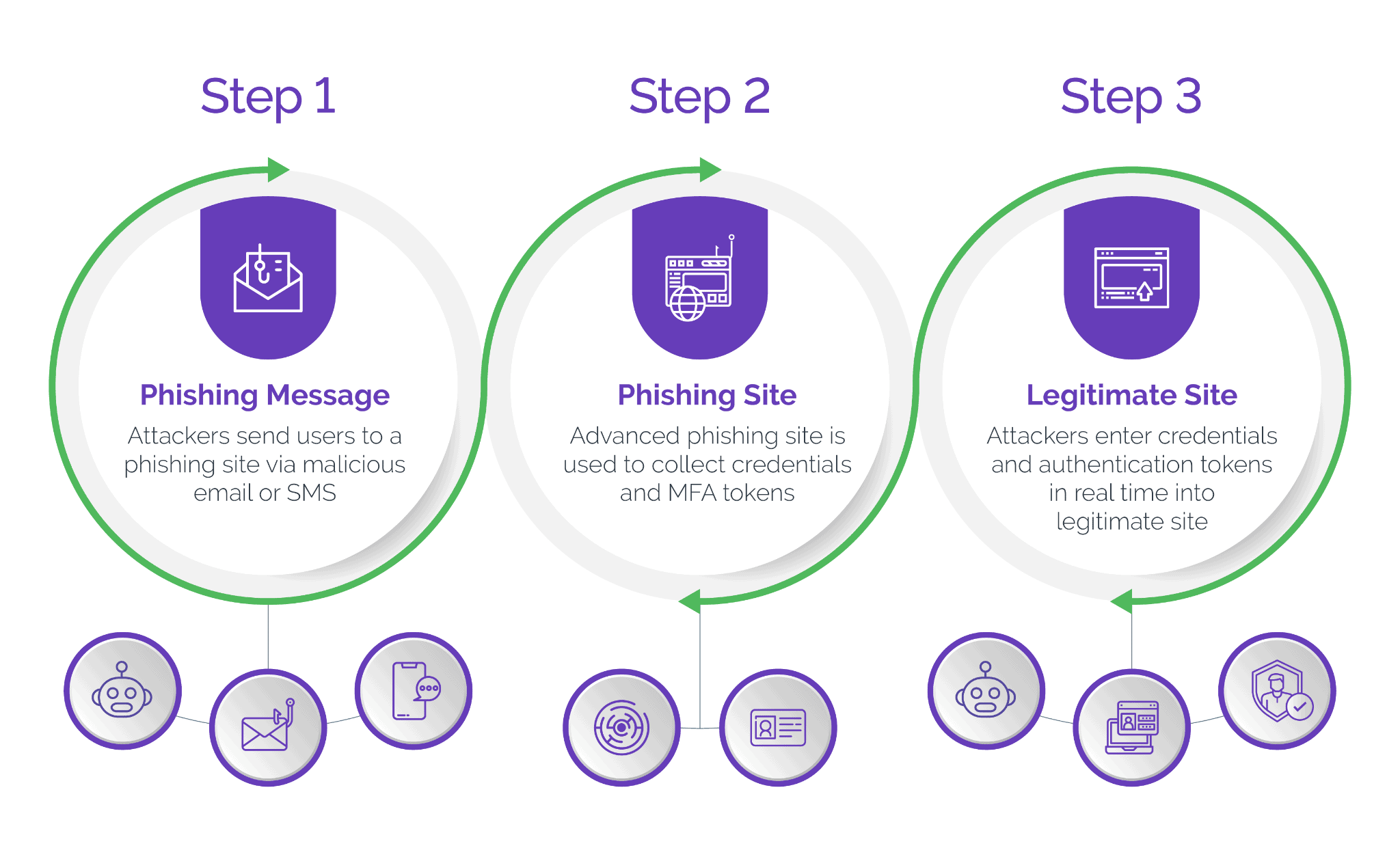
A lot of times attackers use scraped data to create fraudulent accounts or user profiles, which skews the accuracy of user metrics and ad targeting, causing potential revenue loss. This low-quality data, flooding the market due to widespread automated scraping, can diminish the quality of data analytics, distort market insights or competitive analysis, and impact marketing strategies.
