What Is an Account Takeover Attack?
An attack where a bad actor uses stolen credentials to gain unauthorized access to a user's digital account is called an account takeover attack, or simply ATO.
Once an account is compromised, the attacker can control the account and use it for numerous criminal activities such as data theft, phishing, identity fraud, unauthorized transactions, opening new lines of credit, card-not-present fraud, money laundering, and so forth.
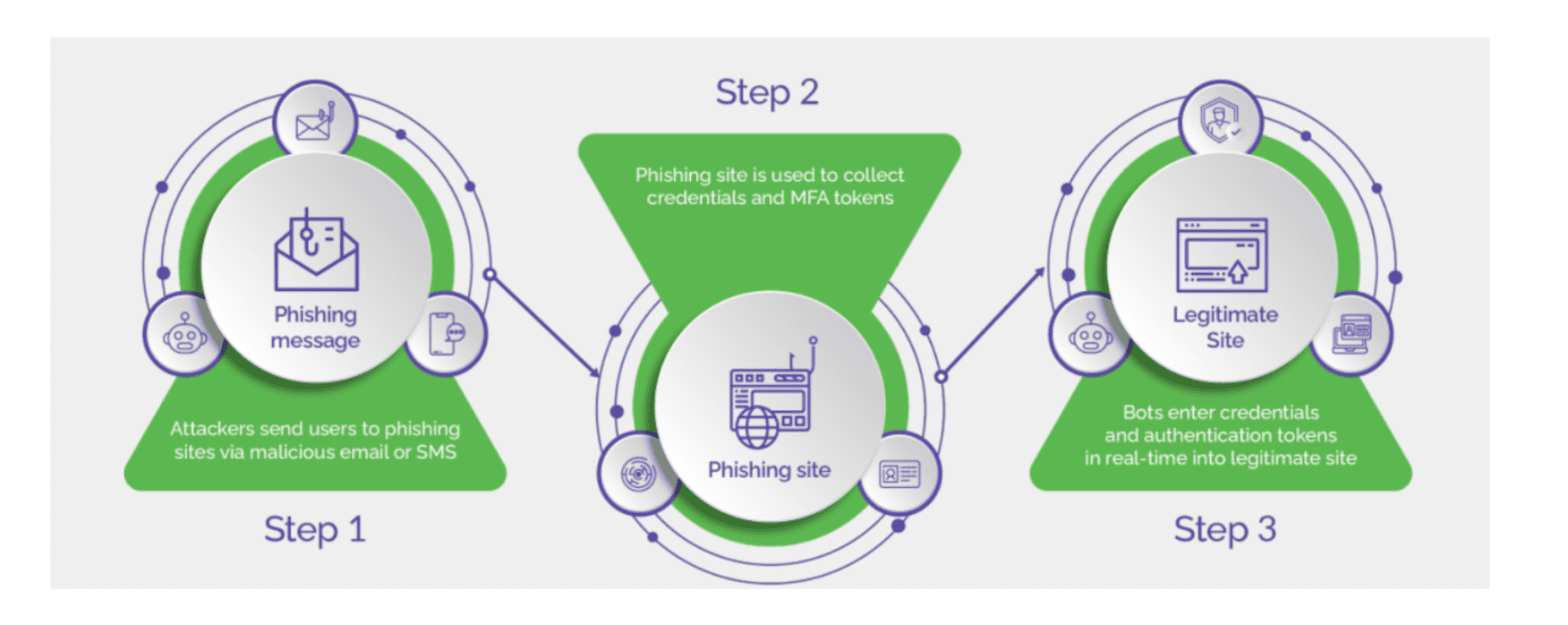
Steps in an Account Takeover Attack
Cybercriminals use sophisticated tools and tactics to carry out these attacks, often following this pattern:
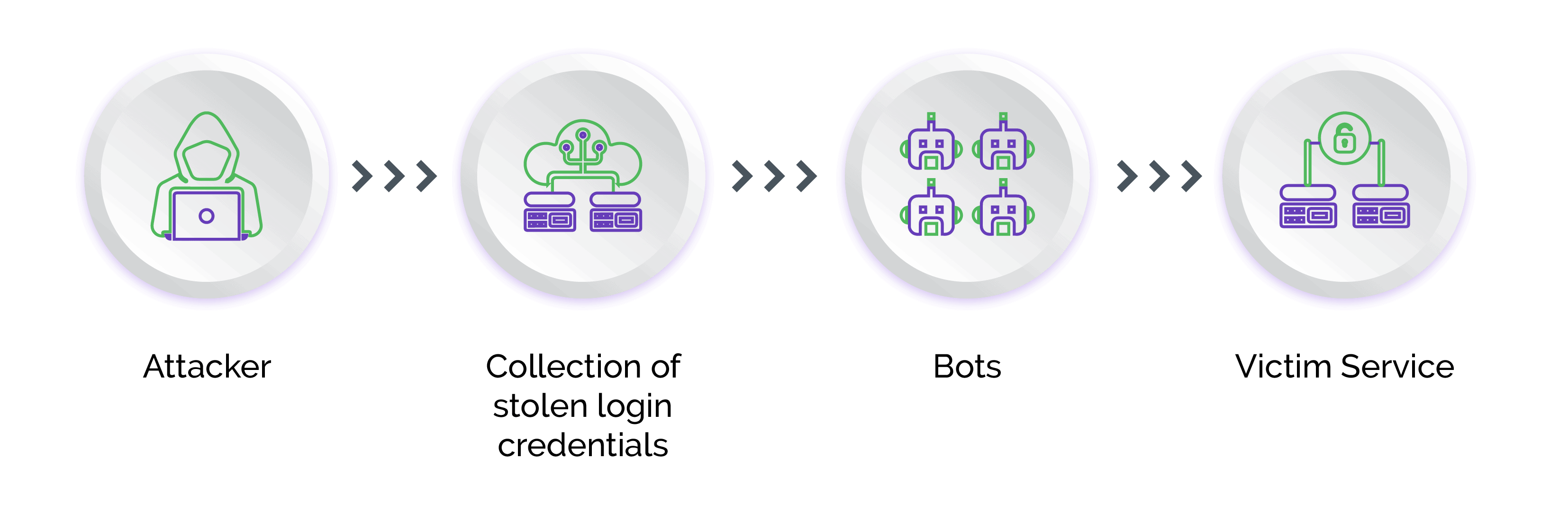
- Credential Theft: Attackers obtain users’ login credentials using methods including data breaches, phishing, scraping, keyloggers, or malware.