It is mandatory for social media platforms to comply with various data protection and privacy laws. Scraping may violate these regulations as well as platform terms of service, exposing social platforms to the risk of account suspension or legal action.
Proactive measures against social media scraping
There are several strategies that social media platforms can implement to prevent scraping, protect valuable data, and maintain integrity of their platforms.
Strengthening security measures to prevent unauthorized access to social media accounts and data should be the first priority. For this, social platforms must enforce strong password policies, enable two-factor or multi-factor authentication, and regularly monitor account activity for any suspicious behavior.
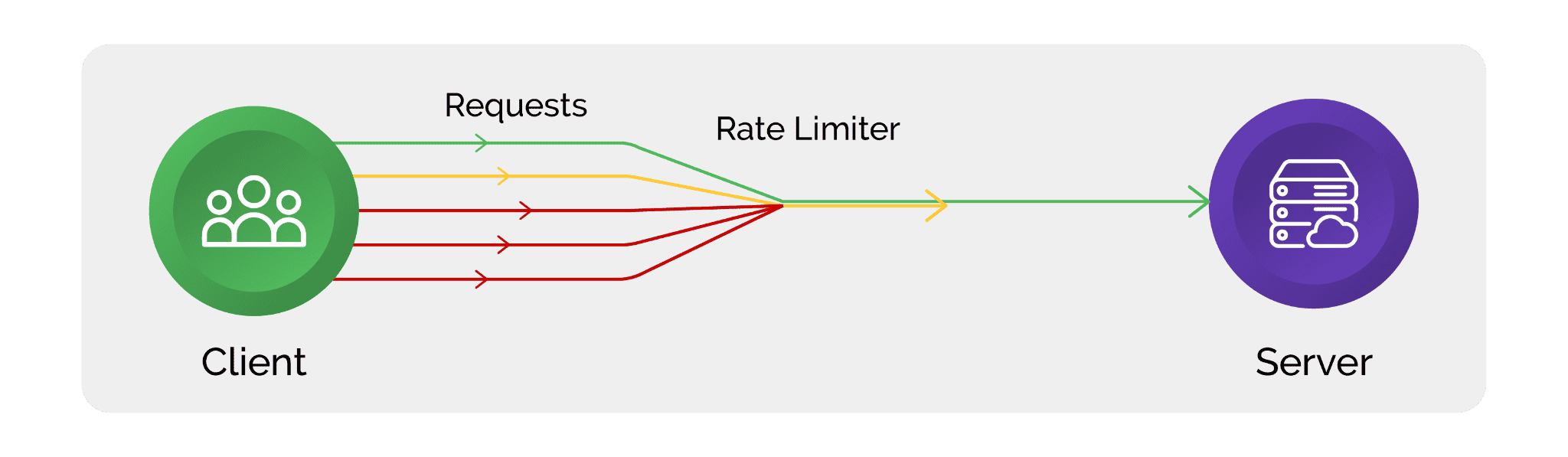
Implementing rate-limiting measures on their APIs will reduce the impact of scraping activities on servers by controlling the volume of requests from a single user or IP address. Further, regular review and updation of platform terms of service to explicitly outline the consequences for violators, such as legal action or account termination, can help prohibit scraping activities.
Identifying signs of social media scraping activities
With regular monitoring and vigilance, social media platforms can identify the signs of scraping activities and take timely corrective actions. Some common signs indicative of a social media scraping attempt include: a sudden spike in traffic or requests from a single IP address; anomalous user behavior, such as irregular patterns in interactions or a high volume of account creations within a short period; and a sudden influx of duplicate or low-quality content.
Implementing robust user access controls
Social media platforms must invest in monitoring tools and services that can detect and mitigate scraping attempts in real-time. This will enable swift response to any unauthorized access attempts or data breaches. Implementing robust access controls may involve several key steps, including:
- Authentication and Authorization: Require users to authenticate themselves before accessing sensitive data or APIs. Implementing strong authentication mechanisms such as two-factor or multi-factor authentication can help validate user identities. Enforce clearly defined access control policies to ensure only authorized users can access data or resources needed for their roles.
- Rate Limiting and Throttling: Limit the number of requests that users can make within a certain time frame with rate limiting and throttling mechanisms. Monitor and analyze request patterns to identify and block suspicious behavior.