- Credential Abuse: On acquiring the user’s account credentials, attackers try to log in to the target accounts. They use bots to achieve scale and speed in matching usernames with passwords.
- Account Access: Successful login attempts allow attackers to gain unauthorized access to the user accounts and use the compromised attack for numerous criminal activities.
- Maintaining Access: To ensure long-term use of the compromised account, attackers may change account recovery settings, manipulate contact information, add their own contact details to lock the genuine users out, or install backdoors for future access.
- Monetization: Attackers may choose to sell databases of harvested credentials as is or refine them for valid username-password combinations to resell at a premium. Attackers may also use the stolen details and compromised accounts themselves for various malicious activities.
Impact of ATO Attacks
Account takeover attacks can have far-reaching consequences on businesses and consumers. Affected users not only face financial losses but also identity theft and mental trauma trying to restore their digital identities.
Businesses face financial, operational, and reputational damages that can adversely impact revenue and potential growth. They incur additional costs on remediation, account restoration, refunds, burden on customer support, and investment in security mechanisms, while facing operational disruption. Because account takeover attacks erode customer trust, businesses may face difficulty retaining and acquiring customers, causing long-term business losses.
Why Banks and Financial Institutions are Prime Targets for Account Takeover Attacks
The sensitive financial and personal information of users and monetary assets that banks and financial institutions possess make them prime targets for ATOs. A successful takeover of a financial account can provide attackers with substantial monetary gains, which drives attackers to focus on attacking banks and financial institutions.
As banks and financial institutions have adopted digitization to deliver a variety of financial services digitally, the number of touchpoints has increased. This widened attack surface provides attackers with numerous opportunities to exploit vulnerabilities. Furthermore, being a critical component of the economy, breaching banks and financial institutions allows attackers to gain unauthorized access, manipulate transactions, and cause instability in the overall financial system.
Reasons ATO Attacks Are on the Rise
In recent years, account takeover attacks have increased manifold. There are several factors contributing to their increasing prevalence. These include:
- Increased Digitalization: The great digital shift and growing dependence on digital platforms has expanded the attack surface, enabling attackers to exploit user touchpoints for vulnerabilities and take over user accounts.
- Data Breaches: The increasing frequency and scale of data breaches have exposed vast amounts of user credentials that can be stolen to fuel attacks across various platforms.
- Use of Bots: Bots facilitate a bank account takeover attack through phishing, malware attacks, automated credential stuffing attacks, and manipulating transactions. Advanced bots can mimic humans to interact with defense mechanisms and bypass them with ease. Given the speed and efficiency with which bot traffic executes automated attacks, it becomes difficult for traditional security measures to detect and prevent automated bot attacks.
- Sophisticated Attack Techniques: Using continually evolving attack tactics and spoofing techniques, bad actors can launch complex and targeted attacks without getting detected.
- Credential Sharing and Reuse: Often, consumers create weak passwords, recycle and reuse same passwords for digital accounts across digital platforms. If attackers are able to guess the passwords and successfully compromise one account, they can easily take over other accounts.
- Inadequate Authentication Practices: Legacy or obsolete authentication methods increase the risk of account takeover, such as the sole reliance on passwords or lack of multi-factor authentication (MFA).
- Monetary Motivation: The underlying motivation for an account takeover attack is financial gain through fraudulent transactions, stealing financial information, ransom demands, money laundering, and exploiting loyalty programs, among others.
- Insider Threats: In some cases, employees or individuals with insider knowledge can facilitate compromise of user accounts and sensitive information.
Account Takeover Attacks Are Challenging to Detect
ATOs are a growing challenge for businesses across industries as they are difficult to detect due to their evolving and sophisticated nature. Attackers use several techniques like phishing, social engineering, and malware for credential harvesting, without raising suspicion.