- API Key Management: Monitor and track API usage by requiring developers and applications to use unique API keys for accessing APIs and resources. For enhanced API security, enforce usage limits for each API key and revoke access for unauthorized users or applications.
- IP Whitelisting and Blacklisting: Maintain lists of trusted (whitelist) and untrusted (blacklist) IP addresses to control access to resources.
- Monitoring and Logging: Implement comprehensive logging and monitoring systems to log relevant information such as IP addresses, user agents, request timestamps, and response codes for analysis and detecting unusual patterns or spikes in access.
Advanced security technologies to deter social media scrapers
Social media platforms must take proactive measures to go beyond mitigation to deter scraping activities. Leveraging advanced technologies, such as those mentioned below, can be useful in deterring automated scraping:
- Behavioral Biometrics: To analyze user behavior in real-time, detect anomalies, and distinguish between genuine users and scrapers.
- CAPTCHA Challenges: To filter out non-human traffic and verify that the user is a human.
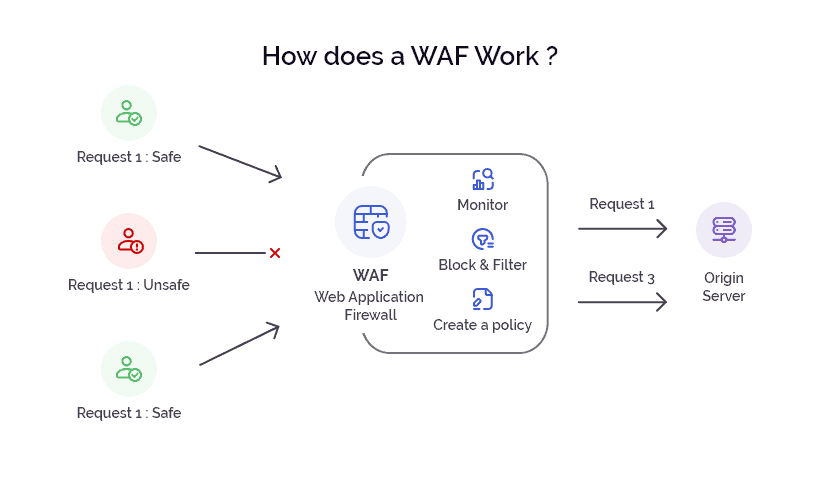
- Web Application Firewalls (WAF): To block suspicious requests in real-time by analyzing incoming traffic, identifying bot behavior, and applying rulesets.
- Device Fingerprinting: To analyze device attributes such as user-agent strings, screen resolution, and browser plugins, for unique identification, tracking of devices accessing web resources, and blocking scrapers with masked identities.
- Honeypots and Decoy Data: To lure scrapers into accessing fake or irrelevant information, block scraping bots, and protect actual data from unauthorized access.