The easy availability of commoditized tools enables attackers to perform credential stuffing at scale and make numerous login attempts without triggering immediate account lockouts. By mimicking legitimate user behavior and using evasive techniques such as proxy servers, virtual private networks (VPNs), and other anonymization techniques, attackers can obfuscate their identity and location. This makes it harder for security teams to trace and block account takeover attacks.
Often, attackers wait for opportune moments, such as periods of low-traffic or less vigilant monitoring to conduct unauthorized activities. This strategic timing reduces the possibility of immediate detection and allows attackers enough time to exploit vulnerabilities and compromise accounts.
Telltales of a Potential ATO Attack
Although it can be difficult to identify account takeover attacks, there are definitive telltales that indicate account takeover attempts. Businesses must ensure continuous monitoring to keep an eye out for common indicators such as:
- Multiple failed login attempts, logins from unfamiliar locations, or sudden changes in login times
- Unexpected password changes without the users’ knowledge or consent
- Logins from unfamiliar devices or IP addresses, especially those linked with previous malicious activity or high-risk regions
- Unusual account actions, such as changes in account settings, addition of new contacts, or unexpected financial transactions
- A sudden increase in failed login attempts may suggest a brute force or credential stuffing attack
- Unexpected password reset requests, changes in email settings, or phishing attempts
- Simultaneous logins from geographically distant locations within a short timeframe
Strategies To Effectively Prevent Account Takeovers
Successful account takeover attacks can severely impact businesses and consumers. It is therefore essential that businesses take proactive measures. Organizations must consider implementing a comprehensive set of strategies to address vulnerabilities at various touchpoints. A strategic account takeover protection plan should be a key component of the overall security posture to ensure user account security. Some key strategies are as listed below:
- Bot Detection and Mitigation: Cut attacks off before they can happen by proactively detecting malicious bots, distinguishing them from legitimate users and deploying countermeasures to prevent unauthorized access.
- Multi-Factor Authentication (MFA): Reduce the risk of ATO attacks by adding an additional layer of security. Request users to provide multiple forms of identification such as password, OTP or code, or biometrics.
- Behavioral Analytics: Implement behavioral biometrics tools to analyze user behavior and identify deviations from specified standard patterns.
- Continuous Monitoring: Use advanced monitoring systems for anomaly detection such as unusual login patterns, changes in account settings, or any other unusual activity, and trigger alerts.
- Strong Passwords: Encourage users to create strong and unique passwords to prevent credential abuse by reusing passwords.
- Account Suspension: Temporarily suspend customer accounts after a certain number of failed login attempts to mitigate the risk of brute-force attacks.
- IP Whitelisting: Implement IP whitelisting to restrict access to user accounts from specific IP addresses or ranges.
- Secure Password Recovery Processes: Secure the password recovery or reset processes with additional verification steps to prevent attackers from resetting passwords or account takeover.
- Security Audits: Conduct regular security audits and vulnerability assessments. Identify and address potential weaknesses in systems and applications. Review and update security policies, configurations, and access controls.
- Incident Response Plan: Create an incident response plan for swift and effective response to a security incident, as well as to improve future defenses.
- User Awareness: Educate users about threats such as phishing attacks and social engineering that attackers employ to extract information. Communicate security best practices and train users to recognize and report suspicious activities.
Prevent Account Takeover Attacks with Arkose Labs
Arkose Labs is a trusted partner for comprehensive protection against ATO. Using a combination of the latest technologies, machine learning, and real-time risk-based authentication, Arkose Labs provides definitive protection against human and bot-driven attacks.
An adaptive approach dynamically assesses the risk associated with each incoming user and engages risky users with challenge-response authentication. Instead of blocking any user, Arkose Labs serves Arkose MatchKey challenges to test the legitimacy of the users. Good users generally do not encounter these challenges. In the event they do, they find it fun to solve the challenges and move ahead with their digital journeys.

On the other hand, automated scripts and bots of various advancement levels instantly fail. This is because Arkose MatchKey challenges are designed to be resilient to the most modern optical vision technologies, which makes them the best CAPTCHA challenges on the market today. Often, when deterred, bots hand over the attack baton to human click-farms. These malicious humans continue to face several variations of Arkose MatchKey challenges that not only keep increasing in volumes but also complexity.
This continuous obstruction delays execution of attack and also increases the investment in terms of time, effort, and resources. Even if attackers tried to create automatic solvers for Arkose MatchKey challenges, they would spend disproportionate amounts of time and still fail due to the sheer number of variations of every single challenge. Ultimately, with no financial returns in sight, frustrated attackers give up and abandon the attack for good.
Additionally, Arkose Labs supports its partners with 24X7 SOC support, data-backed insights, and the latest threat intelligence from its global network of clients to ensure businesses can mitigate any risks as soon as they are identified. As a result, Arkose Labs is a preferred partner for leading global businesses looking to protect their consumers from the onslaught of cyberthreats, without in any way degrading the user experience for genuine users.