- Client-Side Protection: To verify the integrity of user interactions and prevent automated scraping bots from accessing web pages, using anti-scraping JavaScript challenges or token-based authentication mechanisms.
- Bot Management Platforms: To comprehensively detect, mitigate, and manage scraping activities.
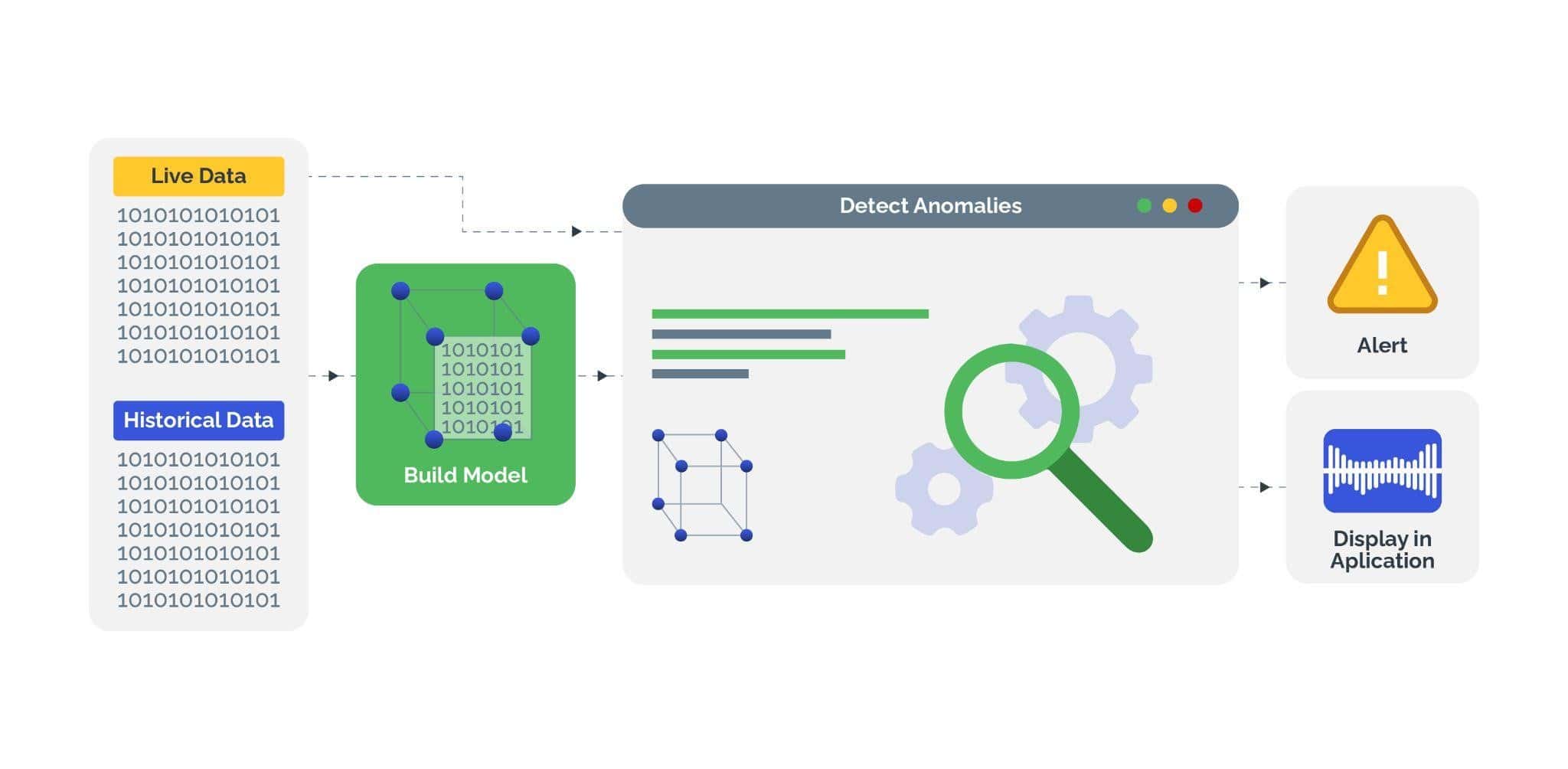
- AI and Machine Learning: To detect anomalies and recognize abnormal behavior patterns using data analysis, in real-time.
Best practices for protecting data and user accounts
Social media platforms can make use of some best practices to protect data and ensure user account security. These include implementing robust security measures such as encryption for data at rest and in transit, strict access controls to limit data access to authorized users, regular auditing and monitoring for security vulnerabilities, and providing users with transparent privacy settings and controls.
Platforms should conduct awareness campaigns to educate users about potential risks of social media scraping and encourage the use of strong passwords and multi-factor authentication.
Social media platforms must comply with relevant data protection regulations and maintain open communication with users regarding data privacy policies and updates.
Bot management solutions
Using smart bot management solutions, such as Arkose Bot Manager, social media platforms can effectively prevent data scraping and protect user accounts and integrity of their services. These solutions leverage a host of advanced technologies such as behavior analysis, challenge-response authentication, device fingerprinting, and more to accurately detect and block automated bot traffic and mitigate the impact of scraping activities.
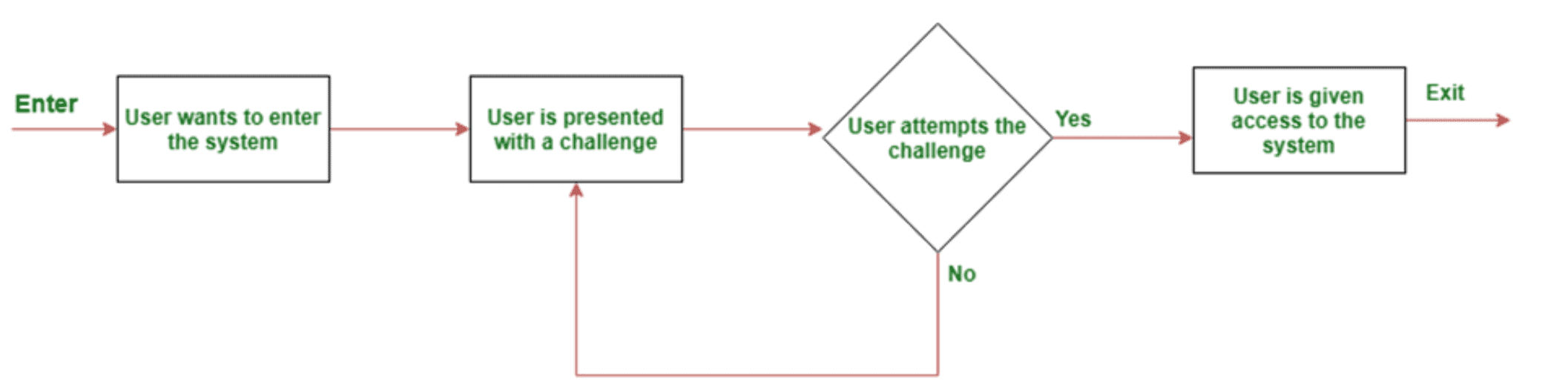
Regular audits and monitoring for vulnerabilities
By regularly auditing and monitoring for vulnerabilities, social media platforms can proactively identify and mitigate weaknesses before attackers exploit them. Social platforms must consider implementing automated scanning tools and conducting security assessments to stay ahead of emerging threats.
Equipping security teams with relevant knowledge and tools on cybersecurity hygiene
Security hygiene is crucial for social media sites to maintain a strong defense against threats. Training security teams on password security, phishing awareness, and secure coding practices, can empower them to better recognize and respond to potential scraping attempts. It is also essential to equip security teams with relevant knowledge and skills needed to protect the social platform’s infrastructure, data, and users’ account security.
Collaborating with industry partners and law enforcement
Collaboration is a powerful strategy for deterring social media scraping. When social media platforms work collectively, they are able to develop more effective countermeasures against automated scraping activities. Social media platforms must also work closely with regulators and law enforcement agencies to deter scrapers with potential legal action.
Sharing intelligence and best practices
By sharing intelligence and best practices, social media platforms can build a more robust defense against scraping activities. Exchanging information on emerging threats, successful mitigation strategies, and new technologies, can help social platforms adapt to the known and emerging threats, improve resilience of individual platforms, and contribute to the overall security of the social media ecosystem.
Legal recourse and collaborative defense strategies
Legal recourse and collaborative defense strategies can play a crucial role in combating social media scraping. Social platforms must leverage the legal frameworks to hold the perpetrators accountable and take action against scrapers. This will help deter malicious actors and create a unified front against scraping threats.
Developing an effective response plan for social media scraping incidents
To ensure readiness for any eventuality, social media platforms must develop a response plan. This may require identifying key stakeholders, establishing communication protocols, and outlining escalation procedures. The plan should clearly establish the steps for detecting and verifying scraping activity, assessing the impact on data integrity and user privacy, and coordinating with legal and technical teams for threat mitigation. Social platforms must test the response plan with regular training and exercises to ensure readiness for an effective response to scraping incidents and minimize their impact.
Potential immediate actions and long-term strategies
A holistic response to social media scraping incidents include immediate actions and a long-term strategy. Immediate actions may include temporary blockage of suspicious IP addresses, deploying CAPTCHA challenges, and enhancing monitoring to detect further scraping attempts.
To adapt to the evolving threats, social media platforms must strive to strengthen access controls, implement advanced bot protection software, and regularly update security measures. Additionally, collaboration with peers and law enforcement agencies can help develop sustainable solutions to comprehensively combat scraping in the long term.
Communication during and after an incident
In case of a scraping incident, the social media platform must immediately inform the affected users, providing details about the nature of the scraping activity, potential impacts, and measures taken to mitigate the situation. The platform should keep the users informed of the ongoing investigation, remediation efforts, and the steps users can take to protect their accounts and data, in a transparent and timely manner.
Want to know more about how to keep bots from scraping your social media platform? Check out our blog post Stomping Out Social Media Scraping.








